Example: Expose the USE_MANAGED_CREDENTIALS attribute
This example demonstrates how to expose the USE_MANAGED_CREDENTIALS attribute so a system trustee does not need to manually enter the system's credentials when onboarding a system; instead a Bravura Privilege managed account will be used, and when that managed account’s password is updated by Bravura Privilege, the credentials used by the onboarded system will be too.
Requirements
This example assumes:
An AD Target has been configured as a managed system
An AD Target has been configured as a source of profiles.
Auto discovery has been run.
RefBuild.pam_team_management is installed.
Scenario.pam_system_type_winnt is installed.
A team administrator has been configured.
A team, with a system trustee has been configured.
Expose the USE_MANAGED_CREDENTIALS attribute
Log in as superuser.
Click Manage the System > Privileged Access -> Managed System policies.
Select the PRODUCT_ADMIN_ACCOUNTS managed system policy.
Click the Member systems tab.
Click Add new….
Select the AD managed system.
Click Select .
Click the Managed accounts tab.
Click Add new… .
Select an account that can be used as target administrator for the onboarded systems.
Click Select .
Click Home.
Click Manage external data store.
Select the hid_global_configuration table.
Add an entry for the USE_MANAGED_CREDENTIAL attribute to be exposed:
Namespace: pam_pdr_onboard_system
Setting: OPTIONAL_ATTRS
Value :USE_MANAGED_CREDENTIAL
Click Update.
Update the following entry in the hid_global_configuration table to match the Value of the managed system policy you configured above:
Namespace : pam_system_management
Setting : MANAGED_ADMIN_CREDENTIAL_POLICY
Value: PRODUCT_ADMIN_ACCOUNTS (or any other MSP which is applied to the managed target admin account)
Test the System: Onboard PDR
Log in as a system trustee.
Click Manage resources.
Click System: Onboard.
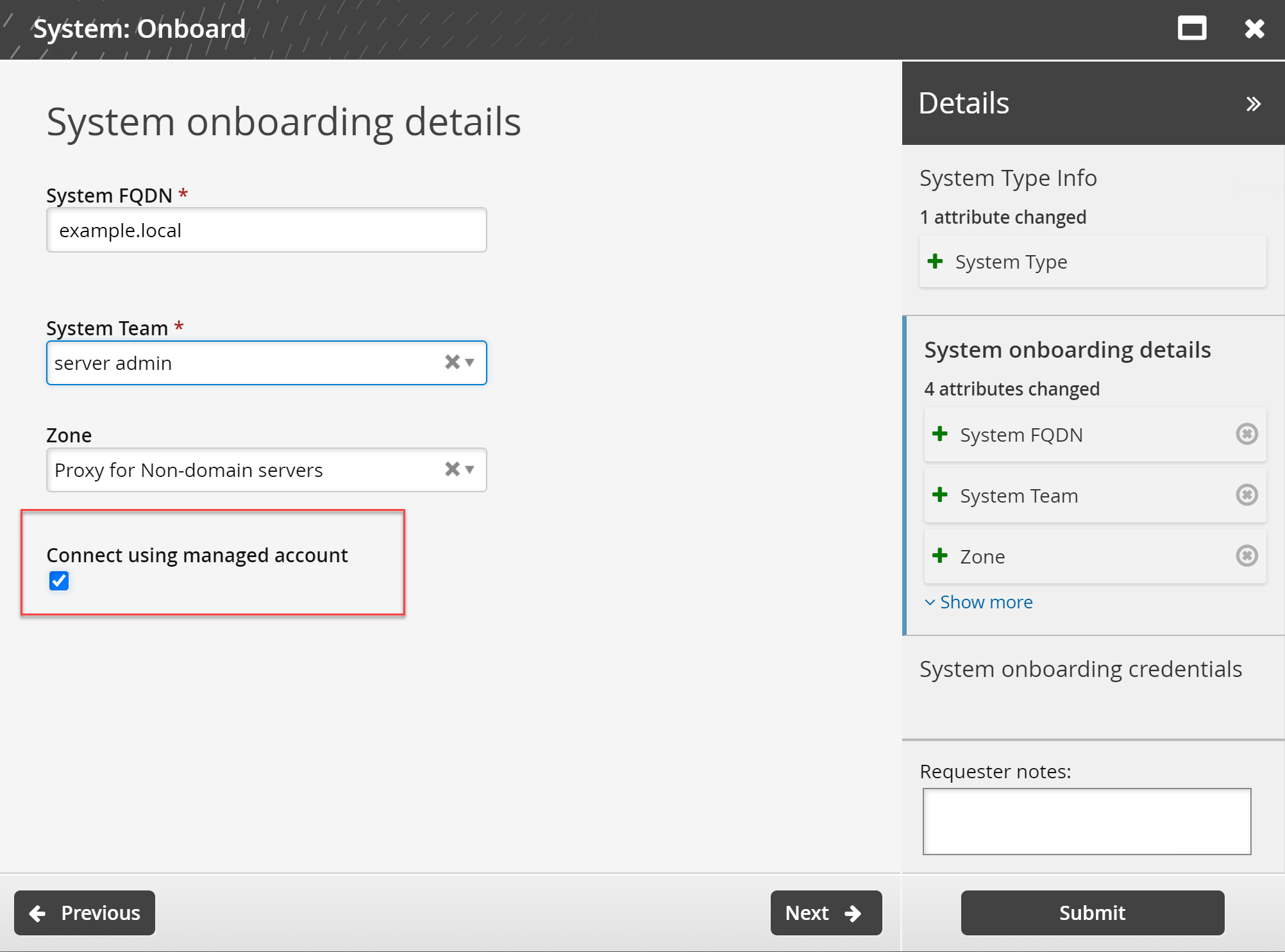
Select the System Type and click Next.
The option to select Connect using managed account is available.