Windows trigger
The following sections you how to set up transparent password synchronization for a Microsoft Windows server or Active Directory based trigger system.
Before you begin, ensure that you have researched and carried out the steps outlined in Implementing Transparent Password Synchronization .
About the Password Change Notification Module
Bravura Pass can intercept password changes on a Windows-based trigger system using the Password Change Notification Module. The Password Change Notification Module consists of an interceptor service, intcptsvc, and the psintcpt.dll file. The service queues DLL requests and communicates with the Password Manager service (idpm ). The DLL captures native password changes.
The installer package also includes testing and maintenance utility programs.
You can install the Password Change Notification Module on a:
Active Directory domain controller (DC)
This will affect password changes by users of the Active Directory domain. In order to intercept all password changes in your domain, you must install the Password Change Notification Module on every Active Directory DC on your network.
Caution
Do not install the Password Change Notification Module on an Active Directory DC that allows blank passwords. If users change their passwords to a blank password, Active Directory will not send the change to Bravura Pass , and the event will not be logged.
Windows server
Password changes local to that server will likewise be subjected to password strength enforcement and synchronization.
The Password Change Notification Module supports filters that can limit the scope of an Active Directory DC to a specific OU mapped to a target system in Bravura Pass . For example, you may want to limit the passwords that are intercepted to accounts in three OUs on an Active Directory DC. Each OU is mapped to a separate target system set up in Bravura Pass . The target systems may belong to different target system groups with distinct password policies. You can install the Password Change Notification Module on the DC and configure it with three filters mapped to each OU.
You can also use filters to include or exclude specific account names to be sent to the Password Manager service for password strength testing and synchronization.
Install the software
Use intcpt.msi or intcpt-x64.msi from the \<instance>\addon\transparent-synch\ad\ directory to install the Password Change Notification Module.
The following instructions show you how to install and configure the Password Change Notification Module onto a Microsoft Active Directory domain controller (DC) and use the software module to trigger the transparent synchronization process.
Before you begin:
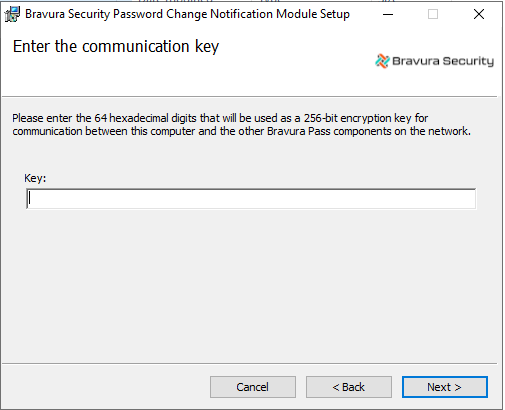
Note the communication key (or Master Key) used to encrypt communication between Bravura Security components on the network.
The CommKey value is encrypted in Bravura Security Fabric . If you did not record the key in a secure location, copy the
idmsetup.inffile from <instance> \ psconfig \ on the Bravura Security Fabric server to the same location as the installer. The installer will extract the Communication Key value from the file.
This section shows you how to manually install the Password Change Notification Module using the Windows Installer. See Using MSI installers for information about setting MSI properties in a transform file or from the command line.
Click below to view a demonstration:
Manual installation steps
To manually install the Password Change Notification Module:
After you restart Windows, native password changes will be intercepted by the Password Change Notification Module and forwarded to the Bravura Pass server for transparent synchronization.
Configure the Password Manager service
Log into the Bravura Pass server as a superuser.
Navigate to Manage the system > Maintenance > Services. Select the Password Manager Service.
Enter the IP address of the AD server with the appropriate mask into Comma-delimited list of IP addresses with CIDR bitmask that are allowed to send socket requests . For instance, if the AD server IP is 10.0.23.76 and it is the only server to contact then the entry would be 10.0.23.76/32.
Click Update.
Stop and start the Password manager service (
idpm).At the bottom of the page, locate the Service status section.
Select Stop the service.
Start the
idpmservice by selecting Start the service .
Troubleshooting
If the password change fails to propagate, double check the following:
Ensure that the instance and AD server firewalls have the correct settings. Incorrect firewall settings will block the change password request from reaching the instance server and the password change will not be propagated.
The domain controller has been added to list of IP addresses allowed to send socket requests to the IDPM Password Manager Service. Once again, the password change request will not be propagated with the wrong IP address.
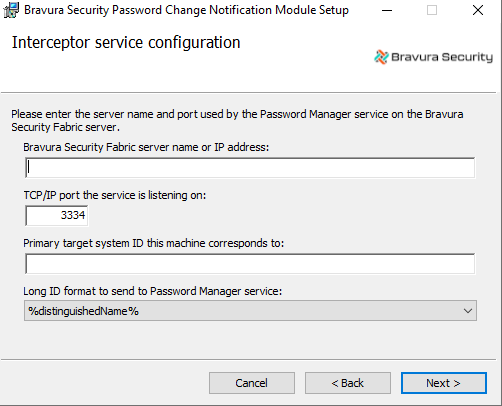
There might be a mismatch on the longid format. As stated before, it must match the longid on the target system.
Setting the longid format
The longid format on the target system must match the longid format used by the Password Change Notification Module. By default, the agtaddn connector’s longid format is set to the NT4 name format.
Complete one or more of the following:
Select the matching longid format during the installation of the Password Change Notification Module,
or
Change the longid format on the target system to use the distinguished name (DN) format. See Selecting the long ID name format in the Connector Pack documentation.
or
Modify the
intcptsvc.cfgconfiguration file, located in:<Program Files path>\Bravura Security\Password Filter\service\
Locate the following lines:
# LongID = "%sAMAccountName%"; # LongID = "DomainName\\%sAMAccountName%"; LongID = "%distinguishedName%";
Comment out the LongID line:
LongID = "%distinguishedName%"
Locate and uncomment the following line:
# LongID = "DomainName\\%sAMAccountName%"
Specify the DomainName of the target.
Save the configuration file.
Restart the
intcptsvcservice.
Testing the connection
Test connectivity and initialize the API by running the diagutil program.
Use the diagutil program for troubleshooting the Bravura Security Password Change Notification Module interceptor. Once executed, it submits real requests to the Password Manager service (idpm ) to process according to the password interceptor service (intcptsvc) configuration file.
This program acts as a real time logging utility to monitor the activities between the interceptor and the Password Manager service (idpm ) on the Bravura Security Fabric server; for example, if an account password is changed, using net user <accountName> <Password> in another command prompt, the activities are displayed in the diagutil prompt until Ctrl+C is used to stop logging.
This program is installed by intcpt.msi or intcpt-64.msi on a Windows transparent password synchronization trigger system and can be found in the following directory:
<Program Files path>\Bravura Security\Password Filter\util\
In order to not affect the password history of a real user, choose a test user to run the password change operation:
diagutil.exe -u test-01 -p doesntmatter
This will check if the password notification DLL is installed, if the interceptor service is running and if there's a successful connection to the configured Bravura Pass server.
It may also report a "license missing" warning which can be ignored.
For best results, ensure that the test user doesn't have a profile created on Bravura Security Fabric y not listing its OU as part of the AD target address or by adding a Profile ID filter in Bravura Pass for that account under Manage the system > Maintenance > Auto discovery > Manage ID Filters . In this case no password history will be updated in Bravura Pass , and it will return code 102 (user not found).
For the list of idpm return codes which Bravura Pass can send back to the interceptor, see the interceptor's config file (service\intcptsvc.cfg).
diagutil.exe [-l <debug level> ] [ -t <timeout> ] -u <userID> -p <userPassword>
Argument | Description |
|---|---|
-l, --level <N> | The debug level 1-6. The default is 4. |
-t, --timeout <N> | The timeout in seconds to receive diagnostic information. The default is 60 seconds. |
-u, --user <userID> | The user to be diagnosed. |
-p, --password | The user’s password. |
diagutil.exe -u qa1000 -p letmein!
returns:
User account name: qa1000 Checking the password filter Dll system registry setting...passed Checking the password filter Dll if it has been loaded...passed Checking the password filter service if it is running...passed Setting password for user [qa1000]: 2010-02-02 11:15:28.561.2903 - [] psintcpt.dll [388,2172] Info: Logging has been enabled, Log level: 4 2010-02-02 11:15:28.576.5698 - [] psintcpt.dll [388,456] Info: User:[qa1000], entered PasswordFilter, sequential number ( SNO ): 1 2010-02-02 11:15:29.675.4688 - [] psintcpt.dll [388,456] Info: User:[qa1000], SNO: 1, PasswordFilter returned [1] 2010-02-02 11:15:29.717.0218 - [] psintcpt.dll [388,456] Info: User:[qa1000], entered PasswordChangeNotify 2010-02-02 11:15:29.720.6418 - [] psintcpt.dll [388,456] Info: User:[qa1000], PasswordChangeNotify finished 2010-02-02 11:15:29.724.6046 - [] diagutil.exe [3244,452] Info: ***** User:[qa1000]'s password has been reset successfully *****
If the debug level is greater than 4 (default), diagutil returns more detail on how the account falls into which categories.
Configuring multiple servers
You may need to make further configuration changes to the server on which you install the interceptor if you have:
Installed Bravura Pass on multiple servers with the Password Manager service running on each server for load balancing,
and
Configured the DNS servers to resolve the Bravura Pass server name in a "round robin" sequence.
Sometimes in this situation, Windows will cache the result and send the request to the same server each time. In this case, you configure the Windows server rotate the list of IP addresses.
You may also want to ensure that the interceptor makes multiple attempts to contact a Bravura Pass server before failing, to handle a condition where a single replica server is down. You can configure the Windows DNS Service to make as many attempts as you require.
After you have installed the interceptor :
On the server on which the interceptor is installed, run the Windows nslookup program with the Bravura Pass server’s hostname to test whether Windows is caching the result. For example, type:
nslookup mercury
The nslookup program displays all addresses defined for the Bravura Pass server, in the order returned from the DNS server. For example:
Server: mercury.example.com Addresses: 10.0.250.119, 10.0.130.108, 10.0.26.15
Repeat Step 1 as many times as there are Bravura Pass servers. For example, if there are three Bravura Pass servers, run the nslookup program three times.
If Windows is not caching the result, the order of the IP addresses is rotated with each query. For example:
Try 1:
Server: mercury.example.com Addresses: 10.0.250.119, 10.0.130.108, 10.0.26.15
Try 2:
Server: mercury.example.com Addresses: 10.0.130.108, 10.0.26.15, 10.0.250.119
Try 3:
Server: mercury.example.com Addresses: 10.0.26.15, 10.0.250.119, 10.0.130.108
If the test shows that Windows is caching the result, force the server where the interceptor is installed, to rotate the list of IP addresses. To do this, add the ManualDNSRotation registry entry:
Entry name ManualDNSRotation
Value 1
Data type REG_DWORD
to the following registry key:
HKLM\SOFTWARE\Bravura Security\Bravura Security Fabric\servertools
If necessary, set the number of times you want the DLL to retry connecting to a Bravura Pass server. To do this, add the ConnectRetry registry entry in the same registry key:
Entry name ConnectRetry
Value number of times to retry connecting
Data type REG_DWORD
Logging
If a connection failure occurs between the interceptor and the Password Manager service, the error is captured using Windows event logging. The error event is written to the Application log and can be viewed using Windows Event Viewer.
You can use the logutil program to enable logging, for debugging purposes, for add-on software. To do so:
Copy the
logutilprogram, located in the util directory on the Bravura Security Fabric server, to the server hosting the add-on tools. It can be placed anywhere on the server.Open a command prompt and invoke
logutilwith:logutil -makekey -instance <instance> -level <loglevel>
The -makekey option needs to be run once only, to generate an instance name and required registry entries.
The Password Change Notification Module installs with a different logging tool (diagutil) that logs similarly to logutil , but has additional arguments to help with troubleshooting or monitoring Transparent synchronization.
See also
Filtering password change requests on a Windows trigger system
You can configure the interceptor service, intcptsvc to include or exclude certain users when they make password change requests on Windows trigger systems. The excluded requests are not sent to the Password Manager service, but are instead processed by the Windows password change facility as usual. This can be used to reduce network traffic between the trigger system and idpm .
You can configure the Password Change Notification Module filter using the configuration file, intcptsvc.cfg, located in:
<Program Files path>\Bravura Security\Password Filter\service\
See the intcptsvc.cfg file for basic instructions, and samples located in:
<Program Files path>\Bravura Security\Password Filter\samples\