Example: Integrate with Active Directory Federation Services IdP
In this example, we use two endpoints for the federation integration:
The SP, Bravura Security Fabric : https://app.demo.local/instance/
The IdP, Active Directory Federation Services: https://adfs.demo.local/adfs/ls/
The domains and instance name have to be changed to fit the instances being integrated. The rest of the paths are fixed.
Configure Relying Party Trust in Active Directory Federation Services (AD FS)
Open the AD FS Management Tool in Server Manager.
Click on Add Relying Party Trust in Actions.
Keep the default "Claims aware" option and click Start.
Choose the "Enter data about the relying party manually" option, and click Next .
Type the name by which the instance of our product being added as Service Provider is known in the customer's infrastructure, for example “Bravura Security Fabric” in the Display name field and click Next .
Click Next on the page to accept defaults.
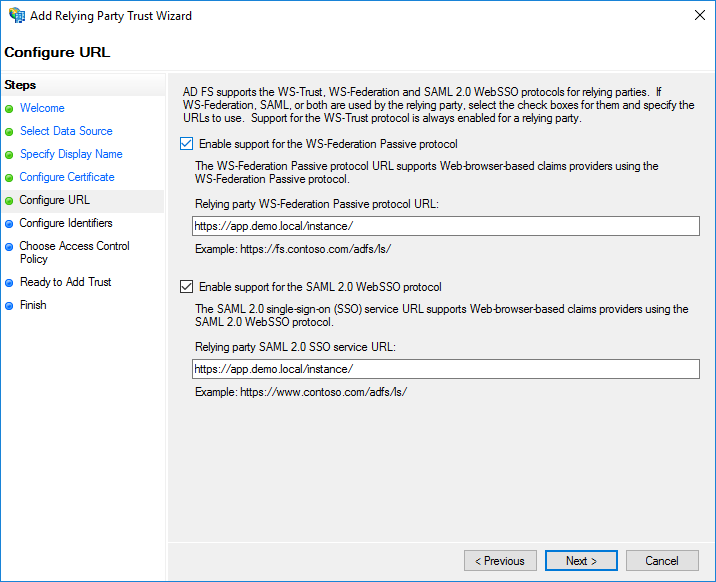
Select "Enable support for the WS-Federation and SAML" in the Configure URL field, type
https://app.demo.local/instance/then click Next .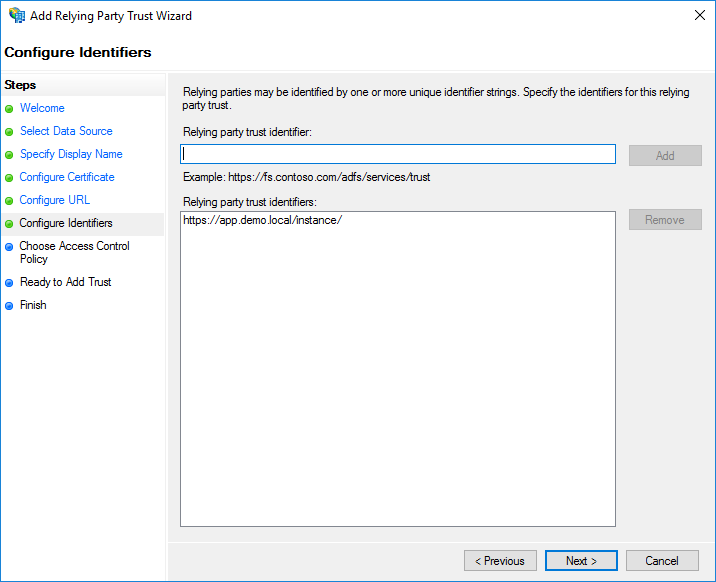
If there is no entry in the Relying party trust identifiers list on the page, type
https://app.demo.local/instance/in the identifiers field and click Add, then Next.Click Next in the page to accept defaults.
Click Next in the page to accept defaults.
Click Close.
In the AD FS Management tool navigate to and select "Bravura Security".
Click on the Edit Claim Insurance Policy.
Click Add Rule.
Keep default "Send LDAP Attributes as Claims" in the page, then click Next .
Type
send LDAP attributesin the Claim rule name field, select "Active Directory" in Attribute Store, select "SAM-Account-Name" in LDAP Attribute and "Name ID" in the Outgoing Claim Type, then click OK.
Export signing certificate from AD FS
Open the AD FS Management Tool in Server Manager.
Navigate to Services > Certificates.
Select Token Signing certificate and then select View Certificate from the menu (or right click > View).
Click the Details tab.
Click Copy to File and click Next .
Select "Base64 encoded X.509" in the page.
Add a descriptive Name (for example "adfs-domain-name-environment.cer" - with the actual domain name being integrated and environment type [dev, uat, prod]), then save the exported file into the Temp folder and click Next .
Click Finish to complete the export process.
Copy the exported certificate into the plugin\ folder of the Bravura Security Fabric instance.
Configure SAML Authentication in Bravura Security Fabric
See generic instructions in Set up Bravura Security Fabric to authenticate with an IdP .
The instance profiles must be created from the Active Directory domain being integrated, or at least a profile attribute has to be populated with that Active Directory's UPN.
When editing the fedidp_samlauth module options ( Step 3-Step 5 ), enter details of the AD FS server in the page:
Single sign-on URL:
https://adfs.demo.local/adfs/ls/ (this is the AD FS endpoint)Issuer to send to identity provider:
https://app.demo.local/instance/(this is the Relying party identified configured in AD FS)Single sign-on binding:
HTTP POSTIdentity provider issuer:
http://adfs.demo.local/adfs/services/trustIdentity provider public certificate file (.cer):
adfs-domain-environment.cer(the one saved from AD FS)Identity provider subject type:
Profile ID(if the profile name matches the AD UPN, otherwise choose "Profile attribute").Subject profile attribute: Leave blank if ProfileID above, otherwise the name of the profile attribute containing the AD UPN - usually EMAIL.