Example: Onboard a Windows server with subscribers
This example describes how to install the subscriber scenario component, onboard a Windows server and configure the subscribers so they receive the new password when it is randomized.
Install the components
The following components are required for this example:
RefBuild.pam_team_management.
Scenario.pam_system_type_vault.
Scenario.pam_subscriber_validation
Scenario.pam_system_type_winnt
Create and set up a team
To create and set up a team:
Create a team administrator.
Log in as the administrator to create the team.
Add users to the groups in the team
Steps are detailed below.
Click Manage the system > Policies > User classes .
Select the PAM_TEAM_ADMINS.
Click the Explicit users tab.
Click Select .
Search and select a user.
Click Add.
This user can now log in and create, delete and manage teams.
Log into Front-end (PSF) as the team administrator.
Click Manage Resources.
The page is displayed.
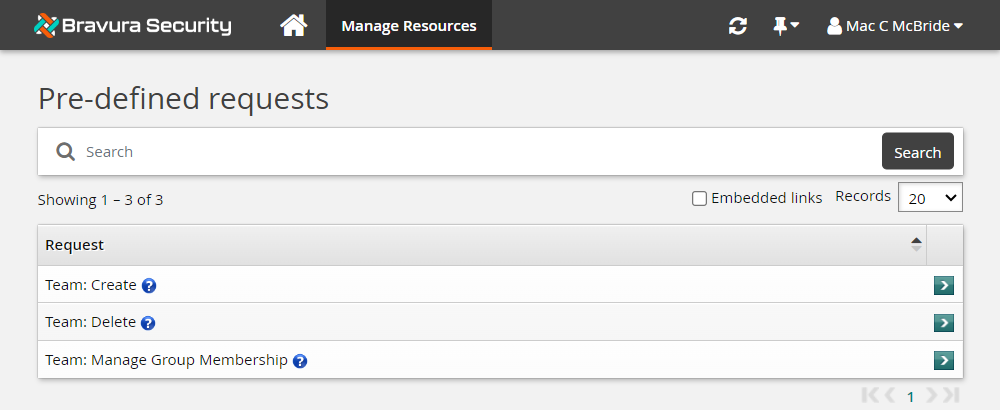
The team administrator can create, delete and manage teams using these pre-defined requests.
Click Team: Create.
Bravura Security Fabric displays the team creation wizard
Enter the following information:
Team Name: Vault-Management-Team
Team Description: Team to manage system vault
Click Next .
Add seven groups. Use the ”More” icon to add more team name fields to the list.
Team Trustees Users who can make team management requests.
Account Trustees Users who can make account management requests (onboard accounts).
Approvers Users who allow or disallow access requests.
Auto Approved Users who can check-out access to systems and accounts without making an access request.
Requesters Users who can make access requests.
Credential_Managers Users who can override or randomize the stored password on a checked-out account.
System Trustee Users who can make system management requests (onboard systems).
Subscriber Trustees Users who can make subscriber validation requests.
Click Next and add team descriptions.
Click Next .
Assign privileges to the team groups:
Team Trustees Team trustees
Account Trustees Account trustees
Approvers Approvers
Auto Approved Auto_Approved and requesters
Requesters Requesters
Credential Managers Requesters and Credential_manager
System Trustees System trustees
Vault Trustees Vault trustees
Subscriber Trustees Subsriber trustees
The Credential_Manager privilege allows a user to override or randomize the stored password on a checked-out account.
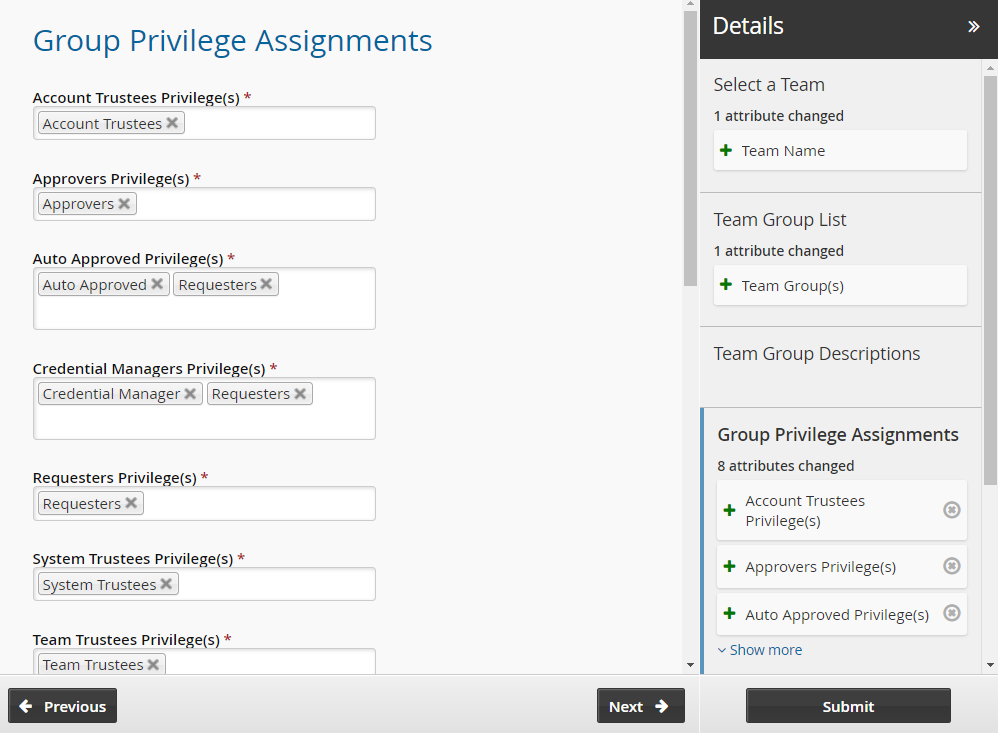
Click Next .
Set the initial team trustees for the new team. There must be at least one team trustee to create a team.
Click Submit.
Bravura Security Fabric notifies authorizers to review the request if required.
Click the View request link at the top of the page to view the status of the request.
Once the request has been approved, the team will be configured.
Log into Front-end (PSF) as a team trustee.
From the home page, click Manage resources.
Click Team: Manage Group Membership.
Select the Vault-Team.
Click Next .
Select the Account Trustees, Approvers, Auto Approved, Requesters, System Trustees, Vault Trustees, Credential Managers and Team Trustees groups.
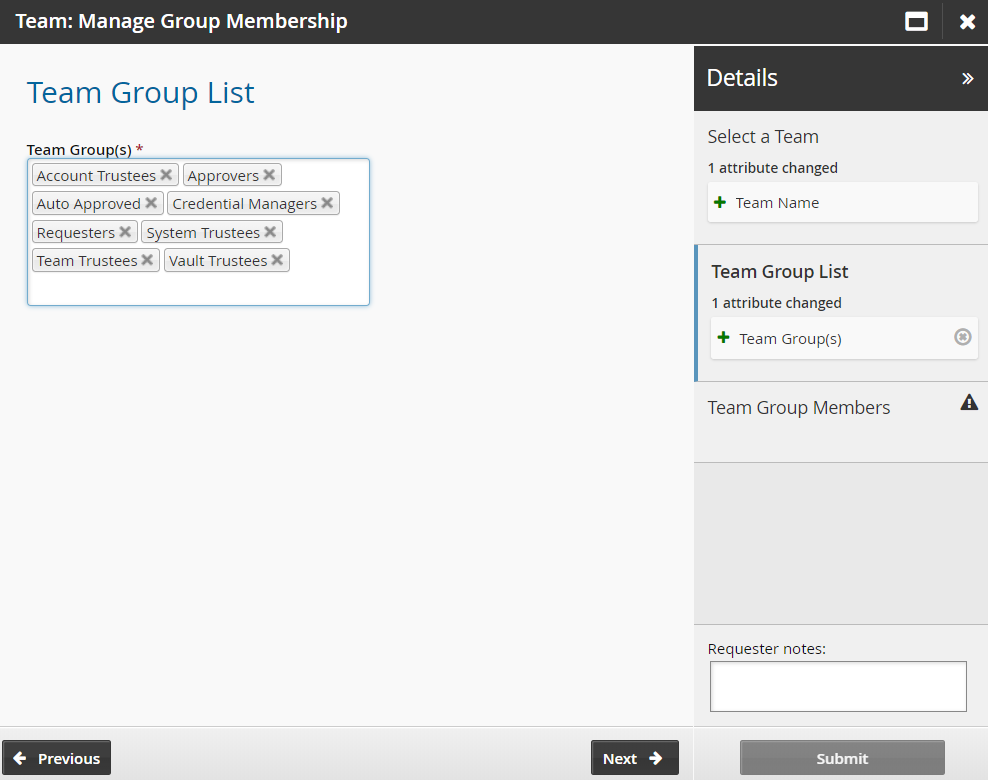
Click Next .
Add members to each team group.
Click Submit.
Bravura Security Fabric notifies authorizers to review the request if required.
Click the View request link at the top of the page to view the status of the request.
Once submitted and approved, the group’s membership will be updated to include the selected users.
Onboard the Windows system
Log into Front-end (PSF) as the system trustee for the Windows system team.
Click Manage Resources.
The Pre-defined requests page is displayed.
Click System: Onboard.
Select the Windows Server system type from the drop down menu.
Click Next .
Enter the System FQDN.
If the Windows system is not on the domain use <hostname> .local
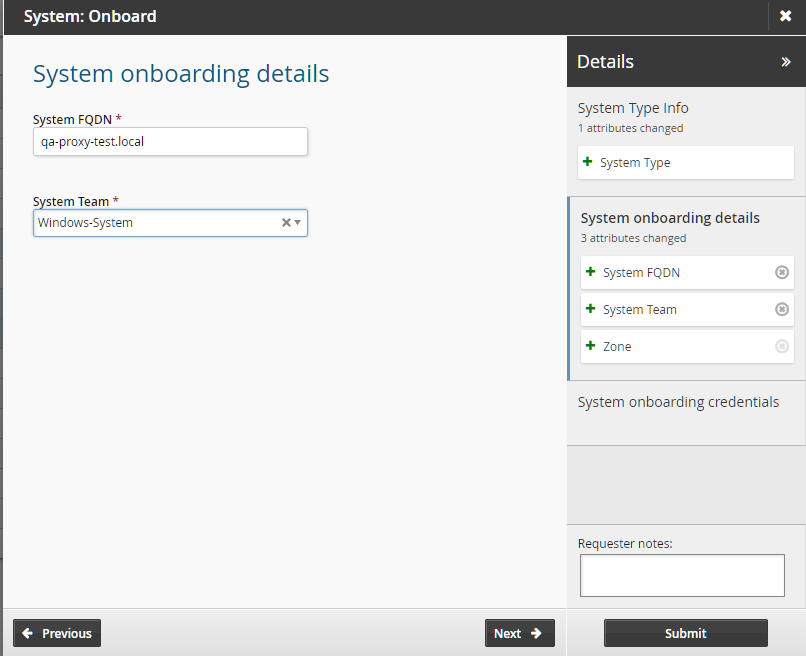
Select the Windows system team to manage the system.
Click Next
Enter the system credentials.
Click Submit.
Bravura Security Fabric notifies authorizers to review the request if required.
Click the View request link at the top of the page to view the status of the request.
Once the request has been approved, trustees can manage accounts on this system.
Set discovery options
Log into Front-end (PSF) as a superuser.
Click Manage the system > Resources > Target systems > Automatically discovered .
Select the Windows system you recently onboarded.
Click the Discovery options tab.
Select the following depending on what subscribers you expect to manage:
Link accounts on this target system to subscribers
Load scheduled task subscribers
Load service manager subscribers
Load IIS manager subscribers
Load DCOM manager subscribers
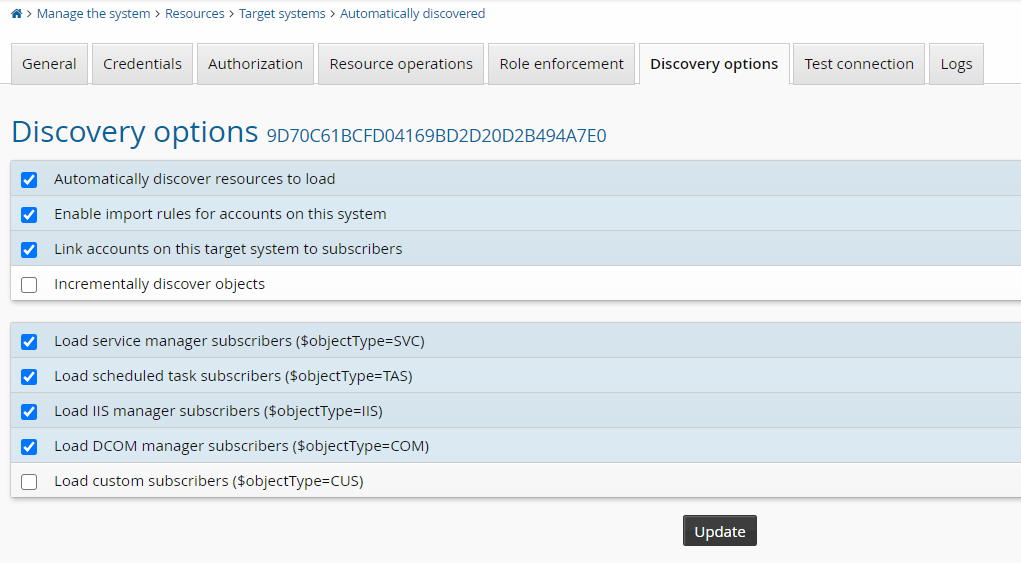
Click Update.
Execute Auto discovery.
Onboard Windows service account
Ensure the subscribers have been set up and discovered before onboarding the account. For example; your scheduled tasks and services set to use a managed account and auto discovery is ran to discover those accounts (subscribers).
Log into Front-end (PSF) as the account trustee for the windows system team.
Click Manage Resources.
Click Account: Onboard.
Select the service account to be managed by the Windows system team
Click Next .
Select the standard policy as the Managed System Policy ID.
Click Next .
Select the Windows system team as the Account Team .
Click Next .
Click Next .
Click Submit.
Bravura Security Fabric enters the request into the authorization workflow.
As a superuser, execute auto discovery to generate subscriber validation requests.
Log into Front-end (PSF) as a subscriber trustee for the windows system team.
Click There is 1 request(s) awaiting your approval link at the top of the page.
Select the request from the Results panel .
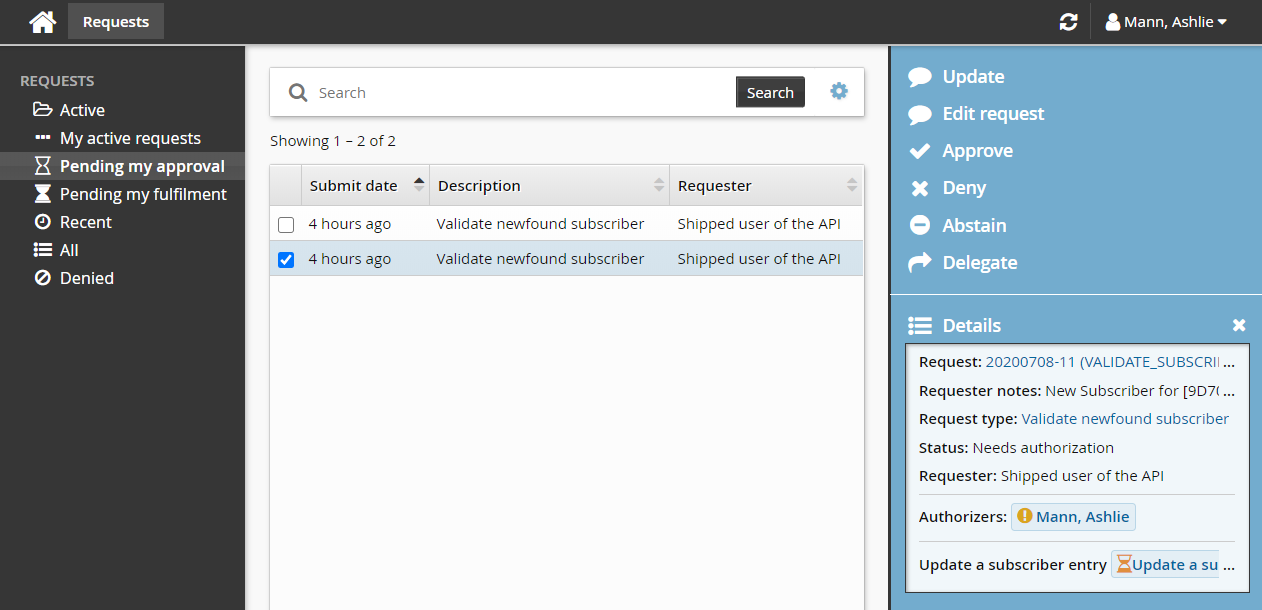
Click Edit request.
Set Notify subscriber of randomization to a value:
After randomizing
Before and after randomizing
Before randomizing
No Notification
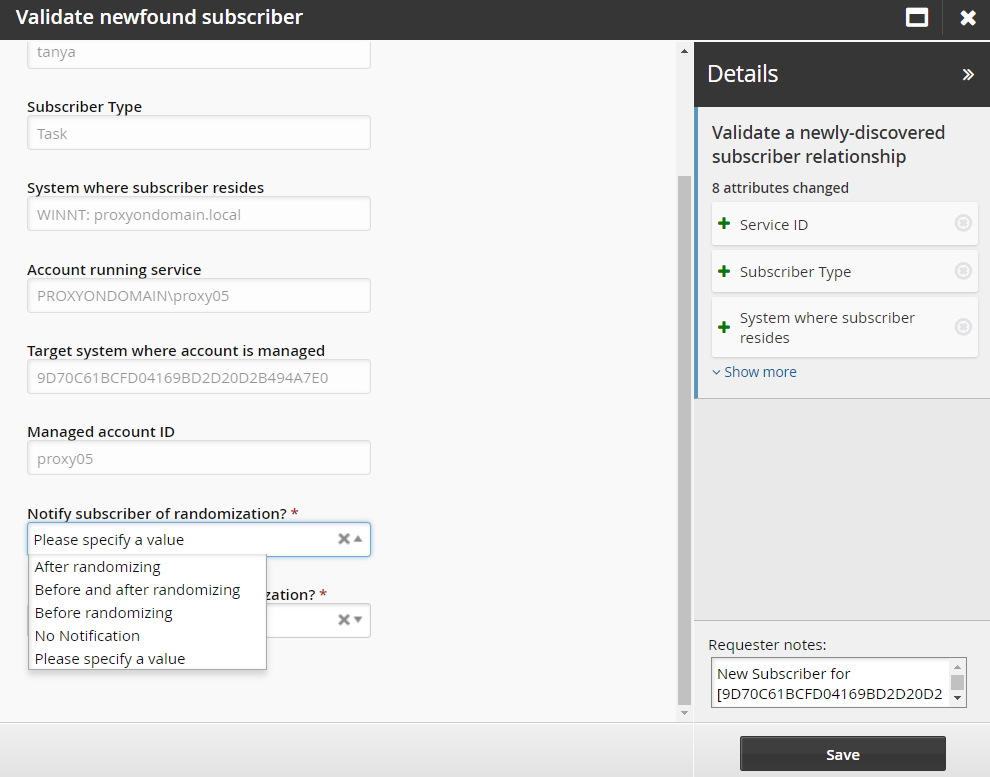
Set Restart subscriber after randomization to either Yes or No.
Restarting may not be needed for large, slow, heavy subscribers like SQLserver; the notification (changing the configured account password) is enough, as the service account password is used only when the service starts up. However, tasks or services which use the service account to run several operations which require login, would lock the service account if they use the old password several times quickly, so they have to be restarted.
Click Save.
Approve the request.
The Deny option is not valid for this type of request. If you do not want to send notifications before or after randomizing, update the request with Notify subscriber of randomization set to "No notification".
Manually randomize the password for the service account.
The password orchestration is now successfully set up.