Example:Configure dynamic authorization
In this example, you will set up authorizers for the target systems, so that when a user requests a change to an existing account, the recipient’s direct or indirect manager can authorize the request. An indirect manager could be the manager’s manager, and so on, up the chain of command.
Requirements
This use case assumes:
Bravura Workforce Pattern is installed.
There is an Active Directory target system set up as a source of profiles.
User BERNAP manages user DARAK.
BRYANW's input is required for any group requests to which he in assigned, as configured in Example: Configure static authorization
Click below to view a demonstration.
Assign dynamic authorizers to resources
To set up authorizers for existing accounts:
Log in to the Bravura Security Fabric Front-end (PSF) as superuser.
Click Manage the system > Resources > Target systems > Manually defined .
Select the AD target.
Click the Authorization tab.
Change the Minimum number of authorizers to
1.Change the Number of denials before a change request is terminated to
1.Click Update for the updated section.
In the user classes table at the bottom of the form, click Select… .
Select the checkbox for _MANAGER_INDIRECT_ , and click Select.
Bravura Security Fabric displays an error because you have not mapped the participants in the user class yet.
Under Participant mapping for MANAGER, select AUTHORIZER.
Under Participant mapping for SUBORDINATE, select REQUESTER.
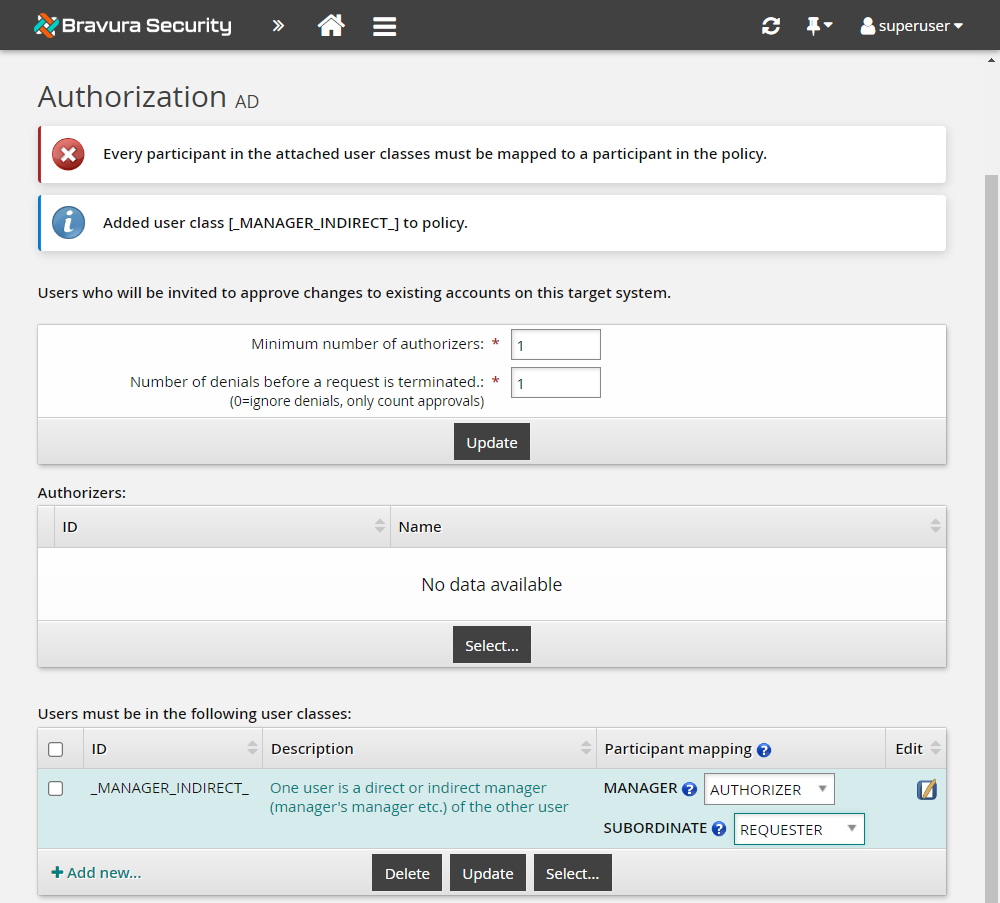
Click Update.
Test the user class participant mapping
To test if a change request will have enough authorizers:
Click Test… in the user class table.
In the List matching users: section, select AUTHORIZER from the List: drop down.
In the REQUESTER field, also under List matching users: , type DARAK .
Click List.
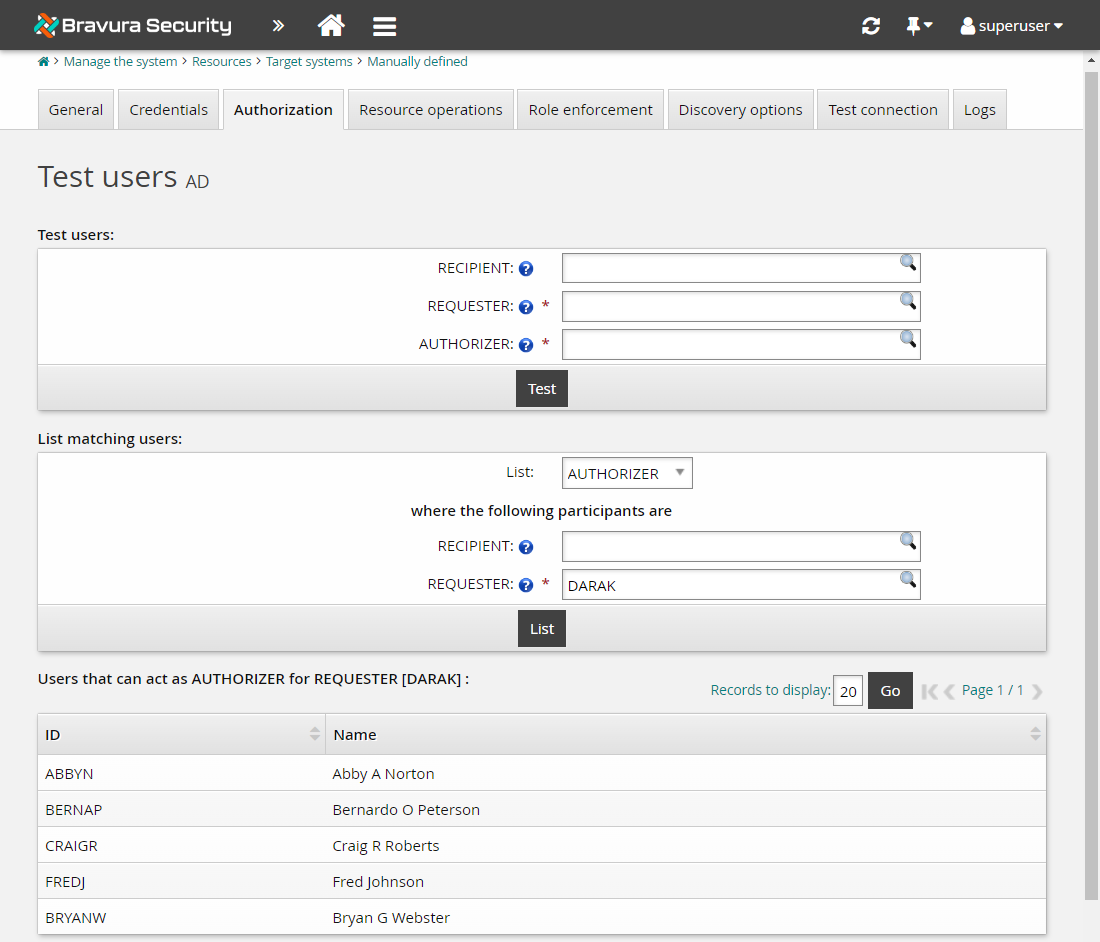
Bravura Security Fabric will list DARAK’s manager, BERNAP, and all the managers in the chain of command above BERNAP as well.
You have now set up dynamic authorization for change requests related to existing accounts.
Submit a request to change attributes
Log in to the Front-end (PSF) as DARAK.
Click View and update profile in the MY PROFILE section.
Select Update attributes near the bottom of the page.
The request wizard opens.
Fill in the following information:
Other names Barb
Click Submit.
Review the request details and authorizers. You should see that the request is pending approval from BERNAP and the managers in the chain of command above him.
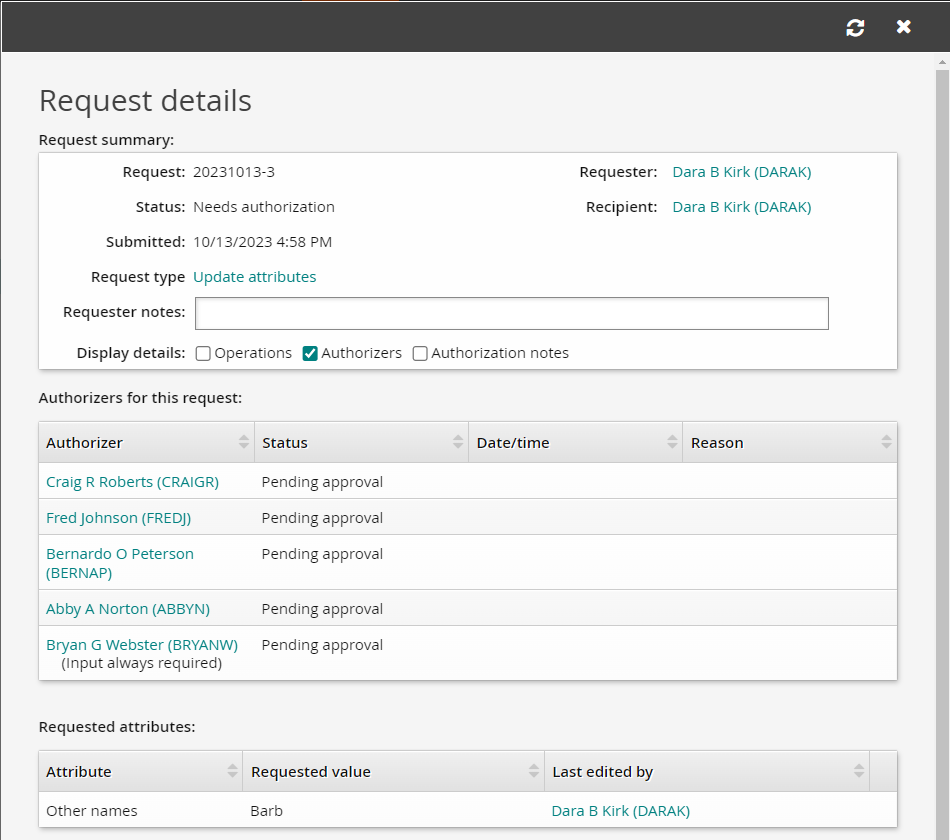
Approve the attribute request
Log in to the Front-end (PSF) as BERNAP.
Click There are 1 request(s) awaiting your approval.
The Requests app opens.
Select the Update attributes request from the Results panel.
The details of the request will appear in the Actions panel .
Click Approve.
Click the Approve button to confirm.
Final approval
Even though the authorization requirements for the target system are met, BRYANW’s approval is still required because we set the Input is required before request can be approved option when we configured static authorization .
Log in to the Front-end (PSF) as BRYANW .
Click There are 1 request(s) awaiting your approval.
The Requests app opens.
Select the Update attributes request from the Results panel.
The details of the request will appear in the Actions panel .
Click Approve .
Click the Approve button to confirm.
The status of the request should change to "Approved, performing requested operations".
Navigate back to DARAK’s home page.
Click View and update profile in the MY PROFILE section.
The Other names field will now be populated with our change.
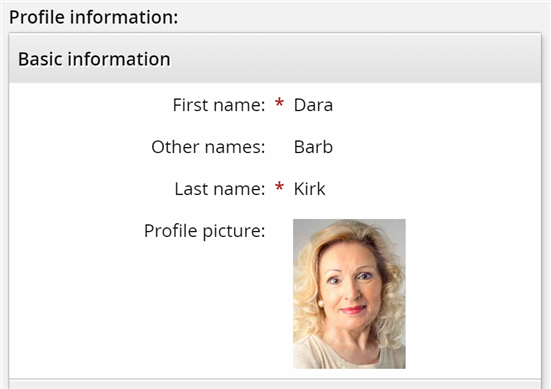
If you can see that the change to Barb has been made successfully to the Other names field for Dara, you have completed the lab properly.