Demo/Lab: Targeting with SQLite example
In this lab we build a connector to integrate with SQLite.
Prerequisites
Bravura Security Fabric is installed.
Steps
Find the
agtsqlitedemo.pysample script andagtsqlitedemo.concontainer file in <instance>/samples folder.Copy
agtsqlitedemo.pyandagtsqlitedemo.coninto your <instance>/agent folder.With PyCharm or the editor of your choice, open your
agtsqlitedemo.pyscript.Note that the connector bootstraps an SQLite database schema and preloads accounts and groups. This is not typical connector behavior, but given that this is a demo connector, this simplifies the creation and loading of an SQLite database with useful test accounts and groups.
The name of the database file is cereal-1.2.db.
If the cereal-1.2.db database does not already exist, the sample script will create the database schema and preload hard coded values.
With PyCharm, you can turn on "structure view" to get a better understanding of what is in the Python file. To turn on this feature:
Go to View > Tool Windows and select "Structure".
The structure panel will appear in the bottom left corner of your screen.
Click the settings cog on the right top corner of the window to select a different location for the window.
Log into Bravura Security Fabric as an administrator and create a manually defined target with the following:
Type: Demo Python Agent using SQLite
ID: MYSQLITEDEMO
Description: My SQLite Demo
Click Change next to the Address field.
Notice that, at this time, this demo has no address attributes and, therefore, does not expose any target configuration options.
Click Continue.
Set Automatically manage groups to "All groups, approval required".
Set Groups whose membership will be listed is set to "Managed groups".
Click Add on the target main page.
On the page enter in credentials. This SQLite database authenticates to the accounts and passwords stored inside the cereal-1.2.db. For this demo, start with:
Administrator ID : placeholder
Password: North*1
Confirm password: North*1
Click Update.
Select the Test connection tab
Click Test credentials .
Results will fail. Look at the code first to try and determine why it failed before looking at the logs.
Navigate back to your
agtsqlitedemo.pyscript in PyCharm.Since the connect operation failed, go to the connect definition in the code to examine the settings.
Notice there are failure codes that will return for the line:
If account.get()
If account.passwd !=cinfo["adminpw"] or account.enabled !="1":
Check the logs:
Navigate to <Program Files path>\Bravura Security\Bravura Security Fabric\Logs\<instance> .
Open the
idmsuite.logcontained in that folder with Notepad and scroll to the bottom of the file for the most recent logs. Alternatively, you can also click on the Logs tab on the target configuration page.Look for entries with
agtpython.exeprocess running and find the lines forAttempting to connect to host [MYSQLITEDEMO]...You will see a line saying
Warning: Account.get - account id does not exist [placeholder]meaning that our connection is failing because the placeholder account we used as credentials does not exist.As hinted above, we need to find an account and password that cereal-1.2.db was initially bootstrapped with. Go to the top of the script and look for the database bootstrap code.
Note the following code:
c.execute('''CREATE TABLE accounts (id text, shortid text, fullname text, passwd text, expiredpw integer, enabled integer, locked integer, expiredacct integer, email text, department text)''') ... c.execute("INSERT INTO accounts VALUES ('Administrator','Administrator','Administrator','Pa$$w0rd',0,1,0,0,'Administrator@cereal.com','The Boss')")It looks like there is an
Administratoraccount with a password ofPa$$w0rdin the SQLite database.Verify the credentials by opening up cereal-1.2.db with SQLite Brower or a similar tool. This file is located in the <instance>\agent directory. To view the contents of that file :
Open the Windows start menu and click DB Browser (SQLite) program.
Click Open Database in the top toolbar.
Navigate to the <instance>\script directory.
Select the cereal-1.2.db file.
Click Open.
Click the Browse Data tab and in the Table: field select the "accounts" table. It should be something like the following:
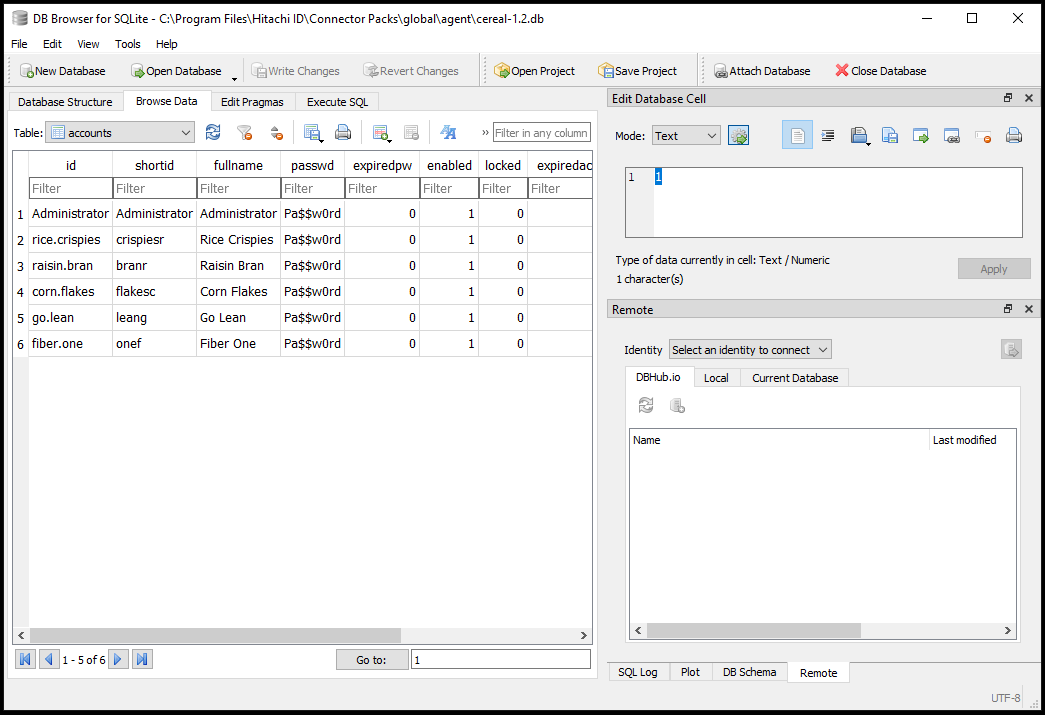
To resolve this issue, navigate back to the credential page, delete the previous credentials and enter:
Administrator ID : Administrator
Password: Pa$$w0rd
Confirm password: Pa$$w0rd
Click Save.
Navigate back to the Test connection page and click the Test connection tab.
Click Test credentials .
The test should succeed.
Click Test list .
The test should return the six users from the script since it built the database the first time we ran it.
On your Bravura Security Fabric instance, navigate to Resources > Target Systems > Manually defined.
Click the checkbox for the MYSQLITEDEMO target.
Click Run discovery at the bottom of the target list.
Confirm the action by clicking Ok in the confirmation pop-up window.
Verify the accounts and groups listed using reports:
Click the Home icon and navigate to Manage Reports > Reports > Users > Accounts. Select your Target System ID and click Run.
Navigate to Manage Reports > Reports > Roles and Groups -> Groups. Select your Target System ID and click Run.