Target system options
The following options are available on the main page in Bravura Security Fabric 12.7.1:
Note
Some of the options on this page may apply to products that you do not have installed.
Options marked with a  in this document are required.
in this document are required.
Symbols in this document indicate that the marked content applies to specific product licenses:
 Bravura Privilege |
Bravura Privilege | 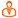 Bravura Identity |
Bravura Identity | 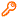 Bravura Pass
Bravura Pass
For IT Service Management (Ticket) systems, only the general options are applicable. When you select a ticket system, other options are hidden.
Option | Description |
|---|---|
| A unique identifier for the new target system. The target system ID can contain letters (A-Za-z), digits (0-9), and other ASCII characters. The target system ID cannot contain the following characters: |
| The target system’s type; which is a description of the connector. The drop-down list includes only licensed target system types for which you have installed the connector Ticket target systems are listed under IT Service Management Systems and are labeled with "(Ticket)". |
| This is the target system name that is displayed to users. Keep this short. If a detailed description of the target system is required, create a static HTML page and define its URL on the Help URL page (see below). |
| The address of this target system. Refer to Connector Pack Documentation for syntax and additional considerations. |
Help URL | In case a longer description would help users, you can compose and post a web page that describes this system further, and enter its URL here. Users can open the URL by clicking the target system description text wherever the text appears in the user interface. |
| Select:
|
| Allow this target system to be included in a certification process. |
Automatically create a Bravura Privilege managed system | Allow this target system to be configured as a managed system in Bravura Privilege . This option can also be used with Bravura Identity or Bravura Pass licenses with limited Bravura Privilege features. Deleting this target system from the Bravura Security Fabric managed systems will remove the ability of Bravura Security Fabric to reset passwords on the target system without manual configuration. For Bravura Privilege licenses, this option is not available for local service mode target systems. You will need to run target system import rules if you delete this target system from the Bravura Privilege managed systems and decide to re-manage it. |
Profile and account association | |
Source of profile IDs | Use this to indicate that users of this system should, by default, also be users of Bravura Security Fabric . This also means that full user names are drawn from this system. |
Account attribute to use as profile ID | By default, Bravura Security Fabric automatically uses the short ID on a Source of Profiles to define the profile name. If you want to use a different account attribute to create the profile ID, type the name of the account attribute in the Account attribute to use as profile ID field. Make sure the chosen attribute is loaded from the target system and that it is populated for all accounts with a unique value. The accounts for which this attribute is blank or doesn’t exist won’t create a profile. If the attribute has the same value for more than one account, no profile will be created and an error notice about "duplicate accounts" will be logged. If the attribute has the same value for more than one account, all of those accounts will be associated with the first profile to be created (usually in alphabetical order). |
Automatically attach accounts | Select this checkbox if user IDs on the target system are identical to those on Bravura Security Fabric . This allows Bravura Security Fabric to automatically associate accounts owned by the user with their user ID. |
Account attribute to automatically attach accounts to user profiles | The attribute to use to associate each account with an existing profile. By default, Bravura Security Fabric automatically attaches an account to a profile if the account's short ID matches the Profile ID. If you want Bravura Security Fabric to use a specific account attribute (rather than the short ID) to determine auto association, type the name of the account attribute in this field. Make sure the chosen attribute is loaded from the target system and that it is populated for all accounts; the accounts for which this attribute is blank or doesn't exist won't be associated with any profile. If the attribute has the same value for more than one account, all of those accounts will be associated with a single profile. |
Auto discovery | |
List accounts | When enabled (default) the connector generates a listing of account login IDs during auto discovery. This option is visible only if the target system supports account listing. |
List account attributes | When enabled (default) the connector generates a listing of account attributes during auto discovery. By default, only account attributes that are mapped to profile and request attributes are loaded, and all attributes are loaded as single-valued. You can override this behavior for individual attributes. In order to use this option the List accounts checkbox must also be selected. Bravura Security Fabric can only list account attributes from supported systems. Refer to Connector Pack Documentation for details of specific systems. |
List groups | When enabled (default) the connector generates a listing of groups during auto discovery. In order to use this option the List accounts checkbox must also be selected. Disabling this option does not remove any existing managed groups; groups must be manually unmanaged or they will be shown in the interface with a red x (invalid) and have zero membership. |
Target system supports multiple owners on groups | When disabled (default) a single group owner is supported for a group. When enabled, multiple group owners are supported for a group. |
List group attributes | When enabled the connector generates a listing of group attributes during auto discovery. In order to use this option the List groups checkbox must also be selected. See the Connector Pack Documentation for details of specific systems. |
Create profile IDs from enabled accounts only | Enable this to prevent accounts that are disabled on the target system from being used to create Bravura Security Fabric profile IDs. If you use the LDAP filter option in the target address, this option is not considered (the LDAP filter overrides it) |
Use ID filters to include only certain users and accounts | You can use ID filters to exclude or include certain users and accounts. By default, an ID filter excludes identified users from Bravura Security Fabric. When you select this checkbox, all accounts are excluded except those explicitly included by an ID filter. You must also select the Include in system option when configuring the filter. |
Track account changes | Select this checkbox to capture changes on target systems that happen out-of-band from Bravura Security Fabric . Changes that will be tracked include: accounts getting added and deleted, accounts joining or leaving managed groups, account attribute values being changed, and account association being changed. The tracked changes are viewable in reports as part of each user’s profile history. |
Track group changes | Select this checkbox to capture changes to group memberships on this target system that happen out-of-band from Bravura Security Fabric . This option can also be set for individual managed groups. The tracked changes are viewable in reports on group membership. |
Automatically manage groups | Configure this option if you want Bravura Security Fabric to automatically manage groups listed on the target system. This option applies to Active Directory, Oracle Database, or Domino Server Script target system types. Some systems have thousands of groups; this option may slow down the listing dramatically and require a lot of space in the backend database; best practice is to manage only the groups whose membership matters for the purposes Bravura Security Fabric is used. Select one of the following: (Disabled) : No groups will be automatically managed; this is the default setting. Only groups with owners, moderated by owners: Only manage groups that have an owner. Assign the owner as the group authorizer. All groups, approval required: Manage all groups on the target system. If a group has an owner, then the owner is assigned as the group authorizer. If a group has no owner, then authorizers must be manually assigned. |
Groups whose membership will be listed | If group listing is enabled, use this option to determine the groups whose membership will be listed. Bravura Security Fabric generates the group membership lists during auto discovery. Select one of the following: Managed groups: Only accounts immediately in the managed group will be listed (nested group members are not listed), and only for groups that are managed by Bravura Security Fabric . Managed groups and child groups (if supported): Group membership will be listed for managed groups and any nested group of a managed group, if the target system’s groups can be configured hierarchically. All groups: Group membership will be listed for all groups, regardless of whether Bravura Security Fabric manages their membership. This option only controls what is written to the membership list files during auto discovery. To enable membership of non-managed groups to be displayed on Bravura Security Fabric module pages, enable all accounts to be discovered objects on the Discovery options tab for targets configured to list group membership. |
Allow child resources, including templates and managed account groups, to inherit implementation configuration | Enable this option to automatically configure implementers for resources based on the host target system’s resource operation configuration. You can override this setting on the managed group and template information pages. |
Check password expiry | For some target systems (Novell Directory Services (NDS), Microsoft Windows server, Active Directory, SQL Server), Bravura Pass can also extract a list of users whose passwords will expire soon, or have already expired. This setting is enabled by default if the account attributes are listed, otherwise it’s unavailable. The list can be used by the Bravura Pass notification system to warn users of pending expiry. |
Program to generate a list of target systems | Some target system entries may actually represent collections of actual target systems; for example, an Active Directory domain can be managed as a collection of domain controllers. The sub-host plugin is used in these cases, and this field is where you enter the name of the plug-in. Sub-host plug-ins are subject to the same timeout interval as password connectors. |
Connector time out | Connectors are given a finite amount of time to perform operations, before Bravura Security Fabric stops them. Use this field to set that timeout (in seconds). A setting of -1 will give the connector infinite time. The default is 300 (five minutes). If operations take longer than this time, they will be retried according to the configuration of the Password Manager service ( |
List time out | Connectors should be given a finite amount of time to run during listing before Bravura Security Fabric stops them. Use this field to set that timeout. The default is -1 (infinite), because the product can’t tell how long each target can take to list. A correctly configured target system should not use infinite timeouts. |
Minimum list file size (bytes) | List files must be at least this large (in bytes). Smaller files are discarded, and replaced by their backups. |
List of proxies to run connectors on | Proxy servers that can run connectors on behalf of the main Bravura Security Fabric server. List servers, separated by a semicolon, in the format: <server name>/<port number>;<server name>/<port number> . The default behavior is to attempt to connect to proxies in the order in which they are listed. The first successful connection is used as the proxy to run the connector. To configure Bravura Security Fabric to attempt to connect to proxies in random order, enable the AGENT PROXY RANDOM setting on the Manage the system > Maintenance > Connector behavior > Options page. |
Allow incremental listing | Attribute lists can be very large. Bravura Security Fabric supports incremental listing of account attributes on some target system types, such as LDAP and Active Directory. For these targets, once the initial discovery has been run, Bravura Security Fabric will only list attributes for an account if it detects that the user has changed on subsequent runs of auto discovery. This setting is enabled by default for target systems that support it. You can generate a full list of account attributes during the next auto discovery by clicking Generate full list on the Target system information page. You must confirm your request before the change takes effect. |
Enable persistent listing | This feature allows Bravura Security Fabric to receive changes from Active Directory and AD LDS LDAP as they happen on the domain controller. This feature is only present on Active Directory DN and LDAP Directory Service target systems. It is disabled by default |
Copy data from these targets, separated by commas, during auto-discovery | This is used along with the "Connector execution order" auto-discovery list as well as a post |
| This option is available if phased authorization is enabled and if the target system supports it. This is useful, for example, in cases where a user’s manager must approve a request before it is sent to the group owner. The default is to add group owners to phase one. |
Account Policy | |
Allow users to verify passwords | Select this checkbox if you want the connector to verify passwords on this target system. If not selected, users will not be able to select the target system for authentication. See |
| Select this checkbox if you want to ensure that new profile IDs do not conflict with IDs on this system. |
| When a new ID for this target system is created, use this program to set the case. Bravura Security Fabric provides two built-in programs: |
| Set this option to determine whether you want template requests to use the existing account (do nothing) or create a new account. |
| Select the target system group to which this target system belongs. Target systems can be grouped in Bravura Security Fabric to apply different password policies, apply different synchronization rules, or to allow help-desk users to manage a subset of target systems. |
Allow users to change passwords | Select this checkbox if you want the connector to change passwords on this target system. If not selected, the connector does not run, and success is always assumed. The target system is not displayed on the results page, and the Password Manager service ( |
Accounts must be included in all password changes | Select this checkbox if this target system must be selected for password operations. On web pages which include target system selection, the selection box for this target system is grayed out. Users cannot deselect it. This applies only when the target system belongs to a target system group where web password change restrictions are set to Any number of accounts can be selected for a password change or All accounts are selected for password change. The Only one account can be selected for a password change group setting overrides this target system setting.. |
Allow users to unlock accounts | Select this checkbox if you want Bravura Pass to manage unlocking accounts on this target system. If not selected, accounts on this target system cannot be unlocked using Bravura Pass . |
Users must have accounts | Select this checkbox if Bravura Security Fabric users must have an account on this target system. This option is specific to the Attach other accounts (PSL) module. |
Allow other users to attach auto-associated accounts | Select this checkbox to allow a user to attach a login ID from another user on an auto-associated target system, using the Attach other accounts (PSL) module. |
Allow enabling accounts | Currently not in use. The "enabling accounts" privilege is configured using user access rules. |
Allow users to detach manually-attached accounts | By default, allowing or disallowing users to detach manually-attached accounts from their profile is controlled by the PSL ALLOW DELETE option. The system default is displayed as the “Effective setting”. You can override the default behavior on individual target systems by selecting Yes or No from the drop-down list. |
| The ID of a profile and request attribute to provide a place to prompt the user for the destination container when creating or moving accounts on context-sensitive target systems. |
Display modules | |
Attach other accounts | Select this checkbox if you want users to be able to attach accounts on this target system. If not selected, the target system will not appear on the self-service login ID reconciliation page. |
View and update profile | By default the target system information is listed for user management. Deselect to hide the target system on user management pages. |
Change passwords | Select this checkbox if you want users to be able to choose to change their passwords on this target system. If not selected, the target system will not appear on the self-service page. Note that you can still force password changes on a target system via synchronization. |
Unlock accounts | Select this checkbox if you want a user to be able to unlock their account on this target system. If not selected, the accounts on this target system will not appear on the self-service page. |
Help users > Attach other accounts | Select this checkbox if you want help-desk users to be able to attach ID on this target system to users’ profiles. If not selected, the target system will not appear on the administrative login ID reconciliation page. |
Help users > Change passwords | Select this checkbox if you want help-desk users to be able to change users’ passwords on this target system. If not selected, the target system will not appear on the assisted page. |
Help users > Unlock accounts | Select this checkbox if you want a help-desk user to be able to unlock accounts on this target system. If not selected, accounts on this target system will not appear on the assisted page |