Mainframe Connector Components
Functional overview
Mainframe Connector executes as an MVS subsystem, which receives notification of password changes and forwards them to a Bravura Pass server on the TCP/IP network. The Bravura Pass server validates the strength of new passwords, and may reject password changes on the host system. The Bravura Pass server also synchronizes passwords for users if they have been accepted by its own strength rules and by the host system security product.
The Mainframe Connector subsystem is also capable of listening for incoming requests from the Bravura Pass server, the Bravura Identity server, or the Bravura Privilege server. The incoming requests can be any of the following:
Verification of a specified userid/password combination.
Changing the password of a specified userid if the current password is valid.
Resetting the password of a specified userid if a supplied administrator userid/password combination is valid.
Providing feedback on all userid/username combinations defined to the security product database.
Expiring the password of a specified userid if a supplied administrator userid/password combination is valid.
Resetting and expiring the password of a specified userid if a supplied administrator userid/password combination is valid.
Revoking (suspending) access of a specified userid if a supplied administrator userid/password combination is valid.
Resetting revoked (suspended) status of a specified userid if a supplied administrator userid/password combination is valid.
Performing a revoke (suspend) status query for a specified userid if a supplied administrator userid/password combination is valid.
Resetting the password phrase of a specified userid if a supplied administrator userid/password combination is valid.
The mainframe listener does not support passphrase verification. If the mainframe is configured to use passphrase verification, the result is the mainframe listener does not return anything. That functionality is not available. Possible workarounds include:
Change the target configuration of the mainframe target so that verifications are only done through passwords, not passphrases
Take the mainframe target out of the Authentication list, so it does not attempt to verify through the mainframe target
Use the second option, but provide another target type that are a Source of Record so that the accounts have the ability to authenticate without depending on the mainframe.
Mainframe Connector , using its embedded Bravura Identity functions, supports the following Bravura Identity based protocols:
Create a new userid based on the attributes of a specified model userid
Create a new userid based on the attributes of a specified model userid and additional specified attribute values
Delete an existing userid
Provide feedback on the current attributes for a specified userid
Update, add, and delete attributes for a specified userid
If Mainframe Connector is running on a z/OS system that is using RACF or TopSecret as its security product, the following incoming requests are also supported:
Provide a list of all defined groups
Provide a list of all defined groups and their associated userids
Provide a list of the userids associated with specified groups
Add a userid to a group
Remove a userid from a group
The components of the Mainframe Connector user management system are shown below.
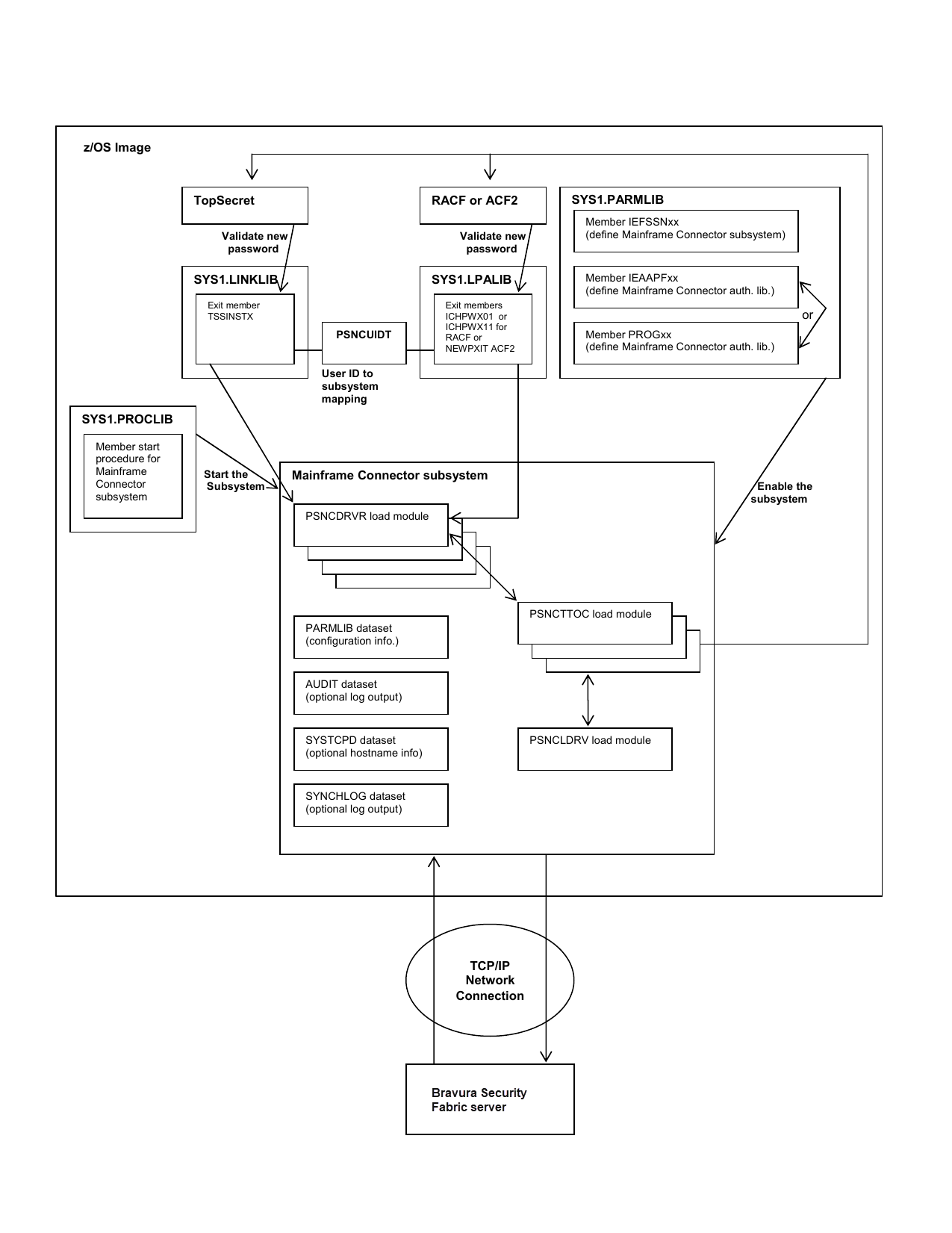
Components on z/OS
Mainframe Connector for z/OS is comprised of two major components. The first component, the Mainframe Connector subsystem, runs as a z/OS started task. It performs the bulk of the work required for Mainframe Connector processing.
The second component is an interface to the host security product (RACF, TopSecret, or ACF2) via the security product’s "new password" exit. Each request for a password change is first submitted by this exit to Mainframe Connector for validation. Upon validation completion, Mainframe Connector returns a response to the exit specifying whether or not to proceed with the change.
TCP/IP connectivity
For Mainframe Connector to operate, a TCP/IP connection must be available to a Bravura Security Fabric server. Ensure that the z/OS system that will support the Mainframe Connector subsystem is connected to the TCP/IP network that contains the Bravura Security Fabric server.
IP host name resolution
The Mainframe Connector subsystem normally converts the name of the Bravura Security Fabric server into an IP address using DNS (IP dotted decimal addresses are also supported). Accordingly, DNS should be configured on each z/OS image where the Mainframe Connector subsystem is installed.
If DNS support is not provided through other means, the Mainframe Connector subsystem procedure may contain the SYSTCPD data definition statement. This dataset can contain information that maps host names (such as the name of the Bravura Security Fabric server) to IP addresses.
There are a number of techniques available in z/OS TCP/IP implementations for providing DNS support. Using the SYSTCPD DD is one of these techniques. The method for providing DNS support specific to your site should be used when installing Mainframe Connector for z/OS.
Password Change Exit
If z/OS system password reset events will be used to trigger password resets on other systems or applications supported by Bravura Pass (a process known as transparent synchronization), it will be necessary to install security product specific, Mainframe Connector supplied, exits. Mainframe Connector supports the three standard z/OS host security products: RACF, ACF2, and TopSecret. In each case, an installation exit is available to capture password change events prior to the security product updating its database. The Mainframe Connector supplied versions of these exits will need to be installed if Bravura Pass password strength validation and transparent synchronization will be used.
For RACF, password change events are captured in the ICHPWX01 RACF exit. For RACF, pass phrase change events can also be captured in the ICHPWX11 RACF exit.
For ACF2, password change events are captured in the NEWPXIT ACF2 exit.
For TopSecret, password change events are captured in the TSSINSTX TopSecret exit.
Care must be taken to ensure that there are no conflicts in the use of these installation exits. If RACF or ACF2 are being used for the security product, Chapter 16 discusses what should be done if multiple subsystems need to make use of the new password exit.
If TopSecret is being used for the security product and multiple subsystems are making use of TSSINSTX, contact Bravura Security to discuss what approach should be taken to properly update TSSINSTX.
Mainframe Connector subsystem
The main Mainframe Connector driver task runs as a true z/OS subsystem. Mainframe Connector must be defined to z/OS as a subsystem as described in Defining the Subsystem Name .
System libraries
Mainframe Connector uses or requires updates to the following z/OS system libraries or their concatenation (where applicable):
SYS1.PARMLIB
SYS1.PROCLIB
SYS1.LPALIB (RACF or ACF2)
SYS1.LINKLIB (TopSecret)
SMP/E datasets