Configuring authentication modules
A number of configuration options are displayed in the Module configuration table, depending on the module type.
To configure a module:
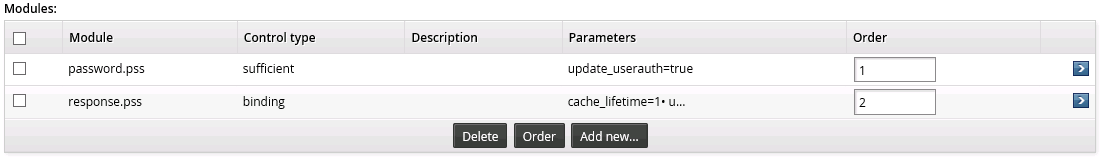
On the authentication chain's configuration page, select the saved module so that it is highlighted in green, and the configuration options are displayed below.
Set options as required:
Click Update.
Password authentication module (password.pss)
The password authentication module runs the built-in password.pss authentication program. Set the following for the password authentication module:
If module succeeds, bypass this module in failed attempt retries | The module is not shown again for authentication if the authentication chain fails and is retried from a failed attempt and the module had succeeded in a previous attempt. |
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. Note : If a product administrator helps another user via the HELPDESK_LOGIN chain, and the Increment lockout counter when this module fails option is disabled for any of the modules in that chain, then the global fail counter will still increase if the product administrator fails to correctly answer any of the questions during help desk authentication. However, this does not cause the user to be locked-out, even if the number of failed attempts reaches or exceeds the value set by MAX USERAUTH FAILURE. |
Security questions module (response.pss)
The security questions module runs the built-in response.pss authentication program.
Set the following for the security questions authentication module:
If module succeeds, bypass this module in failed attempt retries | The module is not shown again for authentication if the authentication chain fails and is retried from a failed attempt and the module had succeeded in a previous attempt. |
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. Note: If a product administrator helps another user via the HELPDESK_LOGIN chain, and the Increment lockout counter when this module fails option is disabled for any of the modules in that chain, then the global fail counter will still increase if the product administrator fails to correctly answer any of the questions during help desk authentication. However, this does not cause the user to be locked-out, even if the number of failed attempts reaches or exceeds the value set by MAX USERAUTH FAILURE. |
If a user does not have a valid security questions profile | Defines which action to take when a user does not have a complete security questions profile. If a user’s security question profile is incomplete and this option is set to:
CautionIf this option is set and the module is bypassed, and the remaining modules are set to either sufficient or optional , then access is not immediately granted. At least one of the remaining modules must pass in order to gain authentication. |
Interval to re-sample questions when a user fails to provide correct answers | Controls whether or not new questions are selected for a user if they previously answered incorrectly. You can choose the period of time before the questions are re-sampled from the drop-down list. When this period of time expires, a different set of security questions are randomly chosen for the user. The default is to re-sample security questions after an hour. Question sets are often configured to select a random subset of the questions in a user’s profile. For example, a user may have 5 questions enrolled in a given question set. The question set may be configured to prompt the user for a random 2 of those questions. One of the objectives of random selection is to make it harder for an attacker to predict what questions will be presented. An attacker could respond to a displayed set of questions, which he cannot answer, by abandoning the login process and trying again. This setting allows you to prevent an attacker from ”shopping” for a set of questions to which he has gathered answers. It also prevents the attacker from getting an exhaustive list of questions which might be asked of a given user, which he can then research answers to. |
Number of questions to ask during authentication | Provides more control over how many questions to ask from each question set. If you do not change this setting, it defaults to the setting for each individual question set. You can choose:
|
Configuration notes for the Security questions module:
Modules for external security question sets should be set to the effective setting, and all other question sets should be set to (None). These modules should also have the From all question sets value set to (None).
The external question sets should be set to 0 when configuring values for other question sets, such as those for the user-defined and pre-defined question sets.
Selecting (None) for all of the question sets for a module resets all of the values for the question sets to use the default question set values.
When configuring a question set, if you deselect the Ask users to answer questions from this set setting:
Then the question is no longer available for use with the default login authentication chain.
External question sets still work via legacy Front-end configuration.
If you add a new question set, you may need to reconfigure the
response.pssmodule for an authentication chain. The new question set is added to existing response.pss modules for all authentication chains with the value for the number of questions to ask users/help desk set to the effective setting.
External program module (external.pss)
The external program module runs the built-in external.pss module, which interfaces with an external authentication program.
Bravura Security Fabric ships with several sample scripts that can be used with this module, listed below:
Sample script | Description |
|---|---|
| A simple demonstration of this kind of plugin. |
| Generic tools for web server (NTLM, SmartCard) authentication integration. |
| Provides authentication to anonymous users who do not have pre-existing credentials, allowing them to submit pre-defined requests for new users. |
| Allows authentication using profile attributes, such as date of birth and email address. |
These files are installed with a complete Bravura Security Fabric installation or if you selected Sample files in a custom installation. See Authentication Chains: Use Cases and Authentication Chains: Plugins for more information on using these scripts.
Set the following for the external program authentication module:
If module succeeds, bypass this module in failed attempt retries | The module is not shown again for authentication if the authentication chain fails and is retried from a failed attempt and the module had succeeded in a previous attempt. |
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. Note: If a product administrator helps another user via the HELPDESK_LOGIN chain, and the Increment lockout counter when this module fails option is disabled for any of the modules in that chain, then the global fail counter will still increase if the product administrator fails to correctly answer any of the questions during help desk authentication. However, this does not cause the user to be locked-out, even if the number of failed attempts reaches or exceeds the value set by MAX USERAUTH FAILURE. |
External program | Must be set to a plugin name |
Target system to use for address and credentials | This is the target system ID on which the user has an account. If the user does not have an account on the specified system the authentication chain will not appear. |
Interface communication protocol | Must be set to the protocol that matches the plugin you named as your external program:
|
You can customize the user interface by modifying the authchain.m4 file and recompiling the skins. See the sample files and the Customization guide for more information.
Security questions with answer scores module (scoreqna.pss)
The score based challenge and response module runs the built-in scoreqna.pss authentication program.
This module prompts users for questions from the user’s question sets. Points are provided for correct answers, and penalties are given for incorrect answers. The points are calculated to determine whether the user’s score passes the authentication threshold. A passing score is required to authenticate successfully.
If the user has not yet answered all questions, but the total score has passed the threshold, then the module immediately passes authentication.
If the user has answered some of the questions incorrectly, and the total score for the remaining questions cannot pass the threshold (even if all are answered correctly), then the module immediately fails.
Set the following for the score based challenge and response module:
If module succeeds, bypass this module in failed attempt retries | The module is not shown again for authentication if the authentication chain fails and is retried from a failed attempt and the module had succeeded in a previous attempt. |
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. Note: If a product administrator helps another user via the HELPDESK_LOGIN chain, and the Increment lockout counter when this module fails option is disabled for any of the modules in that chain, then the global fail counter will still increase if the product administrator fails to correctly answer any of the questions during help desk authentication. However, this does not cause the user to be locked-out, even if the number of failed attempts reaches or exceeds the value set by MAX USERAUTH FAILURE. |
If a user does not have a valid security questions profile | Defines which action to take when a user does not have a complete security questions profile. If a user’s security question profile is incomplete and this option is set to:
CautionIf this option is set and the module is bypassed, and the remaining modules are set to either sufficient or optional, then access is not immediately granted. At least one of the remaining modules must pass in order to gain authentication. |
Number of questions to ask during authentication | Provides more control over how many questions to ask from each question set. If you do not change this setting, it defaults to the setting for each individual question set. You can choose:
|
Points for correct answers | The number of points that are added to the score for each correctly answered question. You can choose:
|
Penalties for incorrect answers | The number of points that are deducted from the score as a penalty for each incorrectly answered question. You can choose:
|
Authentication thresholds |
|
Configuration notes for the Score base challenge and response module:
Selecting "(None)” for all question sets for a module resets all of the question set values to the default question set values.
When configuring a question set, if you deselect the Ask users to answer questions from this set setting, then the question is no longer available for use with the default login authentication chain.
If you add a new question set, you may need to reconfigure the
scoreqna.pssmodule for an authentication chain. The new question set is added to existingscoreqna.pssmodules for all authentication chains that have the value for the Number of questions to ask during authentication set to the effective setting.Use case: A question set (for example, the pre-defined set) is disabled and the Security questions with answer scores (
scoreqna.pss) module is configured for use with other question sets (for example, the user-defined set).If the question set that was previously disabled is now re-enabled, it cannot be used within the
scoreqna.pssmodule until the module has been re-configured. For example, a user would still only be prompted for questions from the user-defined set after the pre-defined set has been re-enabled and before thescoreqna.pssmodule has been re-configured.The
scoreqna.pssmodule would have to be modified in order to prompt for questions from this newly enabled question set.Other parameters such as the number of points for correct or incorrect answers and the values for the authentication thresholds for the passing and/or failing score should also be adjusted accordingly to account for the newly added/enabled question set.
Use case: Both the user-defined and pre-defined questions sets are enabled and the Security questions with answer scores (
scoreqna.pss) module for a custom authentication chain is configured to use questions from both of the question sets.If one of the question sets has been disabled, that particular question set will not be available for use with the
scoreqna.pssmodule.The authentication chain configured with this module will also not be usable at all until it has been re-configured to account for the missing question set that was just disabled.
Email/SMS PIN (emailsmspin.pss)
The Email/SMS PIN module runs the built-in emailsmspin.pss authentication program. This module will send a random PIN to the user via an email-to-SMS gateway or to the users email address.
Set the following for the Email/SMS pin authentication module:
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. Note: If a product administrator helps another user via the HELPDESK_LOGIN chain, and the Increment lockout counter when this module fails option is disabled for any of the modules in that chain, then the global fail counter will still increase if the product administrator fails to correctly answer any of the questions during help desk authentication. However, this does not cause the user to be locked-out, even if the number of failed attempts reaches or exceeds the value set by MAX USERAUTH FAILURE. |
If user hasn’t registered an email/mobile phone number: | Defines which action to take when a user does not have the required email, mobile phone number and/or SMS gateway attributes defined:
|
Target system to use for address and credentials | This is the target system ID on which the user has an account. If the user does not have an account on the specified system the authentication chain will not appear. |
Email/SMS PIN settings | Will define the composition of the PIN and how the PIN will be delivered to the user. PIN length – The length of the randomly generated PIN that is sent to the user. Can be set from 4 to 32 characters in length. Type of generated PIN – Choose Numeric , Upper and lowercase , or Alphanumeric for the PIN composition for the user. Time (in minutes) before PIN expires – The period of time hat the PIN will be valid. The default is time 10 minutes. PIN delivery method – Choose whether you want the PIN to be delivered via Email or Email/SMS gateway . Plugin to send the generated PIN – The plugin that will be used to send the generated PIN. The default is the GLOBAL MAIL PLUGIN . |
Attributes | Defines what profile attributes will be used for sending of the PIN. Note: In order for a profile attribute to be listed it must be configured with Allow for authentication chains selected. Profile attribute specifying email/mobile phone number – This attribute will determine what email address or mobile number will be used to send the PIN to the user. Profile attribute specifying mobile phone service provider – When the PIN delivery method selected is the Email/SMS gateway , this attribute will be set to the users mobile provider. |
Message settings | Defines the message content of the email being sent to the user. Sender email address for the PIN delivery message – The senders email address. The default is the SENDER EMAIL . PIN delivery message subject – The contents of the subject line being delivered to the user. PIN delivery message content – The contents of the email body being delivered to the user. PIN delivery message format – Choose the format of the email, Plain text or HTML . |
Connector package agent (agent.pss)
The connector package agent module runs the built-in agent.pss authentication program. This module will allow for authentication using either the user verify password or challenge response authentication operations directly for applicable connectors.
Set the following for the connector package agent module:
Increment lockout counter when this module fails | Increments the global fail counter each time a user fails authentication for this module. It is enabled by default. The global fail counter is managed by the MAX USERAUTH FAILURE system variable. If the number of failed attempts reaches MAX USERAUTH FAILURE, then the user is locked out. |
Target system to use for address and credentials | This is the target system ID on which the user has an account. If the user does not have an account on the specified system the authentication chain will not appear. |
Password verification operation | This is the connector operation that will be used for authentication to the target system as noted above. It may be set to one of these two operations: User verify password – Authentication will be done using the user verify password operation for the target system. Challenge response authentication – Authentication will be done using the challenge response authentication operation for the target system. Note: This may only be set for the target systems in which these are supported operations. For example, a RADIUS Authentication or RSA Authentication Manager 7.1/8.2 target system may be used for the challenge-response authentication. |
Authentication chain selector (select_chain)
The authentication chain selector module (select_chain) can run a plugin to automatically choose an authentication chain to use to log in.
Bravura Security Fabric ships with two sample scripts that can be used with this module:
chainselect.pslis a generic sample to demonstrate IP based chain selectionauthselect.pslcan be used to direct users to a single-page login page that includes ID and password fields.
For example, if the sample authselect.psl script is configured for the DEFAULT_LOGIN authentication chain, then it can be used to allow the user to enter both their user ID and password on the main page to log into the Front-end . If valid credentials are used, then the default password.pss module is used for authentication and the user is automatically logged in.
These sample files are installed with a complete Bravura Security Fabric installation or if you selected Samplefiles in a custom installation. See Authentication Chains: Use Cases and Authentication Chains: Plugins for more information.
Set the following for the authentication chain selector module:
Run this plugin to automatically select a sub-chain | Specify the name of the plugin to run to select authentication chains. The plugin accepts information from the Front-end , such as HTTP headers, posted data, and authentication chain information. |
If selected chain fails, automatically try the same chain again | Enable this checkbox to automatically reload this authentication chain if authentication to the Front-end fails. If this option is disabled (default), then users that fail authentication are redirected to the main page. |
Allow plugin to skip chain selection (plugin only) | Select this checkbox if you specified a plugin and you want to allow it to skip chain selection for users who already meet authentication requirements. |
Available chains | Select the existing authentication chains from which end users can choose. |
You can customize the user interface by modifying the authchain.m4 file and recompiling the skins. See the sample files and the Customization guide for more information.
Mobile authentication (mobileapp)
The Mobile authentication module will allow for authentication using a QR Code that is scanned from the Bravura One app that is registered for Bravura One for the user for two factor authentication.
Set the following for the Mobile authentication module:
QR code durations (default 60 seconds) | defines the amount of time that a QR Code will be displayed to the user for authentication. |
See also:
See Mobile access for more information about Bravura One and the Bravura One app.
Next: