Example: Create an OTP API user
This example demonstrates how to create an OTP API user that can be used to retrieve managed account passwords using pamutil .
Requirements
This example requires managed accounts to be onboarded. See Example: Onboard users from an Active Directory target for an example.
Create an OTP API group
Log into Front-end (PSF) as a team trustee for the corporate AD accounts team.
Use the Team: Update PDR.
Select the Corporate AD Accounts Team.
Add a new group called
OTP API Trustee.Provide this group with OTP trustee privileges.
Submit the request.
Use the Team: Management Group Membership PDR.
Add a user to the OTP API Trustee group.
OTP trustees are users who can make OTP API account management requests.
Create an OTP_User
Log into Front-end (PSF) as a user from the OTP API Trustee group created in Create an OTP API group .
Only an otp_api trustee can see the PAMUtil: Create OTP API User PDR.
Click the PAMUtil: Create OTP API User PDR.
Choose the Corporate AD Accounts Team as the System Team.
Click Next .
Add a PAM OTP Account Description
Select the managed accounts onboarded earlier.
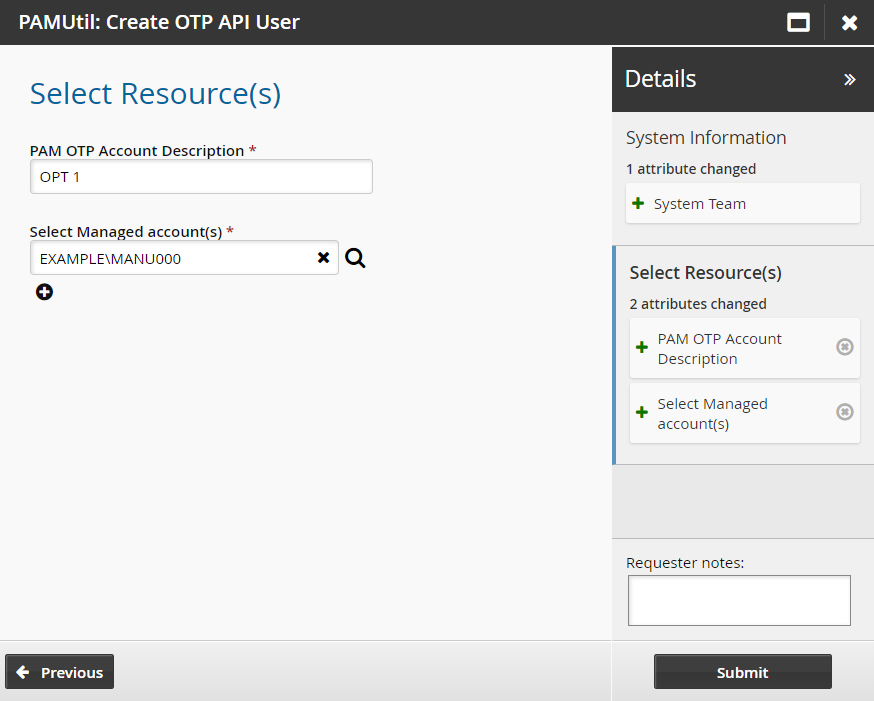
Click Submit.
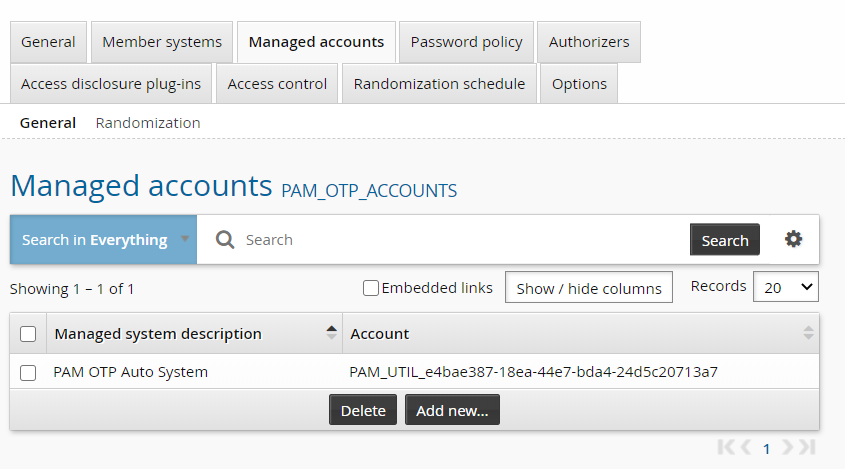
The PAMUtil: Create OTP API User PDR creates a managed account that appears in the PAM_OTP_ACCOUNTS managed system policy in the format of PAM_UTIL_ <guid> , and a product administrator profile to manage the account.
Check out the account
Log into Front-end (PSF) as a user from the OTP API Trustee group created earlier.
Click Privileged access from the Privileged access to managed systems section.
Click Accounts from the Filter panel .
Select the PAM OTP account from the Results panel.
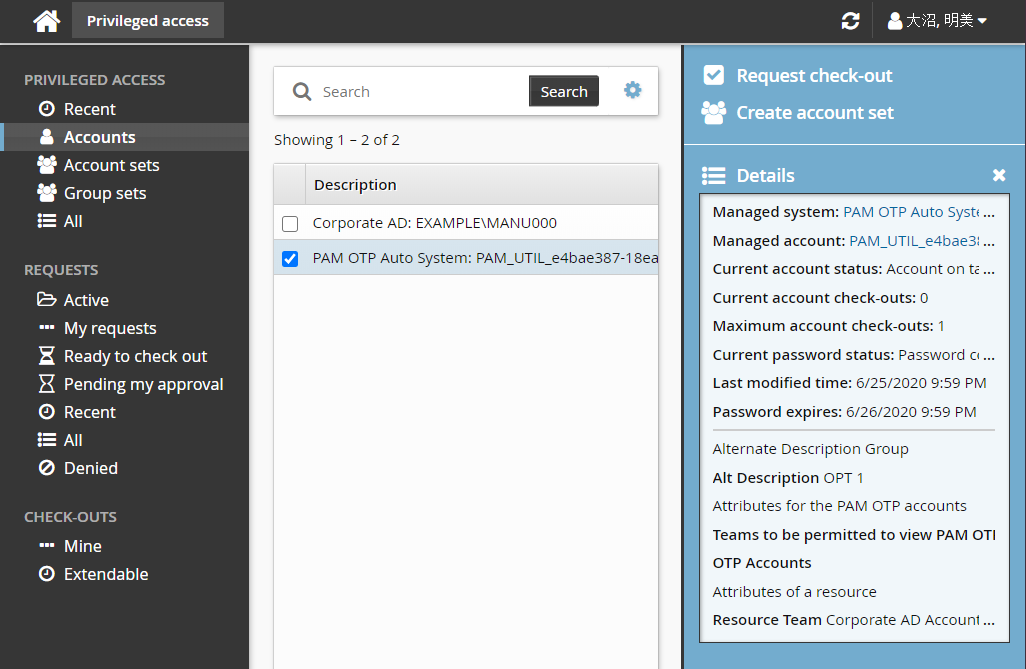
Click Request check-out.
Click Submit.
Authorize the request.
Click Check out from the Actions panel.
The PAM OTP account can now be used by the product administrator profile created earlier, to retrieve credentials of managed accounts it has access to using
pamutil.Warning
Do not check out the vault account again because it will be randomized on check-out and then the one used with
pamutilwill be wrong as it does not get updated with the new, randomized password.