Primary server requirements
Each Bravura Security Fabric server is configured as follows:
Bravura Security Fabric software requires the following hardware:
Intel Xeon or similar CPU. Multi-core CPUs are supported and leveraged. Dual core is a minimum.
At least 16GB RAM – 32GB or more is leveraged and is typical for a server.
At least 600GB of HD storage, preferably in an enterprise RAID configuration for reliability and preferably larger for retention of more historical and log data.
More space is always better, to increase log retention.
At least one Gigabit Ethernet NIC.
Ensure you take into consideration the hardware requirements of any other software that may share the Bravura Security Fabric server; for example, database storage requirements.
See also: Support for virtual machines.
Bravura Security Fabric requires one of the following operating systems:
Windows Server 2025.
Windows Server 2022.
Windows Server 2019.
Windows Server 2016.
It is recommended that the server is not a domain controller.
Bravura Security Fabric uses 64-bit binaries. If both 32-bit and 64-bit software is available, only install 64-bit unless mentioned otherwise in our documentation. Do not install Microsoft's SDK, only the items mentioned below.
TCP/IP networking, with a static IP address and DNS name entry
Cryptographic certificate
Microsoft .NET Framework 3.5 and 4.5+
.NET Runtime 8.0 with the following:
ASP.NET Core Hosting Bundle 8.0.x (latest. Use 'Hosting Bundle', not x86 nor x64)
.NET Desktop Runtime 8.0.x
The .NET Runtime is from:
Web Service Enhancements (WSE) 2.0 SP3 for Microsoft .NET or greater
Note
This requirement is only needed for the "SOAP Web Service (
agtsoap)" and "XML-RPC Web Service (agtxml)" connectors.Web server (IIS) with the following:
HTTP redirection
The IIS URL Rewrite module from:
CGI
Dynamic Compression
Static Compression
WebSocket Protocol
Bravura Security Fabric requires:
A Microsoft SQL Server 2022 (recommended), Microsoft SQL Server 2019 , Microsoft SQL Server 2017 , or Microsoft SQL Server 2016 SP2 instance is required to host the Bravura Security Fabric schema:
Normally one database instance per application server.
The SQL Server database software can be deployed on the same server as the Bravura Security Fabric application, as this reduces hardware cost and allows application administrators full DBA access for troubleshooting and performance tuning purposes.
See Where to install the software for more information.
If the database software is deployed on a separate server, it is recommended that you install the client software that corresponds to the database backend.
See Installing Database and Database Client Software for details.
The Connector Pack contains connectors which integrate Bravura Security Fabric with target systems.
It is recommended, but not required, that you install the Connector Pack after the Bravura Security Fabric . This allows you to select instance-specific or global installation.
See Installing Connector Pack for details.
The following software must be installed before installing Bravura Security Fabric:
Native clients for the systems that Bravura Security Fabric will interface with. Refer to the Connector Pack documentation for information specific to each type of target system.
Microsoft Visual C++ 2015 Redistributable (x64 and x86)
Microsoft Visual C++ 2015 Redistributable Package is required for Bravura Security Fabric 10.0 and higher. It is required for certain Bravura Security Fabric run-time components that use Visual C++ libraries. This is automatically installed during setup , if prerequisites are met.
Note
The installer checks prerequisites for C++ runtime and universal CRT. Before these two can be installed, the system requires the KB2919355 update (this is a set of patches, which has to be installed in order by clearcompressionflag.exe, KB2932046, KB2959977, KB2937592, KB2938439, KB2934018). KB2938439 must be patched before KB2919355 can be patched. During the installation of patches, if a Windows dialog box displays the message: ”The update is not applicable to your computer” and you are sure that you installed the patch that matches your operating system, it is likely that there are other prerequisites that need to be installed before the current patch.
At least one web browser (such as Chrome)
A Git client (for revision control)
Caution
Anti-virus software may impact Bravura Security Fabric functionality and performance. It is strongly recommended to exclude Bravura Security Fabric Bravura Security Fabric and database directories from the anti-virus software.
Python 3.11.2+ must be installed before installing Bravura Security Fabric. It is required for certain components, including the Python IDMLib library used to help create plugin programs, the Health check monitor, and the Pattern components (reference builds).
Ensure that Python is installed for all users to allow the Bravura Security Fabric service user (psadmin) account appropriate access to the Python installation.
It is recommended to add Python to the system PATH. This may also be added by selecting the Add Python 3.11 to PATH option during the Python installation.
Python 3.11.2+ is optional for Connector Pack installations. It is however required for the agtpython and pxpython connectors.
For older versions of Bravura Security Fabric, there are alternate versions of the agtpython connector located in the agent\alt directory and alternate versions of the pxpython connector located in the interface\alt directory that are compatible with specific versions.
Below is a compatibility matrix that should be taken into consideration when upgrading Bravura Security Fabric and Connector Pack in regards to Python requirements and compatibility.
Python is optional for Connector Pack 4.3.x+ installations but is required for the agtpython and pxpython connectors. For older versions of Bravura Security Fabric, there are also alternate versions of the agtpython and pxpython connectors located in the agent\alt and interface\alt directories that are compatible for specific Python versions.
Y denotes that the versions are compatible and N denotes that the versions are not compatible. Y* indicates that there are alternate connectors for agtpython or pxpython that are shipped with the noted Connector Pack .
Instance version | 3.3.x | 3.4.1 | 3.4.3 | 3.5.3 | 3.7.x | 3.8.x-3.9.x | 3.10.x | 3.11.x |
|---|---|---|---|---|---|---|---|---|
12.8.x / CP 4.7.x | N | N | N | N | Y* | N | Y* | Y |
12.7.x / CP 4.6.x | N | N | N | N | Y* | N | Y* | Y |
12.6.x / CP 4.5.x | N | N | N | N | Y* | N | Y* | Y |
12.5.x / 4.4.x | N | N | N | N | N | N | Y | N |
12.4.x / CP 4.3.x | N | N | N | N | Y* | N | Y | N |
12.0 - 12.3.x / CP 4.0.x - 4.2.x | N | N | N | N | Y | N | N | N |
10.0.4 - 11.1.3 / CP 3.1.4 - 3.3.2 | N | N | N | Y | N | N | N | N |
9.0.3 - 10.0.3 / CP 3.1.0 - 3.1.3 | N | N | Y | N | N | N | N | N |
9.0.0 - 9.0.2 / CP 3.0.0 - 3.0.2 | N | Y | N | N | N | N | N | N |
8.2.8 / CP 2.4.0 - 2.5.2 | Y | N | N | N | N | N | N | N |
See also
Install the 64-bit version of Python 3.11.2, before installing Bravura Security Fabric or Connector Pack.
Ensure that Python is installed for all users to allow the Bravura Security Fabric service user (psadmin) account appropriate access to the Python installation.
To install Python 3.11.2+:
Download and run the 64-bit installer from python.org .
On the first screen, check the Add Python 3.11 to PATH option.
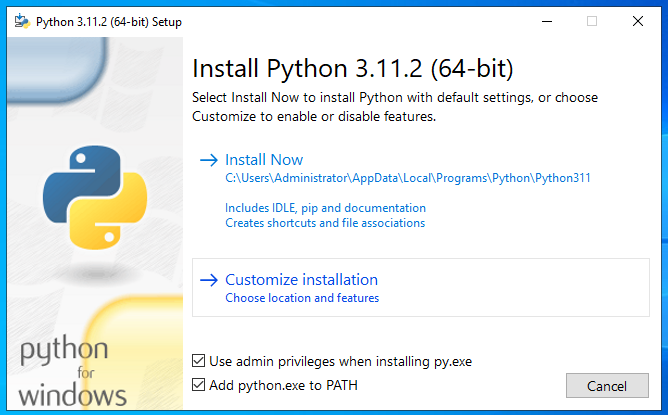
Click Customize installation.
Use all Optional Features.
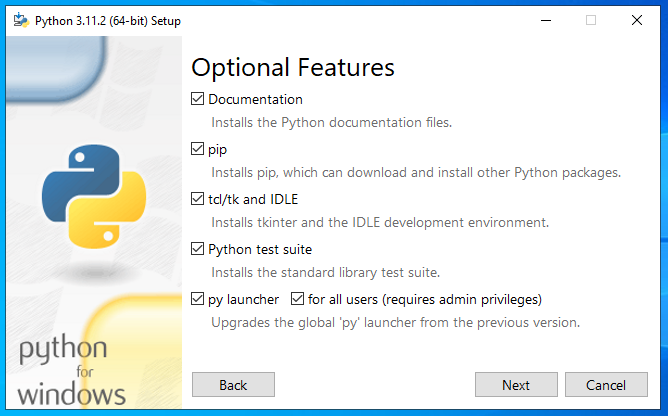
On the Advanced Options screen, select Install for all users, and ensure that the path is correct in the Custom install location.
Do not select Download debugging symbols or Download debug binaries.
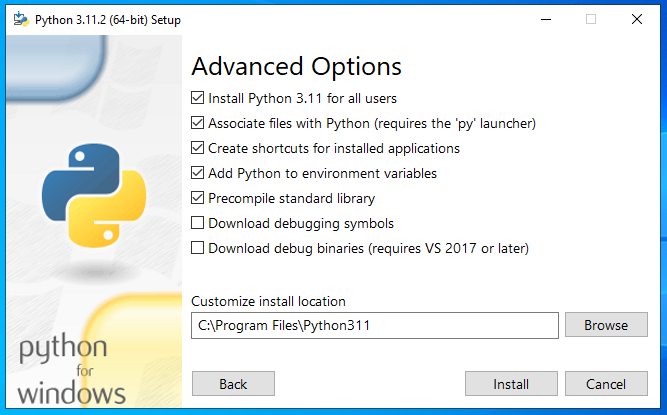
Click Install.
During the instance pre-installation check the installer checks if IIS module "Web Distributed Authoring and Versioning" (WebDAVModule) is installed. If so, the installer warns that this module may interfere with REST API usage and that it should be disabled. This can be done after the instance is installed.
To disable WebDAVModule for an already installed instance (named "myinstance" in this example), run the command:
%SYSTEMROOT%\system32\inetsrv\appcmd.exe delete module /module.name:"WebDAVModule" /app.name:"Default Web Site/myinstance"