Access to user profiles
This section shows you how to define user access rules to control access to user profiles for self-service users and help desk users. User access rules define which privileges a group of users can have, and user classes define membership criteria for each user access rule.
Types of user access rules
The main types of user profile access rules are:
Global help desk rules
Specify what help desk users can do for all other users.
Apply to users in a single-participant
The standard global help desk rules are:
ALLREQUESTERS | Defines privileges that apply by default to all regular users. By default, the membership criteria for this user access rule is defined by the _ALLUSERS_ user class. |
API_REQUEST | Defines privileges for API users. By default, the membership criteria for this user access rule is defined by the _EXPLICIT_API_USERS_ user class. |
API_TPM_REQUEST | Defines privileges for API users of Phone Password Manager . By default, the membership criteria for this user access rule is defined by the _EXPLICIT_API_USERS_TPM_ user class. |
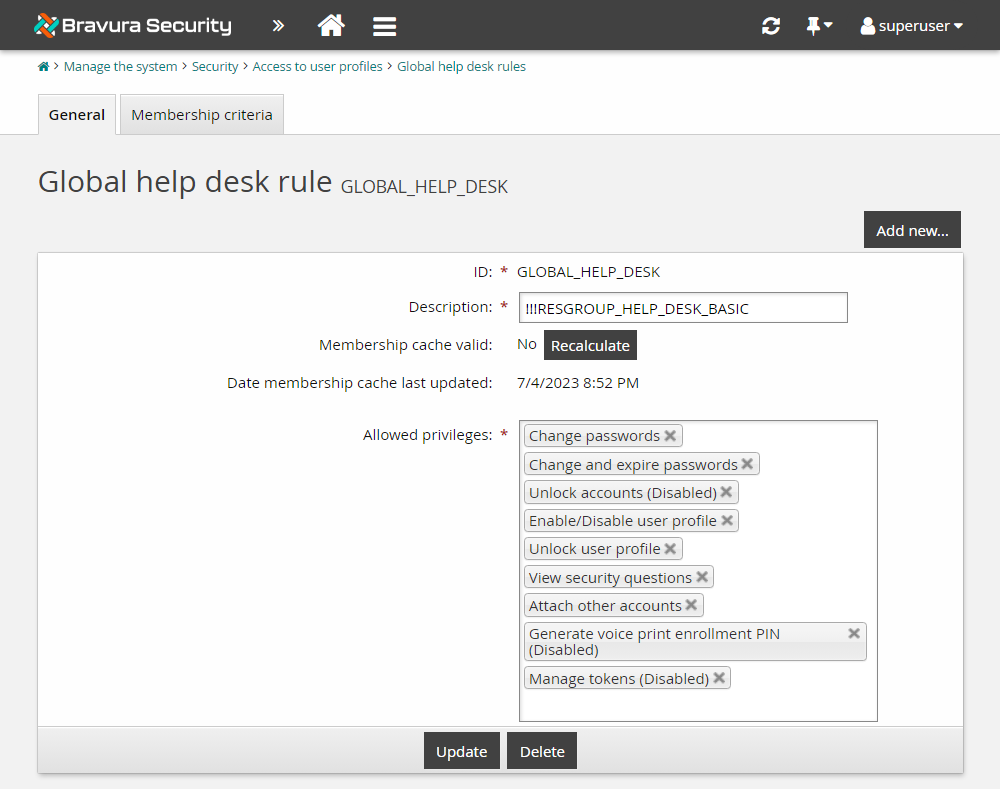
GLOBAL_HELP_DESK | Defines privileges for basic, front-line help desk users. By default, the membership criteria for this user access rule is defined by the _GLOBAL_HELP_DESK_ user class. |
HELP_DESK_MANAGER | Defines privileges for all help desk managers. By default, the membership criteria for this user access rule is defined by the _HELP_DESK_MANAGERS_ user class. Note: The |
See User access rule privileges for details on each privilege.
Self-service rules
Specify what self-service users can do for themselves.
Apply to users in a single-participant user class - that is, individual users are included based on an attribute or group membership.
The default self-service rule is:
ALL_SELF_REQUEST | All self-service users who make requests for themselves. By default, membership is defined by the _ALLUSERS_ user class. |
Note: The Unlock accounts, Manage tokens and Generate voice print enrollment PIN privileges all require configuration. If not yet configured, (Disabled) is displayed next to their name.
The Update security questions privilege has (Disabled) displayed next to it when the Update security questions is disabled. If this privilege is not selected, users are not required to update their security questions when logging in, and the link is not displayed on the main menu.
See User access rule privileges for details on each privilege.
Delegated administration rules
 Applies to Bravura Identity
Applies to Bravura Identity
Allow the same privileges as the global help desk rules.
Include users based on a relational user class – that is, there are multiple participants which are defined as either requester or recipient. An example of this is a manager-subordinate relationship.
Specify what the requester can do for the recipient.
Have no default rules defined.
See User access rule privileges for details on each privilege.
See Example: Delegate a certification segment when the reviewer is invalid for an example.
Profile comparison rules
 Applies to Bravura Identity
Applies to Bravura Identity
Are relational, and have multiple participants which are defined as requester, recipient, or model user.
Determine which requester can modify/create which recipient based on model user. They also define which requester can use which model user.
Have no default rules defined.
Can only be defined by mapping participants to user class. Privileges are determined by other rules and user groups.
Defining user access to user profiles
Requirements
You require the "Manage security" administrative privilege in order to access the Access to user profiles menu item.
Navigation steps
Use the page to configure user access rules. To navigate to this page:
Click Manage the system > Security> Access to user profiles.
Click a category:
Search for or select an existing user access rule, or click Add new...
Define:
If defining profile comparison rules, you only define membership criteria, and there is no need to select a rule. There is, in effect, one rule.
User access rule privileges
The following table describes all available user access rule privileges. It also includes the keyword, used in configuration files and plugin input/output – for each privilege. These privileges can only be granted to users who have an account on a Bravura Security Fabric target system.
Right | Keyword | Description |
|---|---|---|
Change passwords | reset | Self-service users can change their own passwords. Help desk users can change users’ passwords. |
Change and expire passwords | resetexpirepw | Help desk users can change and expire users’ passwords. |
Unlock encrypted systems/accounts | hdd | Self-service users can unlock their own encrypted systems and accounts. |
Unlock accounts | unlock | Self-service users can unlock their own target system accounts. Help desk users can unlock users’ target system accounts. |
Enable/Disable user profile | profileenable | Help desk users can enable/disable users’ profiles. |
Unlock user profile | profileunlock | Help desk users can unlock users’ profiles. |
View profile | view | Self-service users can view their own profile information. Help desk users can view the profile information of other users. |
View accounts | viewacct | Self-service users can view their own account and group information. Help desk users can view the account and group information of other users. |
View roles | viewrole | Self-service users can view their own role information. Help desk users can view the role information of other users. |
Update account (for profile comparison) | update | Self-service users can edit their own profile information when comparing their profile with another user. Help desk users can update other users’ profile information when comparing the user’s profile with another user. |
Add roles (for profile comparison) | addrole | Self-service users can add roles when comparing their profile with another user. Help desk users can add roles when comparing profiles. |
Delete roles (for profile comparison) | delrole | Self-service users can delete when comparing their profile with another user. Help desk users can delete roles when comparing profiles. |
Create account (for profile comparison) | create | Self-service users can add new accounts when comparing their profile with another user. Help desk users can add accounts when comparing profiles. |
Delete account (for profile comparison) | delete | Self-service users can delete their accounts when comparing their profile with another user. Help desk users can delete accounts when comparing users. |
Manage group memberships (for profile comparison) | managegroups | Self-service users can modify their own group memberships when comparing their profile with another user. Help desk users can modify users’ managed group membership when comparing profiles. |
Check in access | ppmreqrevoke | Help desk users can check in another user’s privileged access. |
Rename account | rename | Self-service users can request to rename their own account ID. Help desk users can request to rename another user’s account ID. |
Rename profile | renameprofile | Self-service users can request to rename their own profile ID. Help desk users can request to rename another user’s profile ID. |
Move user from one context to another | movectx | Self-service users can move their accounts from one target system context to another. Help desk users can move users’ accounts from one target system context to another. |
View profile history | viewhistory | Self-service users can view their own profile history. Help desk users can view other users’ profile history. |
Delegate workflow requests | delegmang | Help desk users can delegate the responsibilities of a user to another user. |
Manage workflow requests | flowmang | Help desk users can act on individual authorization requests of other users. |
View workflow requests | viewworkflow | Help desk users can view individual authorization requests of other users. This rule does not allow users to act on requests of other users. |
Delegate authority | delegate | Self-service users can delegate their own authority to another user. Help desk users can delegate other users’ authority to another user. |
Update security questions | editqa | Self-service users can edit their own security question profiles. Help desk users can edit users’ security question profiles. Question sets must have their help desk permissions configured so that they can be viewed by help desk users. The Update security questions module must be enabled. |
View security questions | viewqa | Help desk users can view users’ security question profiles. Question sets must have their help desk permissions configured so that they can be viewed by help desk users. The Update security questions must be enabled. |
Bypass security questions | bypassqa | Help desk users can bypass security question authentication when helping a user. If a question set requires authentication, help desk users with this right are presented with a Skip authentication button. Help desk users who do not have this right must correctly authenticate the caller before proceeding. This user access rule works in conjunction with ADMIN AUTHUSR MANDATORY. |
View answers to security questions | showans | Self-service users can view answers to security questions, by clicking a Show answers button, when viewing their own security question profile. Normally, answers are obscured. Help desk users can view answers to security questions, by clicking a Show answers button, when viewing a user’s security question profiles. Question sets must be have their help desk permissions configured so that they can be viewed by help desk users. The Update security questions must be enabled. |
Attach other accounts | editids | Self-service users can add or remove existing IDs from their profiles. Help desk users can attach or detach accounts from users’ profiles. |
Request access to network resources | netres | Self-service users can request access to network resources for themselves. Help desk users can request access to network resources for others. |
Browse the OrgChart | vieworg | Self-service users can browse the OrgChart. This option is not available for help desk users. |
View my subordinates | manageorg | Self-service users can use the OrgChart to attach, detach, or transfer their subordinates to another manager. Help desk users can use the OrgChart to attach, detach, or transfer another user’s subordinates to another manager. |
Privileged access | pwdaccess | Self-service users can access the Privileged access to request and check out privileged access. |
Remove recorded session packages | smonremove | Help desk users can remove recorded session packages created by other users. |
Request check-out extensions | extendcheckout | Self-service users can request extensions to checked out privileged access. |
Manage recorded sessions | smonmanage | Self-service users can request the ability to search recorded sessions initiated by a specified user. |
Pre-approved search of my recorded sessions | smonsearch | Self-service users can search recorded sessions of initiated by themselves, without requesting authorization. In addition, users will require the "Manage recorded sessions" privilege to access the Session monitor . |
Pre-approved search of all recorded sessions | smonsearchother | Self-service users can search recorded sessions initiated by any user, without requesting authorization. In addition, users will require the "Manage recorded sessions" privilege to access the Session monitor . |
Pre-approved download of recorded sessions | smonview | Self-service users can download recorded sessions initiated by themselves, without requesting authorization. In addition, users will require the "Manage recorded sessions" privilege to access the Session monitor . |
Pre-approved view of recorded sessions | smonbrowserview | Self-service users can view recorded sessions initiated by themselves, in a browser, without requesting authorization. In addition, users will require the "Manage recorded sessions" privilege to access the Session monitor . |
Password synchronization registration | register | Self-service users can synchronize their passwords. This option is not available for help desk users. |
Generate voice print enrollment PIN | ivrreg | Self-service users can generate their own voice print enrollment PIN. Help desk users can generate a voice print enrollment PIN for other users. |
Manage tokens | token | Self-service users can manage their own security tokens. Help desk users can manage other users’ tokens. |
Requests | trackreq | Self-service users can access the Requests to track and act on requests. |
Groups | viewgroups | Self-service users can access the Groups to view and request changes to group membership. |
Initiate a review of all entitlements | adhoccertify | Users can initiate a review of all entitlements for another user, to confirm or remove access privileges. |
Manage mobile devices | mobile | Self-service users can register and activate their own mobile devices. Help desk users can view and delete mobile devices on behalf of other users. |
Personal vault | personalvault | Self-service users can access a personal vault of account information and passwords. |
Defining membership criteria
A user access rule can have one or more users as members. Membership criteria for a rule is defined by selecting or creating user classes. Users must be participants of the selected user classes in order to have membership in the user access rule.
See User Classes for more details on user classes.
To define membership criteria for a user access rule:
Navigate to the user access rule definition page for the rule you want to define.
Click the Membership criteria tab to select or create user classes that define user access rule membership.
This is not required for profile comparison rules, which are only defined by membership criteria.
Add user classes to the rule. To define rule membership criteria:
Select existing user classes: Click Select and enable the checkboxes for the user classes you want to add, then click Select.
Create new user classes: Click Create a new user class.
Select and create user classes until you have defined group membership.
Configure criteria for multiple classes:
Define whether users are required to match All of the user classes or Any of the user classes .
For a delegated administration rule, map user class participants as either REQUESTER or RECIPIENT . There must be at least one of each.
For profile comparison rules, map user class participants as either REQUESTER , RECIPIENT , or MODELUSER .
For example the user class _MANAGER_DIRECT_ links a manager and a subordinate; you can define the manager as requester and the subordinate as the recipient or model user. Arrange user classes so you have a defined relationship between a requester and a recipient, and between a requester and a model user.
Click Update to save your settings.
Once you have defined membership criteria, click the Test tab to Test membership or List members.
Membership of non-built-in user classes can be cached to improve performance. There are options to recalculate or invalidate the cache on the user class configuration page.
Note
In a replicated environment, cache recalculation can only be performed on the instance which runs psupdate.
Removing users from membership
To remove users from rule membership, you can:
Edit user classes to change the participants.
Delete user classes from the membership criteria.
From the membership criteria page, enable the checkbox next to the user classes you want to delete.
Click Delete.
Example: Define help desk rules
This example shows you how to provide a group of users the appropriate access so they can assist users to change their passwords.
Assumptions
This example assumes that:
Bravura Security Fabric and Connector Pack are installed.
The installation includes a Bravura Pass license.
There is an Active Directory target system set up as a source of profiles.
A user group on Active Directory has been mapped to the _GLOBAL_HELP_DESK_ user class.
A security question set is set up to allow help desk users to authenticate other users before helping them.
Click below to view a demonstration.
Steps
Use the page to define global help desk rules:
The members of the _GLOBAL_HELP_DESK_ user class have now been granted permissions to see a user's security questions.
Testing privileges
The Show effective privileges function allows you to view the privileges for individual users by user access rule categories. To do this:
Click Manage the system > Security> Access to user profiles > Show effective privileges.
Type the profile ID of the Requester. This is the person for whom you want to show effective privileges.
Select which set of Rules to show effective privileges for:
Global help desk rules
Self-service rules
Delegated administration rules – You must enter the <PROFILEID> of the Recipient.
Click Test.
Bravura Security Fabric displays the message “User [ <profileID> ] has the following privileges when acting on <recipient> ”, and lists the privileges for the requester.
If the requester has a privilege in multiple user access rules, then they are all displayed.