Example: Integrate with an Okta IdP
Requirement
Organizations that use Okta Single Sign-On solution to leverage federated authentication require Bravura Security Fabric to authenticate with their current IdP solution.
See Okta integration strategy: SAML or API for information about SAML versus API integration.
Solution
Bravura Security Fabric can be configured to operate as a SAML v2 Service Provider, allowing it to integrate with Okta Single Sign-On IdP to authenticate its users. Once authenticated with the IdP, or even before authenticating with the IdP, additional authentication chains may or may not be run.
Bravura Security Fabric can be configured to authenticate users directly against Okta by redirecting them to the Okta Sign-In page. When this method is used, the authentication requirements for the authenticating application are configured within Okta.
Prepare Bravura Security Fabric as a service provider
Install Scenario.hid_authchain_saml_sp component to prepare Bravura Security Fabric as an SP.
Prepare Okta
Steps are subject to change; please refer to the official Okta documentation if there are any discrepancies.
To configure Okta to allow integration with Bravura Security Fabric:
Sign in to your Okta instance as a system administrator.
Navigate to the Administrator Dashboard.
On the left navigation pane, expand Applications, then click on Applications.
This pane may be hidden unless you click on the Menu icon on the top left.
Click Create App Integration.
For Sign-in method, select SAML 2.0.
Click Next .
Configure General Settings for the SAML Integration:
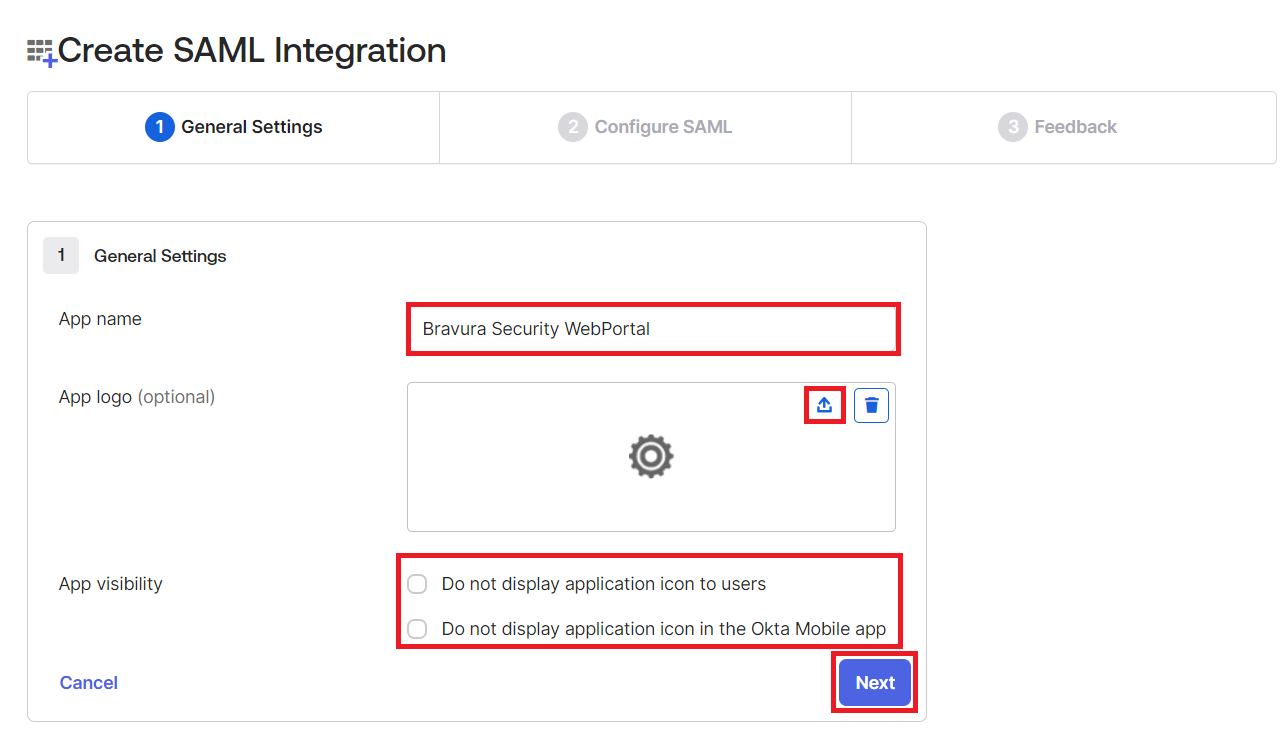
Give your new application a name; for example Bravura Security WebPortal.
Select a logo for the application.
Configure the application visibility settings.
Click Next .
Configure SAML Settings for SAML integration:
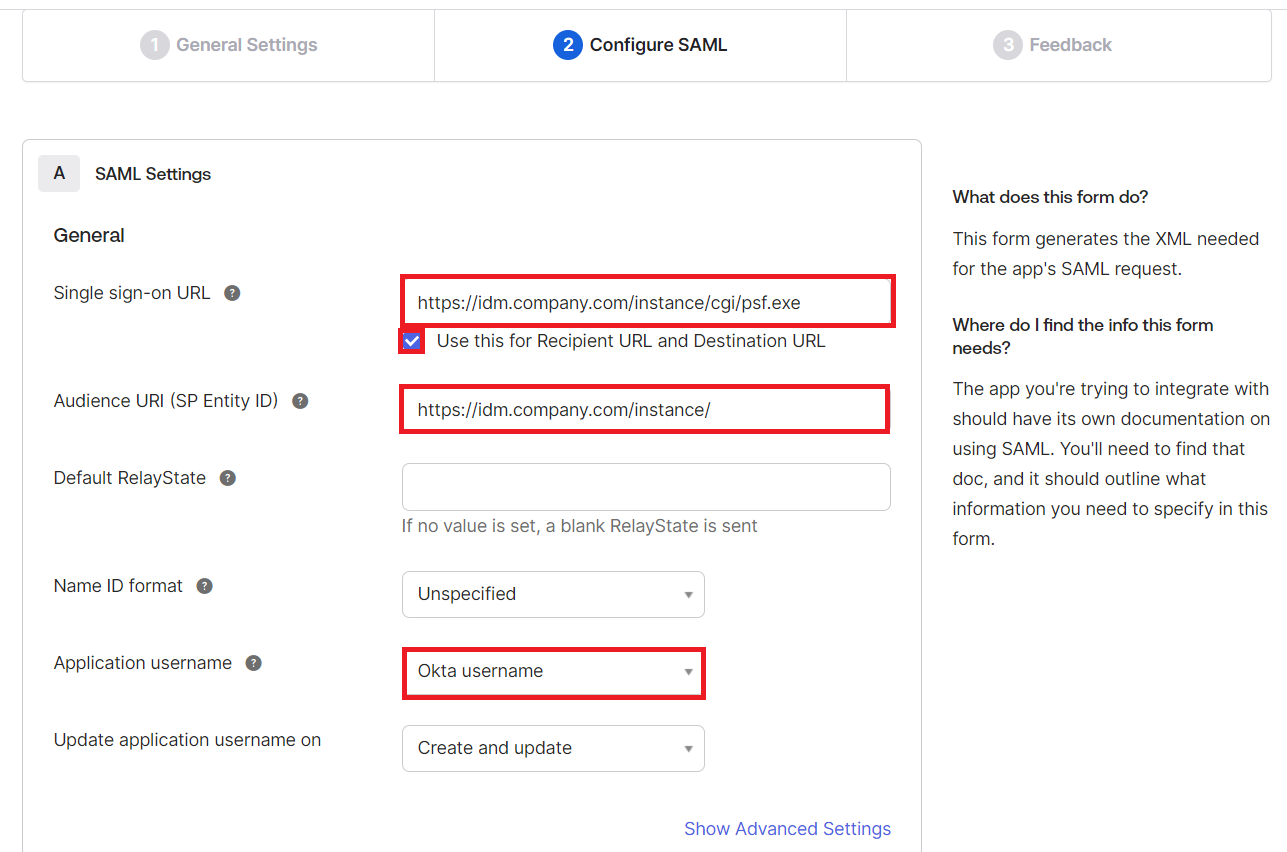
Set the Single-Sign-On URL for the Bravura Security Fabric SP, in the format:
https://<bravura-fabric-server>/<instancename>/cgi/psf.exe.For example
https://idm.company.com/instance/cgi/psf.exeEnsure that Use this for Recipient URL and Destination URL is enabled.
Set the Audience URI (SP Entity ID) for the Bravura Security Fabric SP, in the format:
https://<bravura-fabric-server>/<instancename>/.For example
https://idm.company.com/instance/.Leave the Default RelayState blank.
Set Name ID format to "Unspecified".
Map profile attributes between Okta and Bravura Security Fabric users.
In order for Okta to authenticate Bravura Security Fabric users, it needs to have a means of associating Bravura Security Fabric users to existing Okta users. This is done via attribute mapping, where Okta will compare the two profiles’ attributes to see if they match. In the Application username field, you must select an attribute which can be mapped to Bravura Security Fabric user profiles. This is used to link Okta and Bravura Security Fabric user profiles.
If the Okta username matches the Bravura Security Profile name then select Okta username.
Otherwise, an attribute within Okta can be used to match either the Bravura Security Fabric user profile name, or a user attribute within Bravura Security Fabric . You will need to mirror these attribute mappings when you configure the authentication chain in Bravura Security Fabric .
Warning
It is important to ensure that only a single profile within Bravura Security Fabric matches the selected value. Ensure that the attributes selected will be an exact match.
The attribute mapping between Okta and Bravura Security Fabric must be 1:1. If there are multiple attributes configured in Okta under Application username, Bravura Security Fabric acting as an SP will not be able to distinguish between them and will redirect back to Okta, which combined with active Okta SSO is likely to cause an infinite redirect loop.
Click Show Advanced Settings.
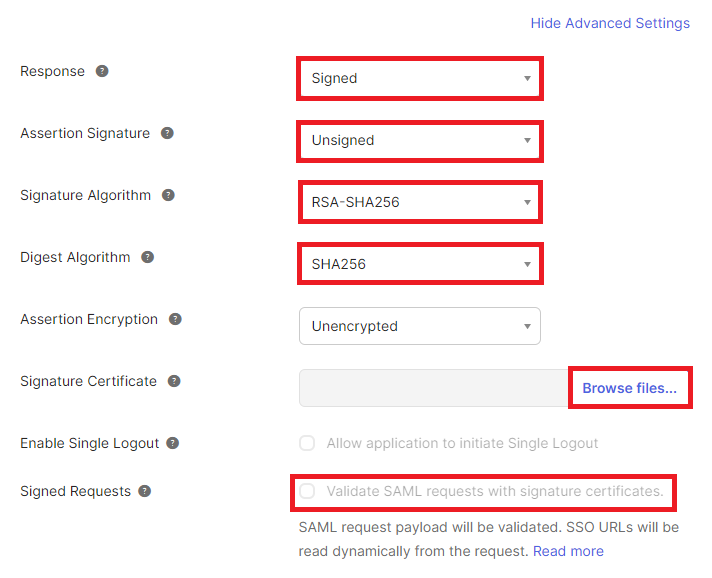
Choose whether the Response or Assertion Signature is "Signed":
You can choose to have either the response or the assertion be signed by the IDP, but not both.
You can choose to have both the response and the assertion be unsigned, however this not recommended.
Choose the Signature Algorithm used to digitally sign the response or assertion. By default, RSA-SHA256 will be used.
Ensure the Digest Algorithm matches the one specified for the Signature Algorithm.
Leave Assertion Encryption as "Unencrypted".
If you want SAML assertions to be assigned and have configured Bravura Security Fabric to require SAML assertions to be assigned (AuthRequest setting in SAML_SP) click Browse files… for Signature Certificate and set it to public.cer , located in <instancedir>\sp
The directory may appear empty but the certificate is present; ensure that All Files are displayed instead of Custom Files.
Leave Enable Single Logout unchecked.
Choose whether Signed Requests will be validated.
Leave all other options untouched and click Next .
Fill out the Feedback section, and click Finish.
Click on Assignments.
Specify users or groups who will access this application.
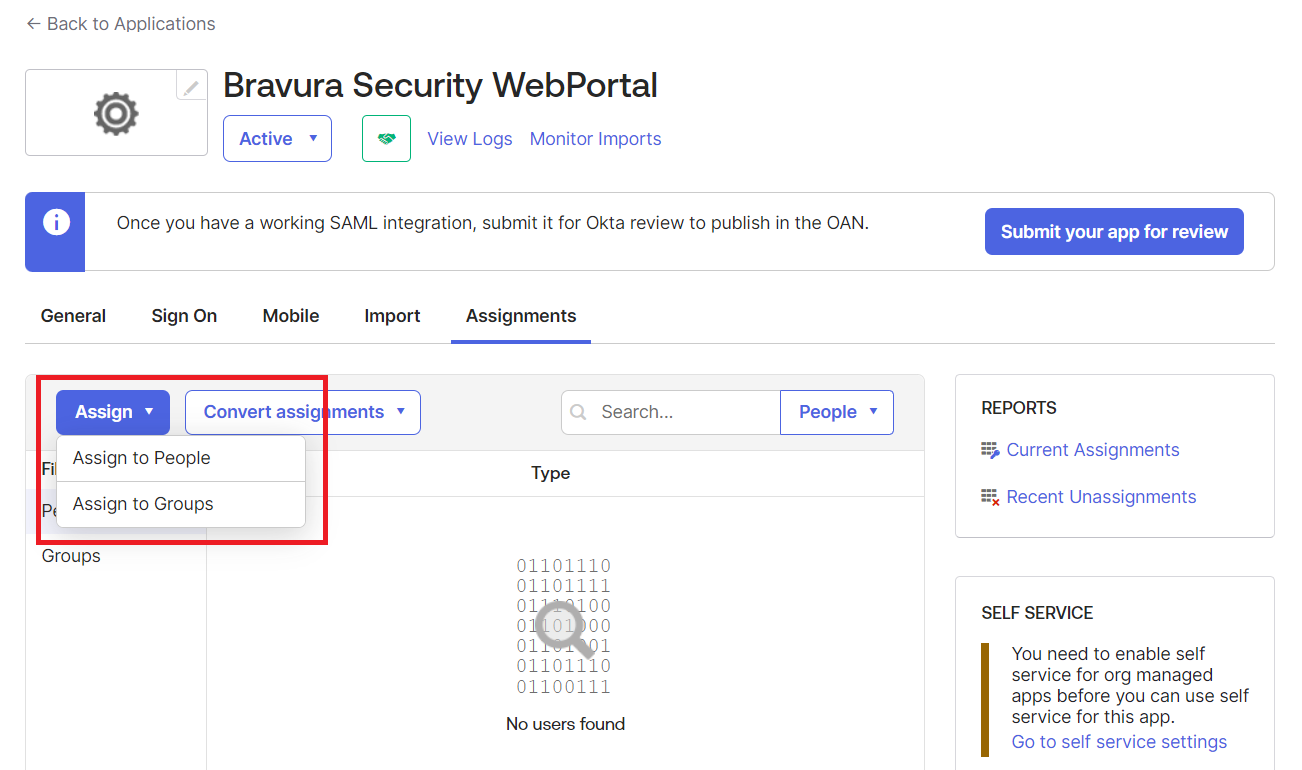
Next:
Set up Bravura Security Fabric to authenticate with the IdP
See also
Okta in the Connector Pack Documentation for details on how to add an Okta target.