Reorder available chains in select_chains module
When providing a choice of available authentication chains at login time, the chains listed in the Available chains list of the select_chain module get displayed for the user in the alphabetical order of their chain IDs, for example:
Configure Manage the system > Policies > Authentication chains > Front-end login .
In the Available chains setting, list:
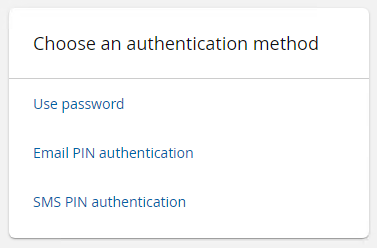
Use PSFEXT_VALUES EMAILPIN SMSPIN
When users log in, Bravura Security Fabric displays the options in the in the alphabetical order of their chain IDs (after Use PSFEXT_VALUES):
Requirements
This use case assumes that:
Bravura Security Fabric and Connector Pack are installed.
User has the administrative privilege and can access the Bravura Security Fabric server
Steps
Identify all cases where reordering is required. This will mean that you need to adjust the authentication chain names only once.
Export the authentication chains.
Edit the exported .cfg file(.exp file) to globally rename SMSPIN so it sorts above PERSONAL_EMAILPIN (for example ASMSPIN).
Re-import the authentication chains according to the article listed above.
Test the results.
When successful, update any custom components which add authentication chains, to use the new names for the authentication chain IDs.
If only default components are used, override them with custom ones that add the new chain ID names.
Now, the Available chains field lists chains as:
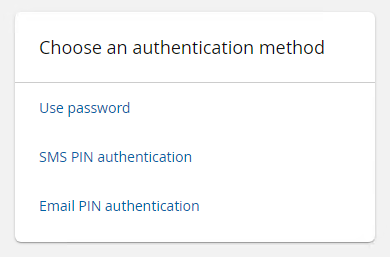
Use PSFEXT_VALUES ASMSPIN EMAILPIN
Bravura Security Fabric displays:
The method above is recommended even though manually creating a copy custom authentication chain is also possible only if the authentication chain does not have any of its modules registered (and it will require manual changes to all other chains where this chain is referenced).
Any other components and/or policy tables which may refer to the ID-renamed authentication chains must be edited as well. If component changes are required, do not edit default components; make custom ones.
Some other authentication chain modules (for example challenge-response modules like Okta or Duo) also provide their options in the order they are sent back from the API of the respective authentication service, or follow built-in order.