Enabling and disabling authentication chains
Once an authentication chain is created and configured, you must enable it to make it available to users. On the Custom authentication chains page, the Status column indicates if the chain is  enabled or
enabled or  disabled.
disabled.
Enabling authentication chains
To enable authentication chains from the authentication chain's configuration page, select the appropriate checkboxes next to the authentication chains you want to enable, then click Enable.
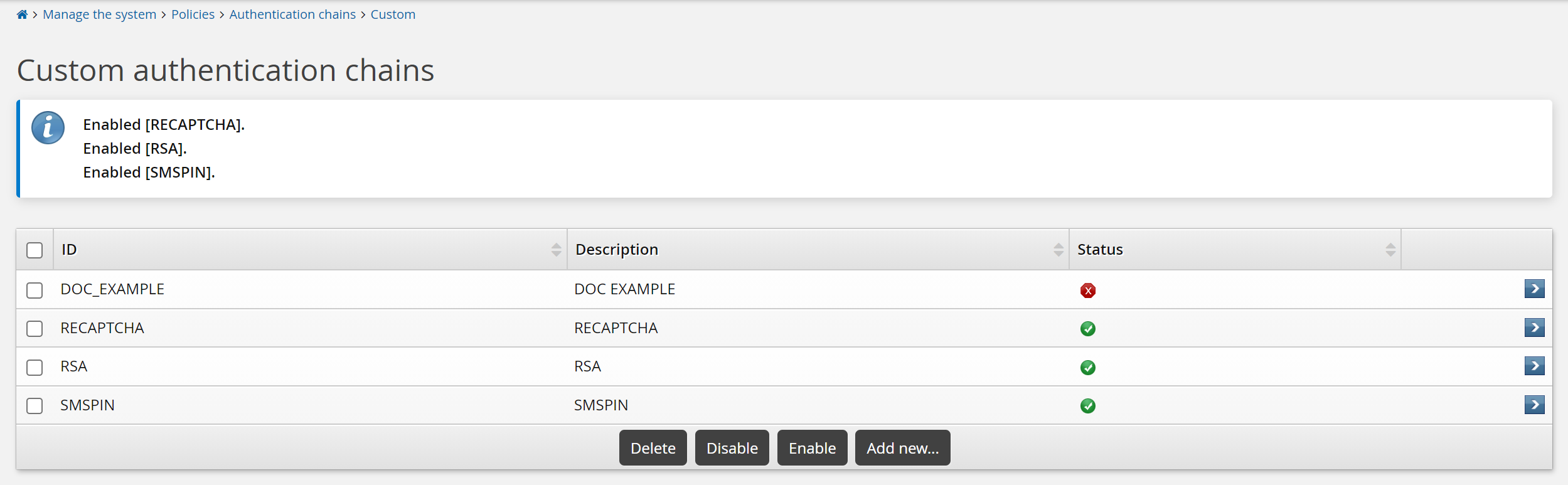
You can also enable an individual authentication chain on the Authentication chain information page by clicking the Enable button.
The built-in Front-end login, Help desk authentication, User identification service and Generic login failure authentication chains are enabled by default when Bravura Security Fabric is installed. If they have been disabled for any reason, navigate to chain’s configuration page, then click Enable.
Making authentication chains available in the authentication menu
To make an authentication chain available in the Front-end authentication menu, you must add it to the DEFAULT_LOGIN chain’s select_chain module. To do this:
From the Authentication chains menu, select Front-end login.
Click Disable.
This allows you to modify the chain.
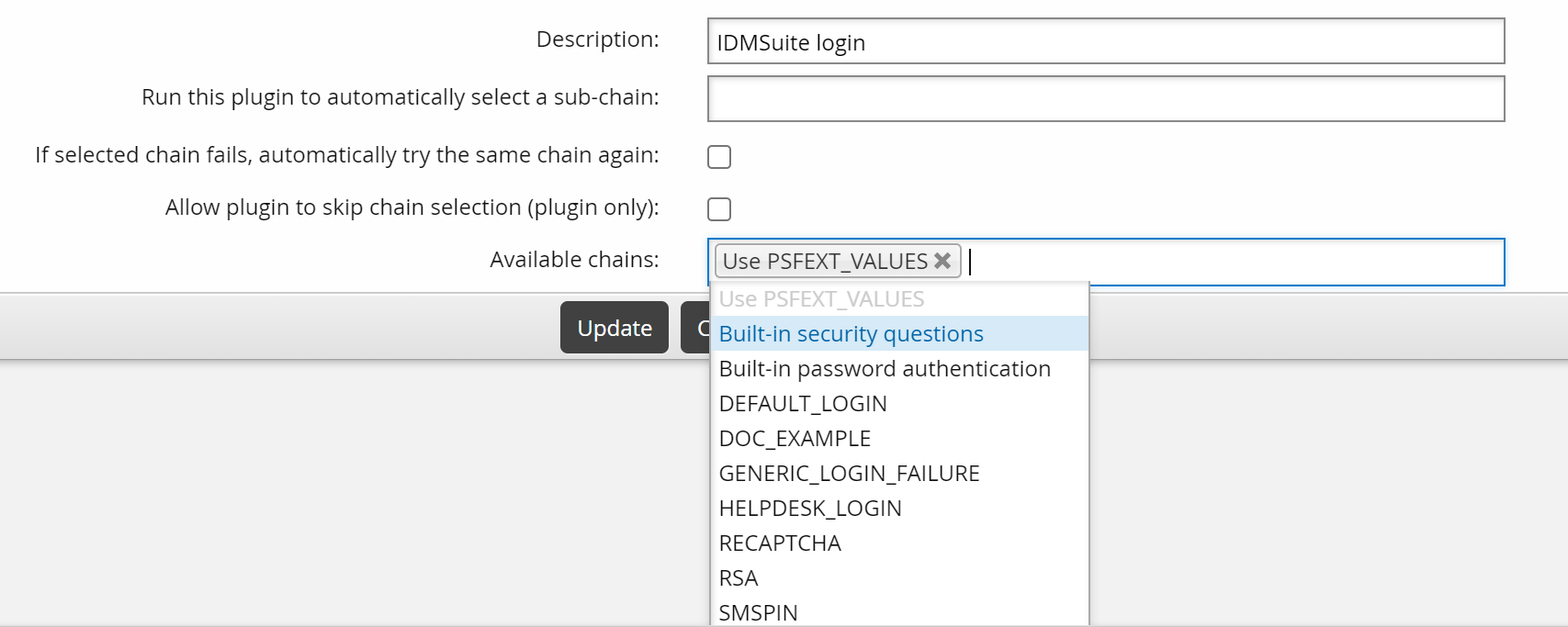
Select the
select_chainmodule.Add the chains that you want to include in the authentication menu to the Available chains list.
The DEFAULT_LOGIN chain includes Use PSFEXT VALUES by default, to include authentication methods configured in the Front-end .
Click Update below the module settings.
Click Enable to enable the authentication chain.
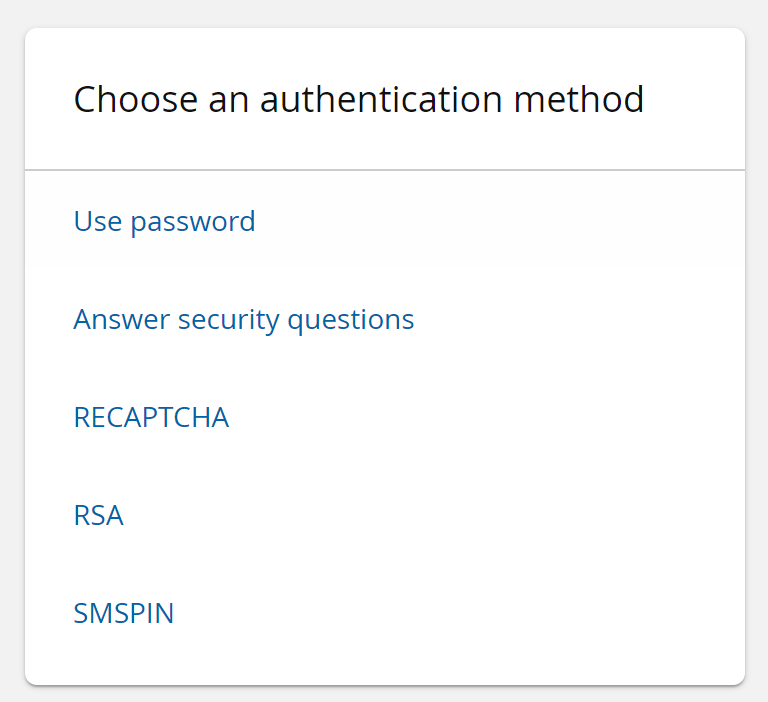
The additional authentication chains are now available to users when they log in using the Front-end .
Specifying an authentication chain within a URL
You can specify a certain authentication chain within the Bravura Security Fabric URL. This allows you to direct a user to a preferred method of authentication, instead of the user being prompted to select an option on their own.
For example, the specified user is directed to the first page of the specified authentication chain:
https://<server>/<instance>/?LANG=en-us&USERID=<user>&PSF_EXT=<authchain>
Where:
<server>is the Bravura Security Fabric server<instance>is the name of the Bravura Security Fabric instance<user>is the user for whom you are creating the URL<authchain>is the name of the authentication chain to which you are directing them.
Disabling authentication chains
To disable the built-in Front-end login, Help desk authentication, User identification service or Generic login failure authentication chain, to navigate to the chain’s configuration page, and then click Disable.
To disable custom authentication chains, navigate to the Custom authentication chains page, select the appropriate checkboxes next to the authentication chain you want to disable, then click Disable.
You can also disable an individual custom authentication chain on the Authentication chain information page. Select the custom authentication chain and click Disable.
If you disable the DEFAULT_LOGIN chain, then all authentication chain functionality within Bravura Security Fabric is disabled and is replaced by legacy behavior; that is, Bravura Security Fabric only uses authentication methods configured in the Front-end . Custom authentication chains are not able to be used if DEFAULT_LOGIN is disabled.
Configuring the help desk chain
The Help users (IDA) module has its own customizable authentication chain called HELPDESK_LOGIN, enabling you to configure the way that help desk users must authenticate on behalf of other users before they are allowed to access a user’s profile.
The HELPDESK_LOGIN authentication chain uses security questions by default, but can be configured to use other authentication modules or additional authentication chains as methods of authentication. To do this, use the same method used for configuring the DEFAULT_LOGIN chain .
By default, this authentication chain is configured to force the help desk user to answer the user’s built-in security questions before they can access the user’s profile. There are two settings that work together to configure whether or not a help desk user can bypass another user’s security questions during authentication to gain access to the user’s profile:
The "Bypass security questions" user access rule
The ADMIN AUTHUSR MANDATORY system variable
When this chain is enabled the help desk user can use the main menu link to exit from a user’s security questions.
The behavior of these settings depends on whether the user’s security profile is complete or incomplete:
Incomplete security profile | When ADMIN AUTHUSR MANDATORY is: Disabled : help desk users can access a user’s profile, whether or not they have the "Bypass security questions" user access rule. Enabled : help desk users only have access to a user’s profile if they have the Bypass security questions user access rule. If they do not have this user access rule, then an error message is displayed when the help desk user accesses the user’s profile. This error message is not displayed if ADMIN AUTHUSR MANDATORY is disabled. |
Complete security profile | When the "Bypass security questions" user access rule is: Granted : help desk users can skip authentication by security questions and gain access to the user’s profile. In this case, ADMIN AUTHUSR MANDATORY can be either enabled or disabled. Not granted : help desk users cannot skip authentication by security questions. The security questions must be correctly answered before access is granted to the user’s profile. In this case, ADMIN AUTHUSR MANDATORY can be either enabled or disabled. |
Click below to view an example HELPDESK_LOGIN authentication chain configuration:
Configuration notes
By default, the HELPDESK_LOGIN authentication chain is configured to use the built-in security questions authentication method to prompt for a user’s questions.
If the HELPDESK_LOGIN authentication chain is enabled, and the Ask users to answer questions from this set option is:
Enabled for a question set, and the question set is enabled, then help desk users are prompted with a user’s security questions, regardless of the value for the help-desk permissions.
Disabled for a question set, then help desk users are not prompted with a user’s security questions, regardless of the value for the help-desk permissions; even if the question set is enabled.
If the HELPDESK_LOGIN authentication chain is disabled:
And help-desk permissions for a question set is set to Requires authentication with security questions, then the Ask users to answer questions from this set is ignored. The help desk user will be prompted for a user’s questions from this set as long as it is enabled, and the value for ADMIN AUTHUSR MANDATORY is enabled as well.
And help-desk permissions for a question set is set to either Not allowed to view security questions or Allowed to view security questions, then the help desk user is not prompted with a user’s questions from this question set, regardless of whether Ask users to answer questions from this set is enabled or disabled; even if the question set is enabled.
The purpose for this behavior is to help distinguish the question sets that are marked for help desk authentication from the question sets that are intended for use with the default login authentication to the Front-end ; for example, if:
The HELPDESK_LOGIN authentication chain is disabled, and;
The user-defined question set has the Ask users to answer questions from this set option disabled, and the help-desk permissions is set to Requires authentication with security questions , and;
The pre-defined question set has the Ask users to answer questions from this set option enabled, and the help-desk permissions is set to Not allowed to view security questions, and;
Both question sets are enabled
then the built-in security questions method would allow help desk users to authenticate (on behalf of other users) with questions from the user-defined question set, and users could log into the Front-end using the pre-defined question set.
If any errors are encountered in the HELPDESK_LOGIN authentication chain during the authentication process, the help desk user is denied access to the user’s profile. The authentication chain must be fixed before access is possible.
If a help desk user fails the help desk authentication process when attempting to access the user’s profile, then the global fail counter still increases for the user. The global fail counter only increases for failed help desk user authentication attempts if the HELPDESK_LOGIN authentication chain is enabled. If the help desk user ’s failed attempts cause the global fail counter to reach or exceed the value set by MAX USERAUTH FAILURE , this does not lock out the help desk user .
If the global fail counter reaches or exceeds the value set by MAX USERAUTH FAILURE , this does not lock out the user or prevent them from logging into the Front-end . The user can still log into the Front-end , but if the global fail counter has reached or exceeded its limit, then the user is only allowed one authentication attempt. If they fail this one attempt then they are locked out, but authenticating successfully resets the global fail counter.
If you disable the HELPDESK_LOGIN chain, then legacy behavior is used in it’s place; that is, only security questions are available as an authentication when help desk users authenticate to access a user’s profile.
When HELPDESK_LOGIN is disabled:
The ADMIN AUTHUSR MANDATORY system variable must be enabled in order for the help desk user to be prompted with the user’s security questions.
The security questions use the question set settings, not the authentication chain settings.