Example: Onboard users from an Active Directory target
This example describes how to manage an Active Directory target and onboard accounts to be managed by a team.
Install the components
The following components are required for this example:
RefBuild.pam_team_management.
Scenario.pam_system_type_vault.
Manage the Corporate AD target system
Click Manage the system > Resources > Target systems > Manually defined .
Select the Corporate AD target system.
Select Automatically create a Privileged Access Manager managed system.
Click Change next to the Address field and enter the domain for your environment.
Click Continue .
Click Update.
Click the Credentials tab.
Enter your target’s credentials.
Click Update.
Click Maintenance > Auto discovery Execute auto discovery.
Click Continue.
Click Privileged access > Managed system policies.
Select the ONBOARDED_ACCOUNTS managed system policy.
Click the Member systems tab.
Click Add new… .
Select the Corporate AD managed system and click Select.
Create and set up a team
Create a team administrator:
Click Manage the system > Policies > User classes .
Select the PAM_TEAM_ADMINS.
Click the Explicit users tab.
Click Select .
Search and select a user.
Click Add.
This user can now log in and create, delete and manage teams.
Log into Front-end (PSF) as the team administrator.
Click Manage Resources.
The Pre-defined requests page is displayed.
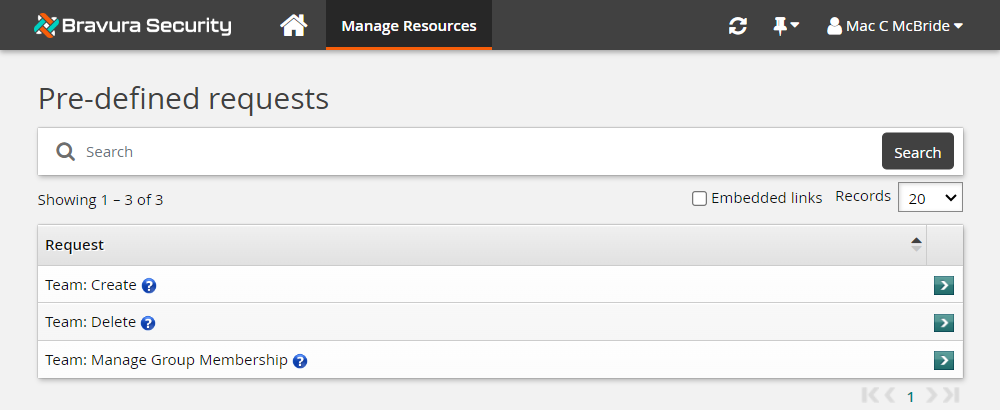
The team administrator can create, delete and manage teams using these pre-defined requests.
Click Team: Create .
Bravura Security Fabric displays the team creation wizard
Enter the following information:
Team Name: Vault-Management-Team
Team Description: Team to manage system vault
Click Next .
Add six groups. Use the ”More” icon to add more team name fields to the list.
Team Trustees Users who can make team management requests.
Account Trustees Users who can make account management requests (onboard accounts).
Approvers Users who allow or disallow access requests.
Auto Approved Users who can check-out access to systems and accounts without making an access request.
Requesters Users who can make access requests.
Credential_Managers Users who can override or randomize the stored password on a checked-out account.
System Trustee Users who can make system management requests (onboard systems).
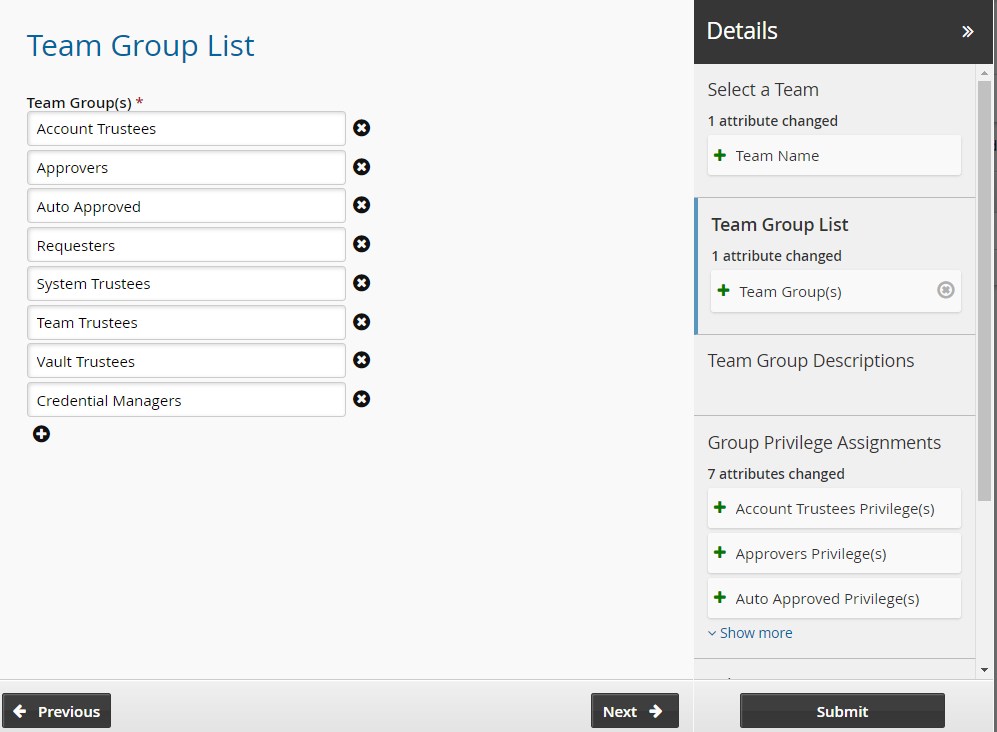
Click Next and add team descriptions.
Click Next .
Assign privileges to the team groups:
Team Trustees Team trustees
Account Trustees Account trustees
Approvers Approvers
Auto Approved Auto_Approved and requesters
Requesters Requesters
Credential Managers Requesters and Credential_manager
System Trustees System trustees
The Credential_Manager privilege allows a user to override or randomize the stored password on a checked-out account.
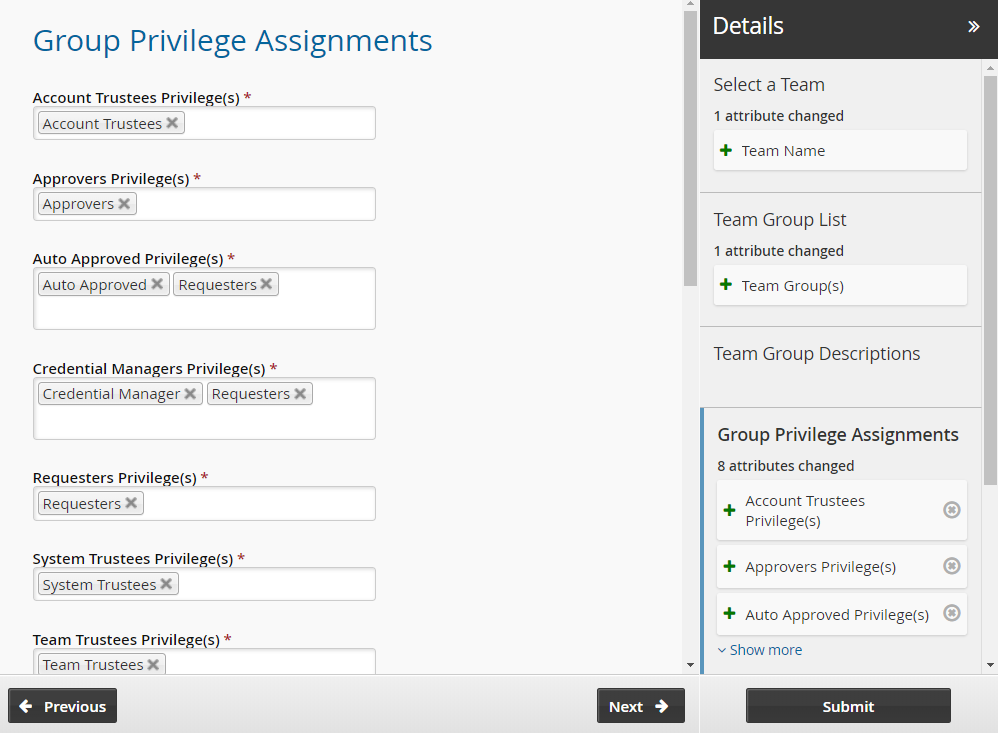
Click Next .
Set the initial team trustees for the new team. There must be at least one team trustee to create a team.
Click Submit.
Bravura Security Fabric notifies authorizers to review the request if required.
Click the View request link at the top of the page to view the status of the request.
Once the request has been approved, the team will be configured.
Add users to the additional groups in the team.
Log into Front-end (PSF) as a team trustee.
From the home page, click Manage Resources.
Click Team: Manage Group Membership .
Select the Vault-Team.
Click Next .
Select the Account Trustees, Approvers, Auto Approved, Requesters, System Trustees, Vault Trustees, Credential Managers and Team Trustees groups.
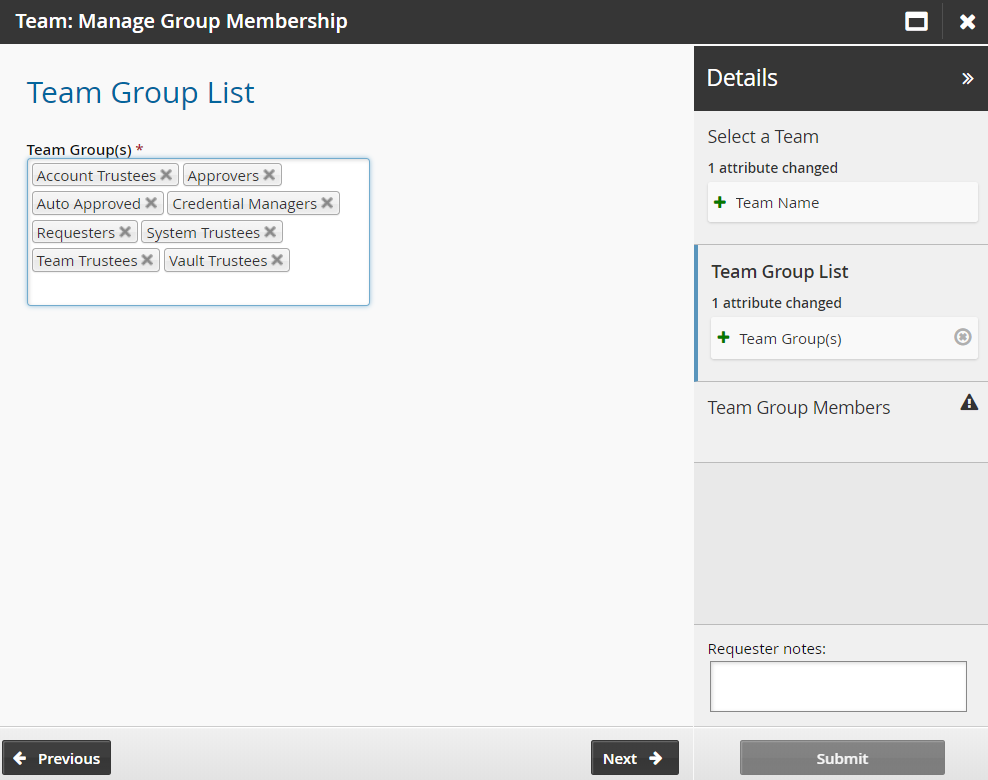
Click Next .
Add members to each team group.
Click Submit.
Bravura Security Fabric notifies authorizers to review the request if required.
Click the View request link at the top of the page to view the status of the request.
Once submitted and approved, the group’s membership will be updated to include the selected users.
Onboard the Corporate AD system
Log into Front-end (PSF) as a superuser.
Click Manage the system > Privileged access > Managed systems.
Select the Corporate AD managed system.
Enter the name of the team that will manage this system.
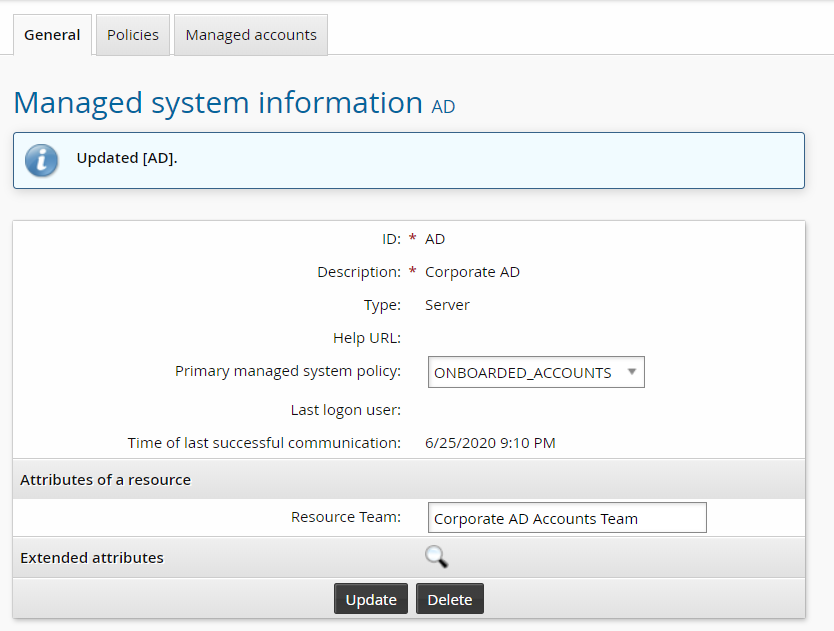
Click Update.
Onboard Corporate AD accounts to a team
Log into Front-end (PSF) as the account trustee for the corporate AD team.
Click Manage Resources.
Click Account: Onboard.
Select an account to be managed by the corporate AD team.
Click Next .
Select the standard policy as the Managed System Policy ID .
Enable View and Copy Password.
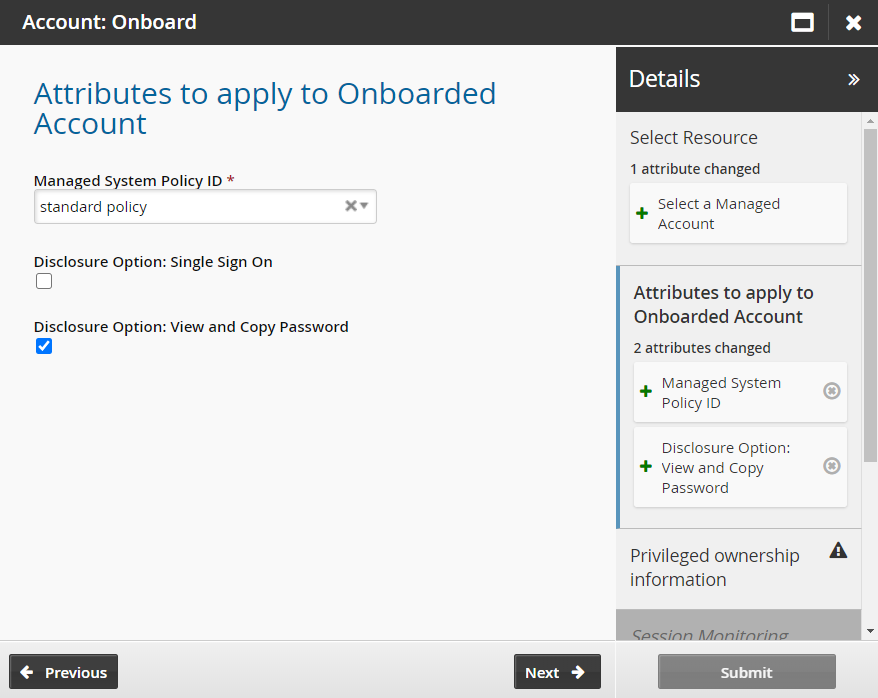
Click Next .
Select the Corporate AD Accounts Team as the account team.
Click Next .
Click Next .
Enable Allow override and randomization of password.
Click Submit.
Once the request has been approved, trustees of the AD Corporate team can manage accounts on this system.