Okta integration strategy: SAML or API
Okta offers a platform for:
Web single sign-on (SSO) with federation or password form stuffing.
Two-factor authentication (2FA) via a smart phone app or a PIN delivered to user emails or mobile phones.
Simple creation and deactivation of accounts on certain SaaS platforms.
It is possible to integrate Bravura Security Fabric with Okta to utilize one of Okta's authentication methods when signing into Bravura Security Fabric .
Integrating Okta with Bravura Security Fabric
There are two mechanisms available to integrate Okta with Bravura Security Fabric :
Integration with SAML federation; where the Okta service is the Identity Provider (IdP) and Bravura Security Fabric is the Service Provider (SP) . Bravura Security Fabric can also act as the IdP to Okta or any other web app acting as the SP.
Note
The SAML solution is not recommended for Bravura Security Fabric versions prior to 12.0.3. Contact support for more information.
Integration via the Okta web services API; where the Bravura Security login subsystem asks Okta for session status, is also available.
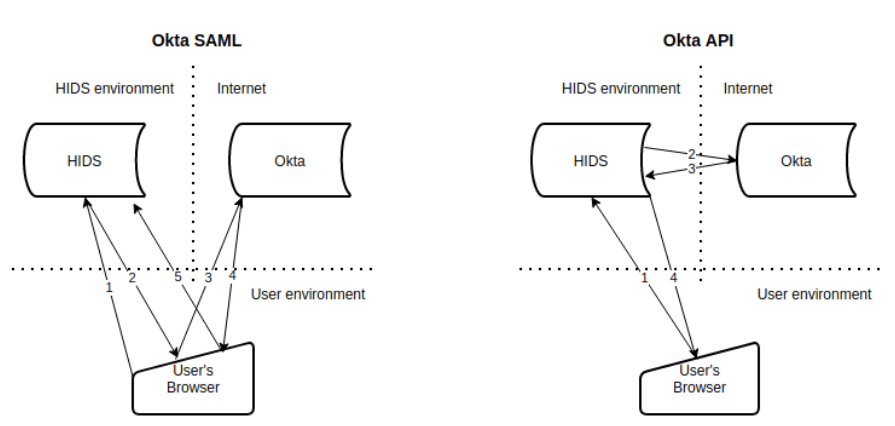
Advantages of a SAML-based integration
Consistent SSO (single-sign-on): Once signed into Okta from one browser, any future attempts to login for the duration of the SSO token, don't require authentication.
Note
This does have security and audit implications for Privileged accounts and should not be implemented alone for those accounts, however, for end-users it is a time-saver.
More consistent user experience:: The visual login sequence with Okta's Web UI showing up when authenticating from other Web applications is what customers' users are sometimes already familiar with.
2FA can be configured natively on the Okta platform by the relevant application administrators.
2FA can be configured using Bravura Security Fabric authentication chains.
Once SAML tokens are created during the login process, the login is transparent for additional SAML SPs
In high-security applications like Bravura Privilege this is actually a security risk; for example, going directly into Bravura Privilege because a user authenticated into Google Calendar may not be secure enough.
There is no need to create an administrative-level API token on the Okta platform and import it into Bravura Security Fabric .
There is no need to create an extra target, or copy a list from the target Okta authenticates against (AD or other LDAP).
Advantages of an API-based integration
Bravura Identity can manage accounts on Okta, and role assignment.
More solid directory integration than the SAML method: Listing accounts from the Okta target directly and making it a SoP can ensure no false-negatives exist, if the Okta directory is out of sync with the SoP of the Bravura Security Fabric instance.
Smaller attack surface: As the diagram above shows, Okta exists on the Internet; connections to it are using encrypted, over TLS:
Using the SAML integration method the user browser needs access to both the Bravura Security Fabric instance and the Okta instance configured for authentication using SAML.
Using the API authentication, the users browser only need access to the Bravura Security Fabric 's UI, which is usually on the private network. Bravura Security Fabric then communicates to Okta.
Less repetitive work for end-users: Users enter their profile ID only once. With SAML, users must enter their ID twice; once when interacting with the Bravura Security Fabric instance and again when interacting with the Okta login subsystem.
More consistent user experience per login: Users interact with just a single portal, the Bravura Security Fabric instance rather than being redirected between two login pages.
Note that each portal can use its own cookie to auto-populate this input field, which reduces the impact on login attempts from a previously used browser.
With API-based integration, two different users can sign into Bravura Security Fabric from the same browser. With SAML-based integration, it is more difficult for users to share a browser; either the previously signed-on user must sign off from both products when finished, or the second user wishing to use the browser must first sign into Okta and only then can sign into Bravura Security Fabric .
API-based integration is much easier to use in cases where users share a laptop and need access to "Self-Service, Anywhere" to reset forgotten, locally cached passwords using Bravura Pass.
It is possible to configure the Bravura Security portal to prompt users to provide multiple Okta factors, leading to multi-factor authentication rather than strictly two-factor authentication.
Configuring and updating an expired API token is less work than updating an expired SAML certificate.