Configure the installation
After choosing the database user configuration, the setup program launches idm.msi to configure the software installation. The welcome page is displayed:
Click Next to proceed.
Read and accept the license agreement.
Click Next .
Type the location of the license file.
Alternatively, you can use the Browse button to select the location of your license file.
It is recommended that all replicated servers use the same license file.
Click Next .
The installer displays setup types for you to select from.
Select:
Typical to install with default settings for file locations, ports, and web site. Proceed to Service configuration.
or
Custom to customize installation, port, and web servers settings. Proceed to Install location.
Note
Files for all products are installed; however, only those for licensed products are enabled.
Install location
If you chose a custom installation:
Select the Install location.
It is recommended that you do not change the install location.
Click Next .
Choose the locations for the:
Directory to store log files: This directory should be unique for each instance. The default is <Program Files path>\Bravura Security\BravuraSecurity Fabric\Logs\<instance>.
Directory for all instances to share lock files: This directory should be shared by all instances. The default is <Program Files path>\Bravura Security\Bravura Security Fabric\Locks.
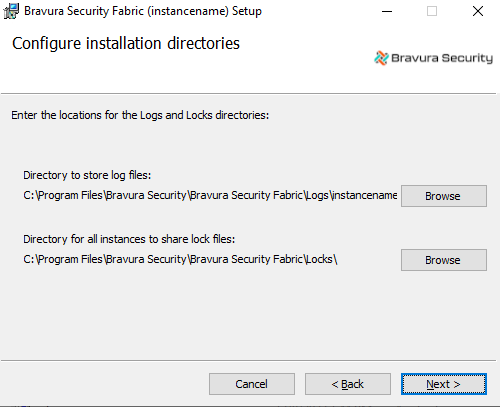
See File Locations for detailed information.
Click Next to proceed to Service configuration .
When you install any Bravura Security product, the default path for program files is <Program files path>\Bravura Security\ as of 12.5.0.
Prior to 12.5.0, the path is <Program files path>\Hitachi ID\.
The directory name is not changed when upgrading.
Three main directories are created when you install Bravura Security Fabric instance, as detailed below.
It is recommended that you do not change these directory locations during the setup process. You cannot install any of the directories required for Bravura Security Fabric on a mapped drive.
<Program Files path>\Bravura Security\Bravura Security Fabric\<instance>\
Directories marked with  include files installed by Connector Pack .
include files installed by Connector Pack .
Directories marked with  include folders and files installed with the optional Analytics app.
include folders and files installed with the optional Analytics app.
Directories marked with 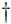 include optional files. They are only installed in a complete installation or if selected in a custom installation.
include optional files. They are only installed in a complete installation or if selected in a custom installation.
Directory | Contains |
|---|---|
| Files required for add-on software, such as Local Reset Extension and SKA. Some files, required to target Netegrity SiteMinder, are installed by Connector Pack . If you installed a global Connector Pack , these files are contained in the Connector Pack global directory. |
| Instance-specific user management connectors (agents). If you installed a global Connector Pack , user management connectors are contained in the Connector Pack global directory. |
| Analytics app specific folders |
| Contains * .rsd files which are Shared Dataset Definitions. These files are only used by SQL Server versions higher than Express. They contain datasets that are shared between reports. |
| Contains * .rdl files which are Report Definitions. These files are the drillthrough reports used by other reports. They are not visible to the end-user. |
| This folder contains other folders. Each folder in this folder is a category in the Analytics app. Within these folders are * .rdl files which are Report Definitions. The folders need to be added to the CUSTOM ANALYTICCATEGORIES system variable to be visible. These reports are then visible to the end-users in the Analytics app. |
cgi-bin | The user web interface modules (* .exe CGI programs). |
db | The Bravura Security Fabric database sqlscripts. |
db \ cache | Search engine temporary search results. These files are cleaned up nightly by |
db \ replication | Stored procedure replication queues, and temporary replicated batch data. |
| Files necessary to make modifications to the GUI. Some files are installed by Connector Pack . If you install a global Connector Pack , files related to connectors are located in the global design directory. |
dictionary | A flat file, Bravura Security Fabric uses this file to determine if new passwords fail dictionary-based password-policy rules. |
idapiservice | Files required to use the SOAP API. |
| Instance-specific ticket management connectors (exit trap programs). If you installed a global Connector Pack , ticket management connectors are contained in the Connector Pack global directory. |
lib | Contains the |
license | The license file for Bravura Security Fabric . |
plugin | Plugin programs executed by Bravura Security Fabric . |
psconfig | List files produced by auto discovery and the |
report | Files and programs for report generation. |
| Instance-specific sample scripts and configuration files. If you installed a global Connector Pack , connector-related sample files are contained in the Connector Pack global directory. |
script | Configuration files and scripts used by connectors, |
service | Service programs. |
sessdata | Session data. A scheduled program removed old data files nightly. |
skin | Compiled GUI files used at run-time (HTML and *.z). |
smon | Monitored session data. This location can be changed by Recorded session management (smon) module options. |
| Command-line programs and utilities. If you install a global Connector Pack , tools related to connector configuration are located in the global util directory. |
| The If you installed a global Connector Pack , this directory is created in the Connector Pack global directory. |
wwwdocs | Images and static HTML pages used by Bravura Security Fabric . |
<Program Files path>\Bravura Security\Bravura Security Fabric\Logs\<instance>\
Any operation that is run by Bravura Security Fabric is logged. Those logs are invaluable when debugging an issue. The log directory by default is <Program Files path>\Bravura Security\Bravura Security Fabric\Logs\<instance>\ . Each instance of Bravura Security Fabric that is installed will have at least one sub-directory within this directory.
The rotatelog scheduled job, which runs on a nightly basis, rotates the logs into a new folder, to reduce disk space usage.
<Program Files path>\Bravura Security\Bravura Security Fabric\Locks
Certain target systems can only be accessed serially, such as Lotus Notes. This is a limitation of the API used to access the target system. In these cases Bravura Security Fabric drops a lock file in the locks directory when an operation is being performed that should only be performed serially. For this reason the locks directory must be the same for all instances of Bravura Security Fabric that are installed on the same server.
When you install Connector Pack , files are placed in different locations depending on type of Connector Pack .
For an instance-specific connector pack, the installer, connector-pack-x64.msi, installs connectors and supporting files in:
<Program Files path>\Bravura Security\Bravura Security Fabric\<instance>\
For a global connector pack, the installer, connector-pack-x64.msi, installs connectors and supporting files in:
<Program Files path>\Bravura Security\Connector Packs\global\
The table below describes the function of directories that are created when a Connector Pack is installed:
Directory | Contains |
|---|---|
addon | Files required to target Netegrity SiteMinder systems |
agent | User management connectors (agents) |
design | Connector Pack -related files necessary to make modifications to the GUI; for example target system address help pages. See the “Customization Guide” for details. |
interface | Ticket management connectors (exit trap programs) |
samples | Sample scripts and configuration files |
unix | The |
util | Tools to support the configuration of various target systems |
Service configuration
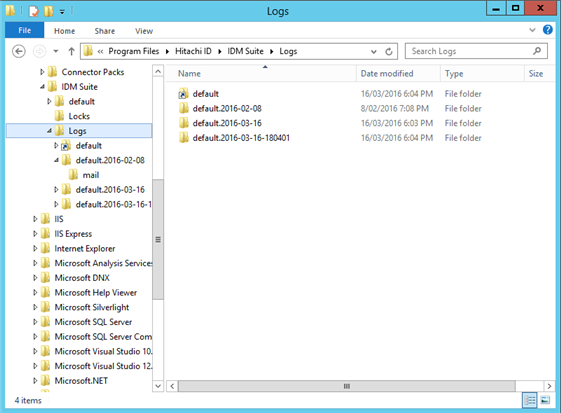
After determining the setup type, enter the Service user ID and Password.
This is the account Bravura Security Fabric services will run as. If IIS is selected as your Web server, this is also the anonymous user for web access.
You can use a local or domain account for the Service user ID. The Password can be up to 64 characters long.
The default is psadmin . If you use the default account and the account does not already exist, the installer will create it with the specified password on the Bravura Security Fabric instance server. If a domain account is specified, the installer validates the account and password before proceeding. An error message will display if the domain account can not be found or the password is incorrect.
Denying interactive log-on for service account is a recognized industry best-practice which is also suggested by Bravura Security Fabric . See Domain requirements for more details on how to create a secure service account.
Click Next to proceed.
See also
In cases where the psadmin account is changed, you can use the serviceacct utility to make updates, as documented in Changes to the service account (psadmin) .
Communication key
Enter the communication key that will be used to encrypt communication between the Bravura Security Fabric server and other Bravura Security Fabric sub-systems on the network.
The key must only contain hexadecimal digits (0-9, a-f).
You can also click Random Key to generate a random key.
Note
The same communication key must be applied to all sub-systems that share communication. It is strongly recommended that you note this key in a safe location.
Click Next to proceed.
Database encryption key
Enter the database encryption key that will be used to encrypt sensitive data stored in the Bravura Security Fabric database; for example, Bravura Security Fabric uses the database encryption key to encrypt passwords.
The key must only contain hexadecimal digits (0-9, a-f).
You can also click Random Key to generate a random key.
Note
The same database encryption key must be applied to all Bravura Security Fabric servers in a replication environment and all sub-systems that share communication. It is strongly recommended that you note this key in a secure location.
Click Next to proceed.
Workstation authentication encryption key
Enter the workstation authentication encryption key that will be used to initialize the communication of untrusted Bravura Security Fabric services to Bravura Security Fabric servers on the network. The workstation authentication encryption key is used by the workstation service for either initial registration or key re-negotiation.
The key must only contain hexadecimal digits (0-9, a-f).
You can also click Random Key to generate a random key.
Note
The same workstation authentication encryption key must be applied to all Bravura Security Fabric servers in a replication environment and all sub-systems that share communication. It is strongly recommended that you note this key in a secure location.
Click Next to proceed.
Connector encryption key
Enter the Connector encryption key that will be used to encrypt sensitive data for communication with the connectors; for example, Bravura Security Fabric uses the Connector encryption key to encrypt and decrypt passwords and administrative credentials used by connectors and exit traps as well as all communication and operations run by the connectors.
The key must only contain hexadecimal digits (0-9, a-f).
You can also click Random Key to generate a random key.
Note
The same Connector encryption key must be applied to all Bravura Security Fabric servers in a replication environment and all sub-systems that share communication. It is strongly recommended that you note this key in a secure location.
Click Next to proceed.
IDMLib encryption key
Enter the IDMLib encryption key that will be used to encrypt sensitive data generated in IDMLib.
The key must only contain hexadecimal digits (0-9, a-f).
You can also click Random Key to generate a random key.
Note
The same IDMLib encryption key must be applied to all Bravura Security Fabric servers in a replication environment and all sub-systems that share communication. It is strongly recommended that you note this key in a secure location.
Click Next to proceed. The order of next steps can vary depending on initial setup choices.
If you chose a custom installation, setup displays Custom port and web server settings
If you chose to use a preconfigured database user,
setupdisplays database server connection settings .If you want to install the Analytics app now, configure options to connect with SQL Server Reporting Services (SSRS) .
Click Skip if you do not want to install the Analytics app now. You can set it up after installing Bravura Security Fabric software, as documented in Managing and using analytics.
In this case, proceed to Configure application administration login information .
Custom port and web server settings
If you choose a custom installation, after configuring keys:
Define port settings.
The defaults are applied during installation unless modified or that port is already in use by another Bravura Security Fabric instance.
Click Next .
Select a Web server for this installation.
If multiple web servers are installed on your Bravura Security Fabric server, select the one on which you want to install Bravura Security Fabric . IIS web servers are automatically detected and configured.
Type an email address to receive administrative notifications.
You can use the Manage the system (PSA) module to set or change this later by modifying the RECIPIENT EMAIL option.
Click Next .
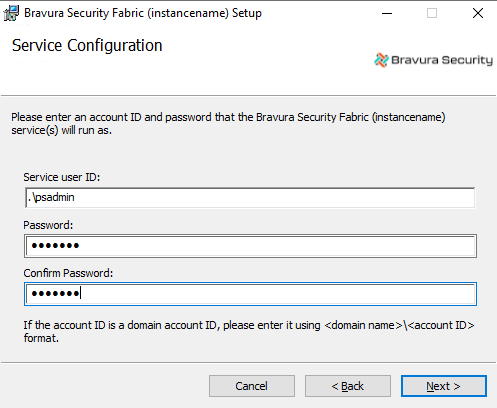
Define web server directories.
Click Next to proceed. The order of next steps can vary depending on initial setup choices.
If you chose to use a preconfigured database user, setup displays database server connection settings .
If you want to install the Analytics app now, configure options to connect with SQL Server Reporting Services (SSRS).
Click Skip if you do not want to install the Analytics app now. You can set it up after installing Bravura Security Fabric software, as documented in Managing and using analytics.
Proceed to Configure application administration login information.
Open ports are an exploitable means of system entry. Limiting the number of open ports effectively reduces the number of potential entry points into the server. A server can be port scanned to identify available services.
All TCP/IP port numbers used for communication between Bravura Security Fabric services and modules across the network are configurable. Following are default values. Note that not all of these services may be active depending on the deployed features.
Description | Program name | Default |
|---|---|---|
Database Service TCP port | iddb | 5555 |
File Replication Service TCP port | idfilerep | 2380 |
Workflow Manager Service TCP port | idwfm | 2240 |
Transaction Monitor Service TCP port | idtm | 2234 |
Password Manager Service TCP port | idpm | 3334 |
Session Monitoring Package Generation Service TCP port | sessmon modules | 2340 |
Discovery Service TCP port | iddiscover | 2540 |
Privileged Access Manager Service TCP port | idarch | 6190 |
Persistent Connector Service TCP port | agtsvc | 4567 |
The defaults are applied during installation unless modified or that port is already in use by another Bravura Security Fabric instance.
On Bravura Security Fabric proxy servers, the following ports are used:
Service | Program name | Default |
|---|---|---|
Proxy service |
| 3344 |
From a user’s web browser to the Bravura Security Fabric server, the following ports are used:
Service | Port (non-SSL) | Port (SSL) |
|---|---|---|
Web Service | 80 | 443 |
For ports that Bravura Security Fabric uses to connect to target systems see the respective sections in the Connector Pack documentation.
Base URL This is the URL of the Bravura Security Fabric server. The installer automatically detects the server name.
Root virtual directory for this instance This is the name of the virtual directory that points to the physical <instance>\cgi-bin\ directory.
The default value is the name of the instance.
Note
Virtual directory paths cannot contain whitespace or the following characters:
% \ / | @ ! # $ ^ & * < > ; : ' ' ? , [ ] { } + = `Web site for this installation If the web server for this installation is IIS, select the web site you want Bravura Security Fabric to use.
Replace the default web page with the index page for this instance Enable this checkbox if you want to replace the default web page with the index page for this instance. The index page automatically redirects users to the Front-end .
Pre-configured database server settings
If you choose to use a preconfigured database user at the beginning of the installation process:
Choose an authentication mode that the SQL Server ID should use. You can choose either SQL Server authentication or Windows authentication. If you choose Windows authentication, ensure that the login exists on the SQL Server database server for the account ID that the Bravura Security Fabric services will run as.
Click Next .
Enter Microsoft SQL Server connection information.
Enter connection information as follows:
Database server name: Type the name of the server hosting the database:
<dbserver>If the database is installed on your Bravura Security Fabric server, use
.(period),localhost, or the server name.If you installed SQL Server with the non-default instance name, you must include a backslash followed by the instance name:
<dbserver>\<instance>For the express edition, the instance is normally
SQLEXPRESS.If SQL Server is using a custom port, the syntax is:
<dbserver>,<port> [ \<instance> ]Database name: Type the name of the database hosting the schema.
Database server user ID: If using SQL Server authentication, type the ID of the dedicated user that you created for Bravura Security Fabric. This field is not visible for Windows authentication.
You must use a different dedicated user for each Bravura Security Fabric instance.
Database server user password: If applicable, type the password for the above user.
If a change has been made to the database server credentials, use the iddbadm program to update the database information.
Advanced configuration
If you want to modify how Bravura Security Fabric installs the database schema, click Advanced on the Database Server configuration page and configure the following:
Install schema: Clear this checkbox if you do not want Bravura Security Fabric to install the schema because it has already been installed by your database administrator, or you are using a shared schema .
Populate default data: Clear this checkbox if you do not want Bravura Security Fabric to populate default data; for example where you want to install to a shared schema.
Schema install user ID: (Optional) If using SQL Server authentication, type the ID of the user to install the schema as. This field is not visible for Windows authentication.
This user must be able to create schema objects. If not specified, Bravura Security Fabric uses the Database server user ID.
Schema install password: If applicable, type the password for the above user.
The password is only required if Install schema is selected and Schema install user ID is specified.
Click Next to proceed.
If you want to install the Analytics app now, configure options to connect with SQL Server Reporting Services (SSRS).
Click Skip if you do not want to install the Analytics app now. You can set it up after installing Bravura Security Fabric software, as documented in Managing and using analytics .
Proceed to Configure application administration login information .
SSRS settings
Caution
If you are installing SQL Server Reporting Service (SSRS) to use Analytics, ensure the server is not a Domain Controller.
You must have access to SQL Server Reporting Services to use this component. You require the following information:
The server name where SQL Server Reporting Services (SSRS) resides
Report Server Web Service URL
Name and password of service account
If you are using an existing report server database you will need that database name
If you are using an existing report server user you will need that username and password
To configure the Analytics app connection to SSRS:
Enter the Report Server web service URL.
Enter the SSRS service username and password.
Click Next .
The page is displayed.
Enter the name of the server where your instance database resides.
Choose your report database user option.
If you want
setupto create and configure a new dedicated database user that can query the instance database, enable the Create a dedicated database user? option.Enter the database administrator name and password so the installer can create the new dedicated database user.
If you already have a dedicated database user created and configured, enter those details.
Click Next .
Configure application administration login information
Type the login ID and password for the Bravura Security Fabric application administrator. The default login ID is superuser. The password can be up to 64 characters long.
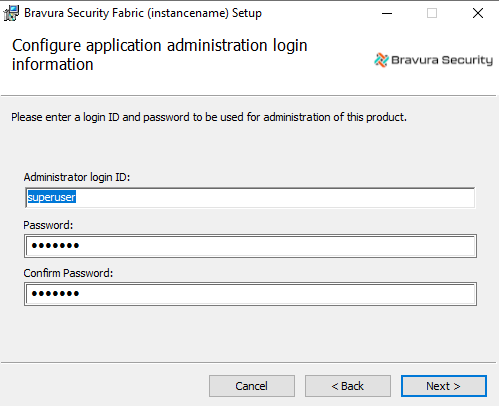
Be sure to remember this login ID and password. You will need them to log into Bravura Security Fabric .
Click Next to proceed.
Configure application REST API login
Type and confirm a password for the REST API endpoints.
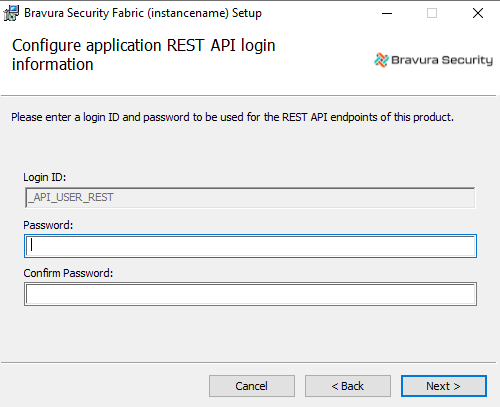
Click Next to proceed.