Example: Configure group entitlement attributes
In Example: Updating group attributes , you learned how to update a resource attribute that was mapped to a group attribute on Active Directory. Resource attributes can also be configured as entitlement attributes to define the relationship between two resources.
The built-in ENTITLEMENT_EXPIRY_DATE attribute can be used to trigger an event to complete an action; for example, when a member’s expiry date arrives, an email is sent to prompt the removal of that user from the group.
In this example, we add a resource attribute group so that users can set this expiry date in a pre-defined request.
Assumptions
This example assumes:
Bravura Workforce Pattern is installed.
The "AD" Active Directory target system is configured as a source of profiles.
Group owners in AD are configured as group managers in Bravura Identity .
Click below to view a demonstration of this example.
Add a resource attribute group
Log in to the Bravura Security Fabric Front-end (PSF) as superuser .
Click Manage the system > Resources > Resource attribute groups.
Click Add new… .
Enter the following information:
ID
Group_entitlements_attrsDescription
Group entitlement attributesResource type
Account group memberships
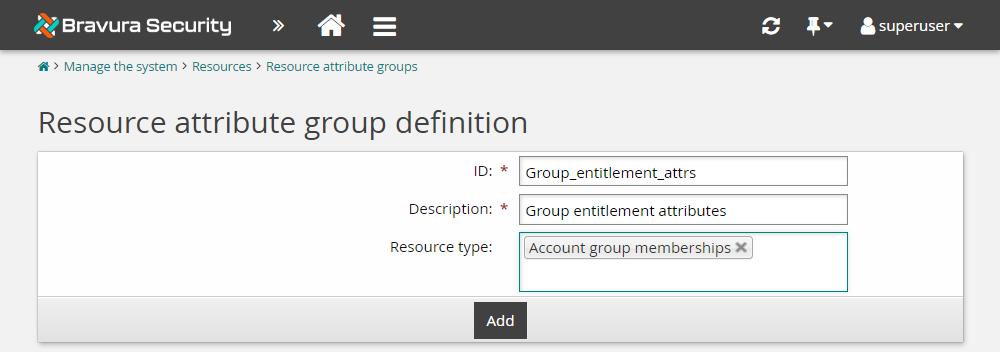
Click Add.
Click the Access control tab.
Select "Allow read" and "Allow write" for ALLUSERS.
Click Update.
Click the Members tab.
Click Select… .
Select "ENTITLEMENT_EXPIRY_DATE".
Click Select .
Click the Display criteria tab.
Ensure the Display type is set to "Main".
Click Update.
We have now configured the ENTITLEMENT_EXPIRY_DATE attribute so that it can be updated by users. In the next example, we will configure the _GROUP_CREATE_ pre-defined request to include the ability to set an expiry date for each group member.