Native access disclosure plugins
Run command: pswcmdrun
The pswcmdrun access disclosure plugin is used with account set access requests. It allows users to run commands or scripts on multiple managed systems using managed account credentials.
When a user checks out an account set, Bravura Privilege displays a command execution window if any of the member systems support the run command operation.
Currently the following target systems support the run command operation:
Windows NT Server
Secure Shell (SSHD Host)
Telnet target system
Python Script
Oracle Database
Microsoft SQL Server
Sybase AES Database
Console Script
Additional preparation is required before pswcmdrun can run PowerShell commands on a Windows Server / workstation target. See Windows Server in the Connector Pack documentation for details.
If the plugin is enabled but an account set contains no managed system that supports the run command operation, Bravura Privilege displays the following message upon check-out:
"None of the checked out systems support command execution operation. Command execution interface is not available."
You can modify the following default attributes to control the behavior of pswcmdrun :
| The command to run. |
| Delete command output after expiration. |
| Retry failed commands run via Transaction Monitor Service. |
| Allow users to save commands. |
| Retrieve command output and save on server. |
Command attribute
| %command% |
| By default, the command or script that the user specifies in an account set request will be used to populate the command execution window upon check-out. If you customize this value, the customized value (command or script) will be used to populate the command execution window. It overrides any command or script specified in the request. |
Command prompt: pswxcmd
The pswxcmd access disclosure plugin provides users with access to managed systems by executing an external program and providing credentials. The default program is PuTTY.exe, which opens an ssh/telnet terminal to a Windows machine. The external program must meet the following requirements:
User credentials must be accepted as part of the arguments
Connection details must be accepted as part of the arguments
The program must be installed on the user workstation
The program must either exist on the full path specified as part of the “program” attribute; or if no path has been specified, the external program must be specified on the workstation system path
SMON HTTP URL must resolve to the server from client workstations
There are three types of command prompt controls; one is specifically for managed accounts, and the other two are for temporary group membership, where the password can either be passed onto the command line, or specified upon connection to the remote server.
You can modify the following default attributes to control the behavior of pswxcmd :
| Arguments to supply to the external program. See Arguments attribute for details. |
| If set to true, the external program closes when the user’s access checkout expires. |
| If set to true, a user is prompted for a user name and password. They are made available for arguments as %curruser% and %currpwd% . This is enabled for use with unmanaged passwords, where the user will be prompted for a password that wil be passed on the command line to the command. |
| Set the letter key for the escalation hotkey. When used with the escalation hotkey modifier, the escalation sequence is inserted.See Inserting an escalation sequence for more details. |
| Set the modifier for the escalation hotkey. There are three options: ’Ctrl’, ’Alt’, and ’Middle click’. When used with the escalation hotkey key, the escalation sequence is inserted. See Inserting an escalation sequence for more details. |
| The text to automatically type into the application. |
| If this window name is detected, the escalation sequence is inserted into the program. See Inserting an escalation sequence for more details. |
| The IP or DNS of server. See Domain and host values for further information about using an alternative attribute value. |
| Set the impersonation level of the process. This is set to ’none’ by default. See Impersonating the checked-out account for more details. |
| External program (including full path) to execute. |
| If true, the command is executed within a display window. If false, the command is executed without a display window. |
Arguments attribute
The arguments provide substitution of the password, user name, host, and other custom plugin attributes. The substitutions are as follows:
| %host% |
| The domain managed system member is on, without any optional parameters. |
| %username% |
| The account ID for the privileged password being disclosed. |
| %password% |
| The password being disclosed. |
| %<custom attribute>% |
| If there is a “custom attribute” defined for the plugin, the value of the attribute is used. |
Using custom attributes provides control over the arguments attribute. You can enable the user to override the custom attribute only, while leaving the arguments locked or hidden.
The following are examples of customizations using the pswxcmd access disclosure plugin.
Allow optional arguments
The default settings for pswxcmd execute PuTTY and connect using the privileged password. This example shows how you can add a custom attribute to allow the user to specify the port:
Create an attribute named port with the following settings:
Integer type
Allow the port attribute to be overridden by the users
Set the minimum value to 1
Set the default value to 22
Set the port attribute to be non-empty
Set the arguments attribute value to:
-ssh %host% -l %username% -pw %password% -P %port%
Insert an escalation sequence
You can allow users to insert an escalation sequence into a program (such as PuTTY.exe) using a hotkey or window name.
When a user presses the escalation hotkey, the escalation sequence is automatically typed into the program. By default, the escalation hotkey is Ctrl + K.
To configure the escalation hotkey:
Set the escalation sequence attribute to the text to insert into the program.
Set the escalation hotkey modifier attribute to:
Ctrl – Pressing the Ctrl key with the escalation hotkey key automatically types the sequence. This is the default setting.
Alt – Pressing the Alt key with the escalation hotkey key automatically types the sequence.
Middle click – Middle-clicking automatically types the sequence. The escalation hotkey key attribute is ignored for this option.
If using the Ctrl key or Alt key for the modifier, set a letter key (A-Z) for the escalation hotkey key attribute.
When the window name is detected, the escalation sequence is automatically typed into the program.
To configure the escalation window name:
Set the escalation sequence attribute to the text to insert into the program.
Set the escalation window name attribute for the window where the escalation sequence will be inserted.
Users will not be able to use the escalation hotkey when the escalation window name attribute is defined.
Impersonating the checked-out account
You can allow the requester to run a program (such as cmd.exe) with the permissions of the checked-out account. This will essentially simulate the runas command.
Set the impersonate attribute to:
none – No impersonation will be performed. This is the default setting.
withoutprofile – Attempt to impersonate without loading the user’s profile.
withprofile – Attempt to impersonate and load the user’s profile.
netonly – Do not impersonate locally, but present the managed credentials for network authentication only.
Executing a shell script
This example shows how you can configure pswxcmd to execute a shell script:
Set the program attribute to:
C:\windows\system32\cmd.exe.Set the arguments attribute to:
/C X:\ITApps\runapp.cmd %host% %password% %username%
Executing SQL*Plus
This example shows how you can configure pswxcmd to execute SQL*Plus:
Set the program attribute to:
C:\oracle\product\10.1.0\client _1\bin\sqlplus.exeSet the arguments attribute to:
%username%/%password%@%host%
Changing the message to users on failure
You can change the message displayed to users in the event that the external program fails to launch by modifying the RES CONNECTION TO SERVER FAILED MSG setting in the global or managed system policy Account access request options.
PuTTY over SSH: pswxcmd
This is a preconfigured pswxcmd access disclosure plugin specifically for managed accounts. By default, this plugin is configured to execute PuTTY and connect using the user’s SSH keys instead of the privileged password.
The following requirements must be met:
Connection details must be accepted as part of the arguments
The program must be installed on the user workstation
The user’s private key must already be configured on the workstation
The program must either exist on the full path specified as part of the “program” attribute; or if no path has been specified, the external program must be specified on the workstation system path
SMON HTTP URL must resolve to the server from client workstations
The following attributes are available:
| Arguments to supply to the external program, the %password% argument is not used. |
| This is set to true, the external program closes when the user’s access checkout expires. |
| This is set to false, users are not prompted to enter their credentials. |
| The IP or DNS of server. |
| External program (including full path) to execute. This is set to putty.exe by default. |
| This is set to true, the command is executed within a display window. |
See Command prompt: pswxcmd for more information on modifying these attributes.
Copy: pswxcopy
The pswxcopy access disclosure plugin provides users with access to a password by copying it into the clipboard of the client workstation. By default, it is configured to clear the clipboard if the browser is closed or if the default 30 seconds expiry time for the plugin has passed.
You can modify the following default attributes to control the behavior of pswxcopy :
| If false, the clipboard is not cleared. If true, the clipboard is cleared after the time expires or the browser is closed. |
| This controls how long before the clipboard is cleared. |
Remote desktop / Remote APP RDP: pswxtsvc
The pswxtsvc access disclosure plugin provides users with access to Windows server or client managed systems and RemoteApp programs using Remote Desktop Connection (RDC). The plugin provides automatic connection to the managed system without requiring the entry of administrative credentials for the managed account. You can also connect to the remote server when accessing group sets. This access disclosure plugin supports Network Level Authentication (NLA) and session monitoring.
There are two versions of the pswxtsvc access disclosure plugin:
Remote desktop, for remote access to a managed system’s desktop environment.
Remote APP RDP, for remote access to one of the managed system’s programs that can be run directly on the client’s workstation. RemoteApp must already be configured on the managed system.
Remote APP RDP type disclosures are used for launching applications such as ssms.exe on Server X and providing users with a SQL Server Management window on their desktop that "looks local", but in fact is running on Server X.
The plugin requires the following:
Microsoft terminal services client (mstsc.exe) installed on the user’s workstation.
Terminal service enabled on the client workstation or server.
Firewalls configured to allow RDC (default port 3389/tcp) from user’s workstation to managed system.
The managed account has remote terminal service access to log on under remote terminal services.
SMON HTTP URL must resolve to the server from client workstations
You can modify the following default attributes to control the behavior of pswxtsvc :
| If set to true, the remote desktop application closes when the user’s access checkout expires. |
| Preferred color depth (value must be 8, 15, 16 or 24 bits per pixel). |
| Domain of the user account that the control will connect with. The default is %host% . |
| The IP or DNS of server. |
| If set to true, will enable searching on attribute ”host” when override is allowed for ”host”. |
| Apply Windows key combinations to the remote connection:
|
| Display login button in list of access disclosure plugins when editable attributes exist. If set to false, the login ability is moved to the override page. |
| If set to true, the screen mode will be full screen and extended to all monitors, provided there is more than one monitor. |
| The port to use when connecting to the host. |
| If set to true, will enable redirecting of the clipboard. |
| If set to true, will enable redirecting of devices. |
| If set to true, will enable redirecting of local disk drives. |
| If set to true, will enable redirecting of local ports. |
| If set to true, will enable redirecting of Point of Service devices. |
| If set to true, will enable redirecting of printers. |
| If set to true, will enable redirecting of smart cards. |
The following disclosure attributes are applicable to the Remote desktop access disclosure plugin only:
| If set to true, will connect to the server for remote administration. |
| If set to true, the screen mode will be full screen. If set to false, the screen mode will be windowed. |
| The desktop height used when using windowed mode. |
| Idle time before auto logoff. |
| If set to true, the screen mode will be full screen and extended to all monitors, provided there is more than one monitor. |
| If set to true, will enable the client computer to scale content to fit the window size. |
| An overridable attribute with support for the special value %shortid% , which retrieves the managed account’s shortid. Add this attribute manually through UI. |
| The desktop width used when using windowed mode. |
The following disclosure attributes are applicable to the Remote APP RDP disclosure plugin only. You can obtain these values by viewing the contents of the RemoteApp’s .rdp file.
| If set to true, the server should expand environment variables in the command line arguments. This is set to false by default. |
| If set to true, the server should expand environment variables in the working directory path. This is set to false by default. |
| The command line arguments for the RemoteApp program, if applicable. |
| The RemoteApp program name. |
| The RemoteApp program alias. (ex. —— <program> ) |
| The working directory on the server for the RemoteApp program. |
Domain and host values
The domain and host values are used to connect to the remote system. Their values may depend on how the managed system is set up, and whether it is push or local service mode, manually or automatically discovered.
The domain must be the DNS Domain Name or NetBIOS name. It should not be an IP address. The reason is that the Windows logon requires the account ID and the context (domain/local machine) to identify the administrative user. If an IP address is used in place of a proper name, the connection will fail.
Bravura Privilege gets the replacement value for %host% from the managed system’s address, or the ’name’ attribute for discovered systems. You could choose to leave the value as an IP address. Windows Server 2008 and above supports an IP address for the host.
If the address does not contain the DNS name (for example, if it is an IP address) and you want it to, you have several options:
If the system is local service mode, use one of the substitution values
%NETBIOS%,%DNSHostname%, or%NetbiosDomain%depending on the type of account. Default is %NETBIOS% .If the system is push mode, and if using the Windows NT connector, enable WINNT_EMIT_INFO and use
%DNSHostname%. This allows the Windows NT connector to return the IP and DNS hostname on the reset operation.If the system is push mode, and if using a scripted connector (
agtssh,agtdos,agttelnet), configure the PSLang script to return the IP address and DNS hostname on the reset operation.Use a managed system attribute set by the API Service
ManageSystemAttrAddfunction. The key-values set for the managed system can then be used for the host/domain settings.Use a hardcoded value.
Let the user override the value.
When an user checks out a domain account, the user has the option to select from a list of domain member computers to connect to. To enable this, the ”host” attribute must have the ability to be overridden by the user, and the ”host search” attribute is set to true. As well, discovered systems must be listed from the Active Directory target.
Local service managed system values
The terminal services plugin connects to the domain set in the managed system’s address field by default.
When you install the Bravura Privilege local service, it transmits the information about the workstation, including:
DNS Domain name
NetBIOS domain name
Fully qualified DNS name
NetBIOS name
Physical DNS domain name
Physical fully qualified DNS name
Physical DNS host name
Physical NetBIOS name
You can view the information for a workstation by clicking Manage the system > Privileged access > Managed systems > < Workstation ID > , then scrolling down to the information table below the account table.
The attribute names can be used to substitute values for the domain and host attributes for the pswxtsvc ; for example you can set the domain value to %NETBIOS%, %DNSHostname%, or %NetbiosDomain%.
Changing the failure message to users
You can change the message displayed to users in the event that the external program fails to launch by modifying the RES PROGRAM PATH INVALID MSG setting in the global or managed system policy Account access request options.
Authentication prompting
If the managed system you are connecting to is configured to include a prompt for password upon connection, you may notice that the password field is already filled in. You can proceed by clicking OK ; you do not need to specify any additional information.
The password is passed from the disclosure plugin to the RDP client via Windows UI Automation (MSAA).
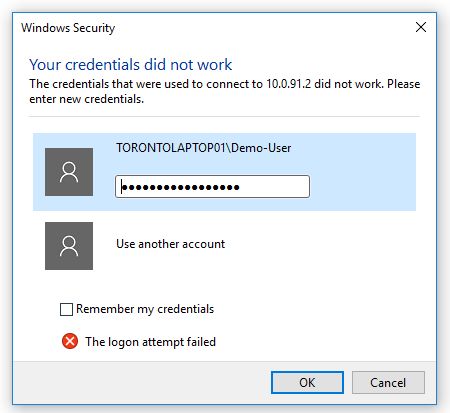
If you receive a similar error and the password is not populated at all, it's possible that Windows changed the RDP dialog. If you are using a supported version of Bravura Security Fabric
Bravura Security Fabric , contact support so they can look for a possible patch.
Single sign-on authentication
You can configure SSO (single sign-on) authentication so that domain users requesting access to group sets can bypass the authentication prompt when running the pswxtsvc access disclosure plugin. SSO is implemented by using the pre-established credentials used to log onto a client computer and sending it to the remote server directly. This allows the user to access the remote server without needing to enter the password multiple times.
In order for SSO to be in effect, the client computer must be on the same domain as the remote server, and the user must log onto the client computer with their domain account.
To order to accommodate single sign-on authentication, you must configure settings on both the remote server and the client. Remote Server
The remote server must be Windows 2008/Vista or above, and it must allow connections from computers running Network Level Authentication.
To allow connections from computers running Network Level Authentication:
Go to Start menu and right click on Computer.
Click Properties.
Click Remote settings.
Select Allow connections only from computers running Remote Desktop with Network Level Authentication.
Click Select Users...
Click Add... to include users that will be requesting group set access to ensure they can remotely log onto the server.
Click OK.
Click OK again to close the system properties.
Remote Client
The remote client must be Windows XP SP3 or above, and support Network Level Authentication.
For Windows 2008/Vista+ Clients:
Go to Start menu, type
gpedit.mscin the search box, and click on the program to access the Local Group Policy Editor.Expand Computer Configuration \ Administrative Templates \ System \ Credentials Delegation.
Double click on Allow Delegating Default Credentials.
Set this object to Enabled.
Click the Show... button to add servers to the list.
Configure a list of trusted remote servers for SSO.
For each server, enter a new value of TERMSRV/ < hostname > where < hostname > is the address that the
pswxtsvcaccess disclosure plugin will use to connect to the remote server. Typically, this will be the fully qualified DNS name of the server.You can also simply type in TERMSRV/. < domain > to include all servers in < domain > .
For Windows XP SP3 Clients:
Go to the Start menu, type
regeditin the search box, and click on the program to access the Registry Editor.Ensure that you are comfortable and knowledgeable in the mechanics of the registry before you attempt to change any configuration settings. Contact support@bravurasecurity.com if in doubt.
In HKLM \ SOFTWARE \ Policies \ Microsoft \ Windows, create a new key called
CredentialsDelegation.In the newly created CredentialsDelegation key, create a DWORD value called
AllowDefaultCredentialsand set its value to 1.Create a new key under
CredentialsDelegationcalledAllowDefaultCredentials.In the newly created
AllowDefaultCredentialskey, create a new string value.Set the name of this to some unique identifier; you may wish to simply use ”1”, ”2”, ”3”, and so on. Set the value to
TERMSRV/ < hostname >, similar to above.Repeat this step for each server you want to enable SSO for.
Go to HKLM \ SYSTEM \ CurrentControlSet \ Control \ Lsa and modify Security Packages by appending
tspkgto it.Go to HKLM \ SYSTEM \ CurrentControlSet \ Control \ SecurityProviders and modify SecurityProviders by appending
credssp.dllto it.
Display: pswxview
The pswxview access disclosure plugin provides users with access to a password by displaying it within the browser. When the secure method is enabled, Bravura Privilege uses JavaScript to decrypt the privileged password embedded in the page. If the insecure method is enabled, the browser can store passwords in plain text in the page source, and users can view the password in browsers that do not have JavaScript enabled.
You can modify the following default attributes to control the behavior of pswxview :
| If true, the password is only disclosed if the browser has JavaScript enabled, and the password is not selectable. If false, the password is available in plaintext for browsers without JavaScript. |
| This controls how long the privileged password is shown. |
| Allows the password to be split amongst multiple viewers so that no single viewer sees the entire password. |
Changing default font and size of viewable passwords
You modify the default font and size of viewable passwords by opening the following files:
<instance>\skin\widgets \ pluginctrl-end.html
<instance>\skin\widgets \ ie \ pluginctrl-end.html
and editing the following lines:
passFontFamily: ‘<font_name>' passFontSize: <font_size>
If the ie directory exists, the file in it will override the global file outside of it.
Split password view
You can split up a password amongst multiple viewers by specifying the pwd split attribute. This takes the form ”n/m” where m is the number of pieces to split the password into, and n is the number of the piece that this instance of the control should display.
For example, 1/2 will display the first half of the password, while 2/2 will display the second half. You can configure a plugin to determine what part of the password a viewer will see. See Using a plugin to define access disclosure plugin . If you don’t intend to use password splitting, you can safely delete the default pwd split attribute.
Browser driver: pswxdom
Use an alternative disclosure plugin, such as Website access disclosure plugins , as Internet Explorer is no longer a supported browser. For information about pswxdom see documentation for 12.5 or older.