Preparation
Before Bravura Security Fabric can perform operations in Active Directory, you must:
Know the name of the Active Directory top domain where Bravura Security Fabric performs operations.
Optional: Enable SSL connections .
Configure a target system administrator and at least one test account on each Active Directory domain.
Alternatively, you can set up a delegated ID and modify the AdminSDHolder object .
Enabling SSL connections
You can configure the Active Directory connector so that all connections to the ADSI LDAP Provider are made over SSL (using server certificates). Encryption strength depends on the certificate strength.
To do this, you must:
Configure server certificates on all domain controllers (that the Bravura Security Fabric server could communicate with).
Consult your product documentation to ensure Domain controllers have certificates installed. This can vary between Windows 2008R2, 2012, 2016, 2019, and 2022, and deployment method; for example, whether you have manually deployed certificates or auto-enrollment.
For an example of Windows Server 2008 certificate services deployment, see:
http://technet.microsoft.com/en-us/library/cc772393%28WS.10%29.aspx
For an example of Windows Server 2012 certificate services deployment, see:
Install CA certificates on all Bravura Security Fabric servers that validate the Server certificates.
Instructions for installation of the CA certificates can be found here:
http://technet.microsoft.com/en-us/library/cc754841.aspx
All Bravura Security Fabric servers require the trusted CA certificates installed for the local computer store.
Enable the SSL option in the target system address.
Configuring a target system administrator
Bravura Security Fabric uses a designated account (for example, psadmin) on the Active Directory target system to perform operations.
The target system administrator should be a member of the Domain Admins group to list users, and should have the following permissions for password and account operations:
Read All Properties
Write All Properties
Modify Permissions
All Extended Rights
The administrator should also be able to enumerate domain controllers in the domain.
If you are targeting multiple domains in an Active Directory forest with this connector, the target system administrator should be a member of the Enterprise Admins group in the forest root, and the username should be entered into Bravura Security Fabric in UPN format. In this case, while the target system administrator does not need to be a user in the forest root domain, the forest root domain or a domain controller in that domain should be specified in the target address.
Ensure that you set and note the account’s password. You will be required to enter the login ID and password when you add the target system to Bravura Security Fabric .
If you want to configure this account with control limited to the users and services needed by Bravura Security Fabric rather than full administrative control, see Minimizing administrative account rights .
If you want to configure an account with specific delegated control, see Delegating control .
Minimizing administrative account rights
In most cases, you include the target system administrator account (such as psadmin) as part of the Domain Admins group; however, it is possible to set up this account not to have full control over the server and only to have control over the users and services that it needs. This involves removing the target system administrator account from the Domain Admins group and adding it to its own group, then giving that group control over users. Because this involves modifying settings for each user, you might want to set up a script to do this work.
The following instructions are for Windows 2012 Active Directory. Details may vary depending on your version of the software.
To minimize administrative account rights:
Log into an Active Directory Domain Controller as a member of the Domain Admins group.
Launch .
Remove the target system administrator for Bravura Security Fabric (for example, psadmin) from the Domain Admins group, and the Enterprise Admins group as applicable.
Create a group (for example, psadmingrp) and set the scope to
Globaland type toSecurity.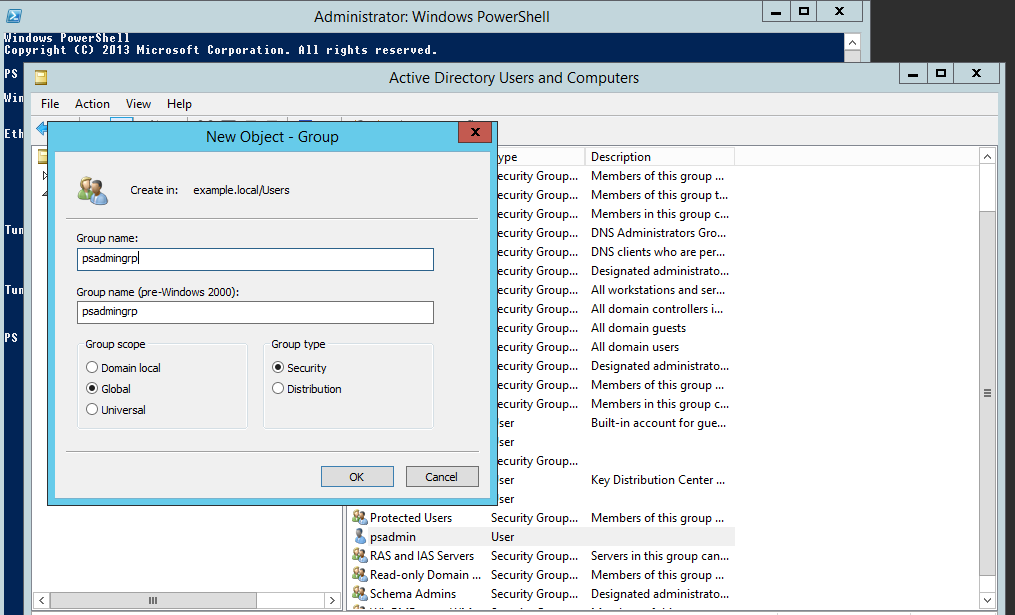
Add the target system administrator to the group you just created.
Set the permissions for the new group that you created:
Ensure that View > Advanced Features is selected.
Right-click on the "user" container that the new group will be used to manage, and select Properties from the pop-up menu.
Click the tab.
Add the group to the list of Group or user names.
Enable the Full Control checkbox in the Allow permissions column.
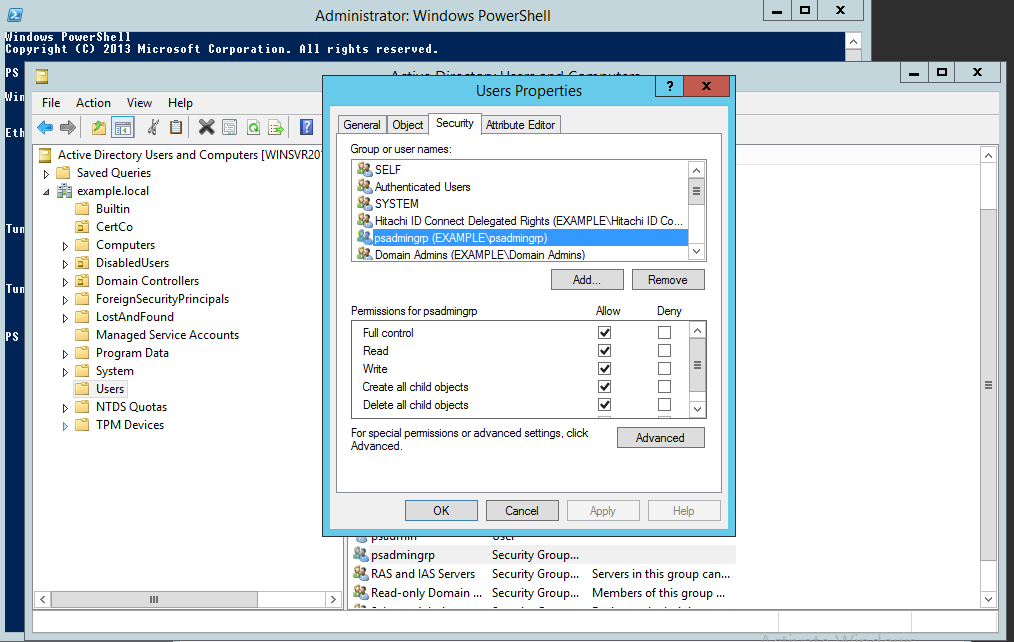
Apply the changes, then click OK to close the dialog box.
If you are targeting multiple domains in an Active Directory forest, you must grant the created group permissions on each domain being targeted. Alternatively, create a new group with permissions in each domain, and add the target system administrator to each group.
The target system administrator must be the same user in all targeted domains, have permission on each targeted domain, and be specified in UPN format in Bravura Security Fabric .
Delegating control
In Active Directory, you can delegate administration of users to a specific individual or group, eliminating the need for the Bravura Security Fabric target system administrator to have authority over an entire domain. We refer to the user as the delegated ID.
If you use a delegated ID, you may also need to configure the AdminSDHolder object .
It is highly recommended that you enable SSL between domain controllers and the Bravura Security Fabric server.
The following steps are used in Windows Server 2012. The steps may vary in other versions.
To create a target system administrator with delegated control, also known as a delegated ID :
Log into a domain controller as an administrator.
Launch .
Create a user in the Users container (or some other container if necessary).
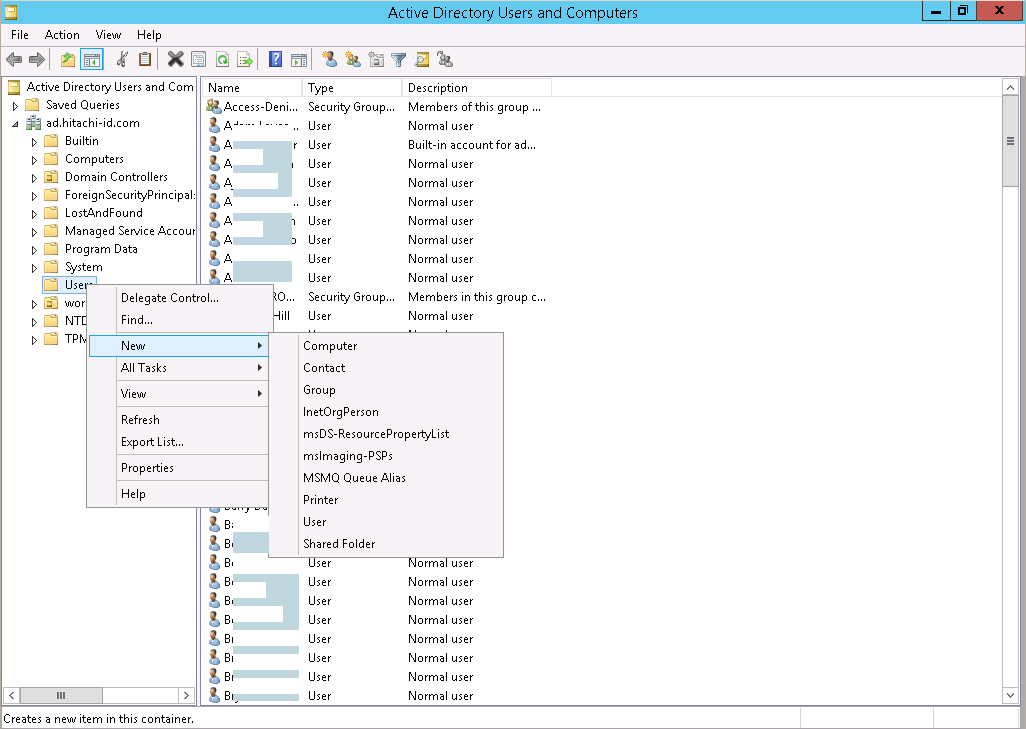
Create a security group to which you can grant delegated control
This allows you to delegate control to members of the group, rather than to an individual user.
Set the scope to
Global, and type toSecurity.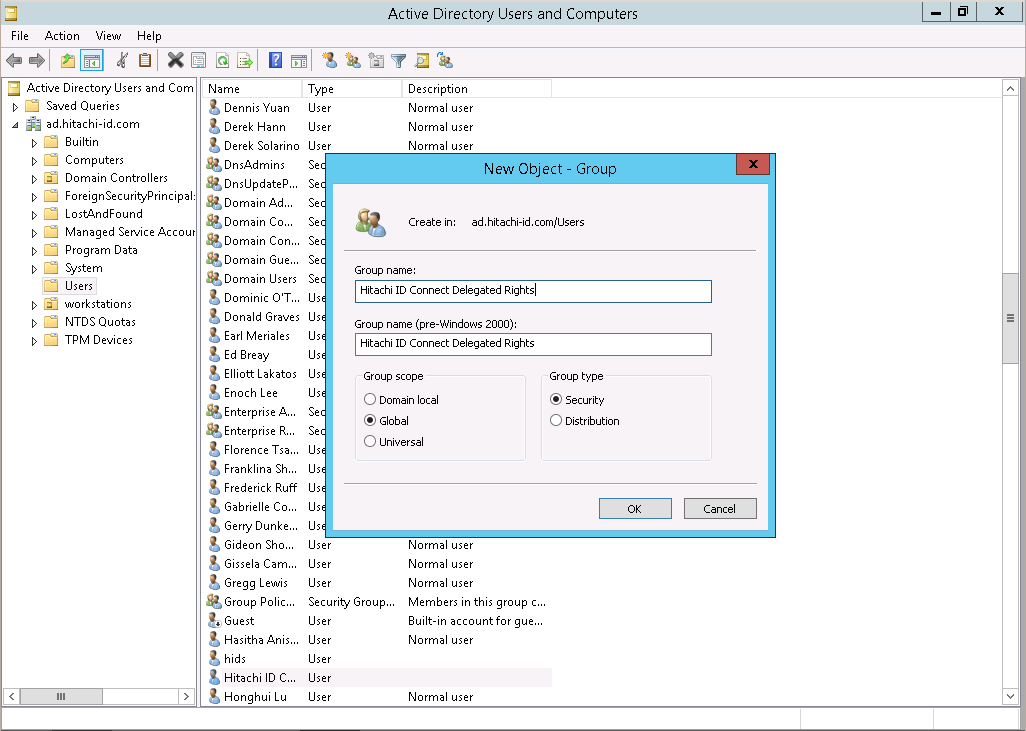
Add the user you created in step 3 as a member of the group.
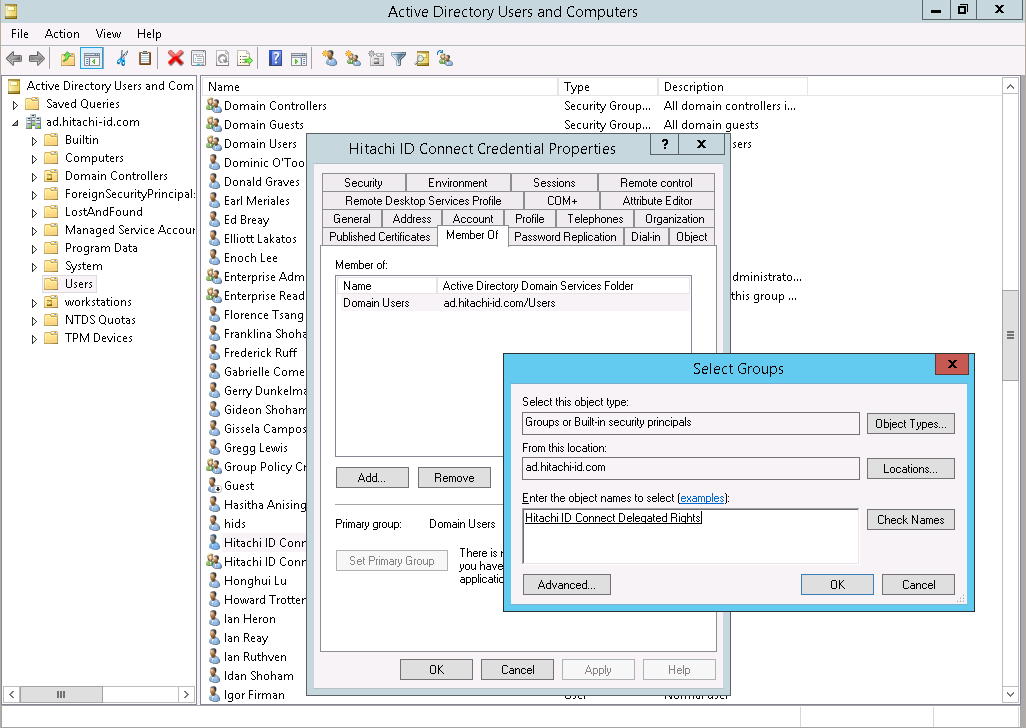
Right click on the container in which you created the user, and select "Delegate Control…".
Click Next .
Click Add… and select the group.
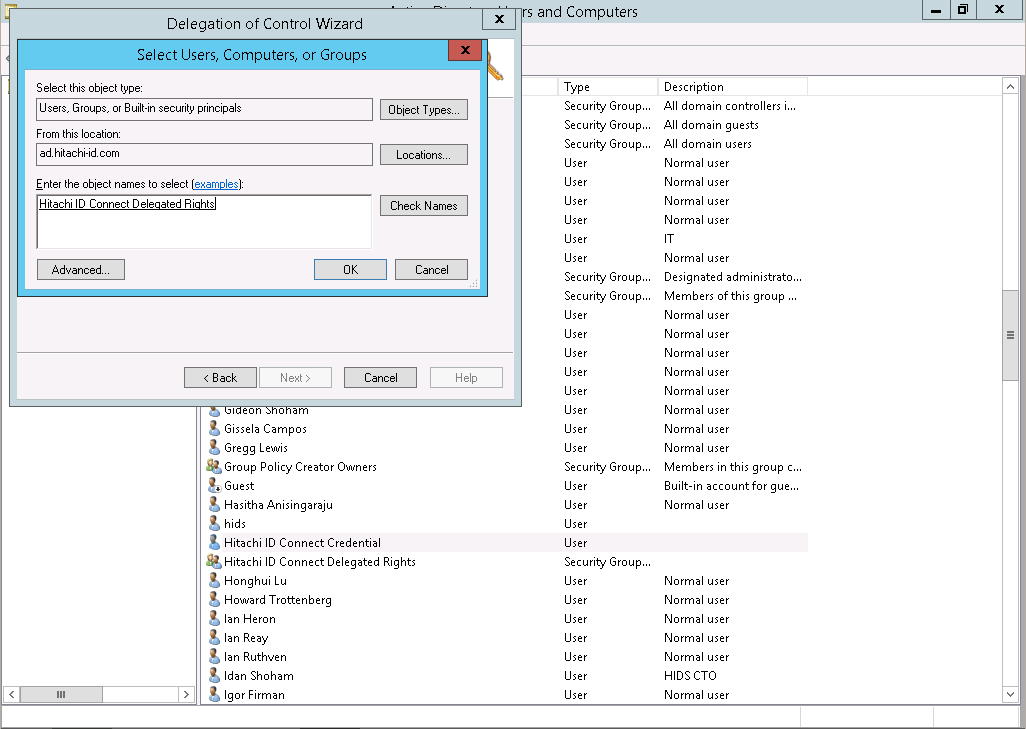
Click OK.
Click Next.
Provide the group with required permissions.
If your license includes Bravura Identity , include "Create, delete, and manage users accounts", "Create, delete and manage groups", and "Modify the membership of groups" in the tasks to delegate. If your license does not include Bravura Identity , you do not need to check those items unless there is a customization; for example, modifying an extra attribute when doing a password reset could require the ability to manage a user account.
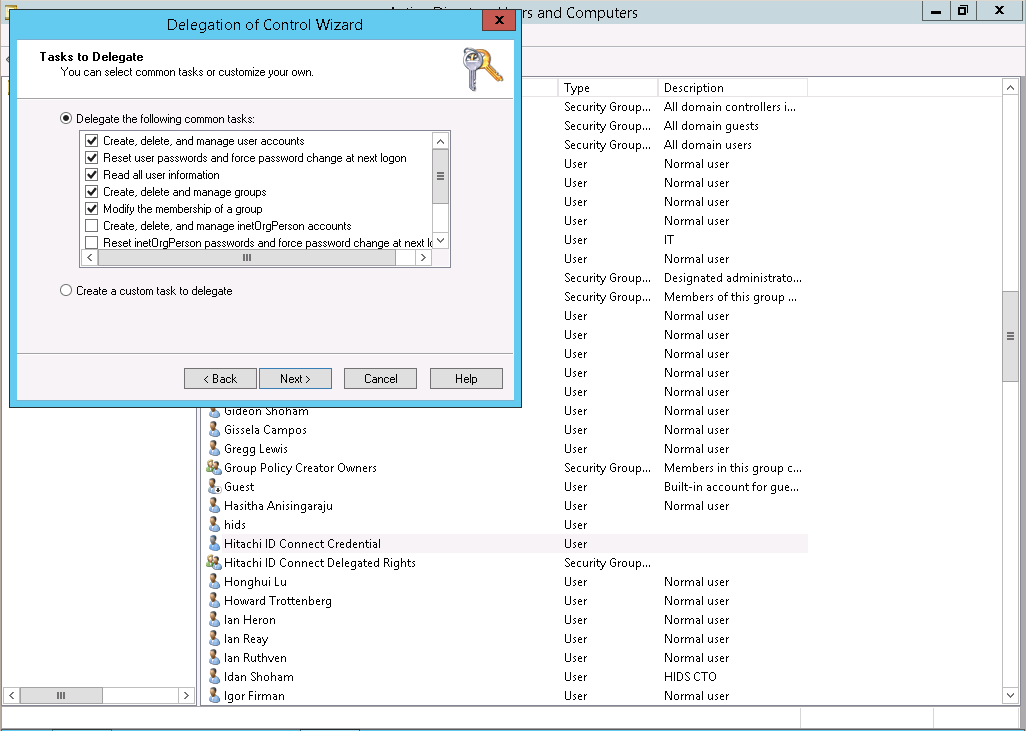
Click Next, then Finish.
For setting more granular permissions, use the ADSI Edit tool. See your Windows documentation for detailed information.
Configuring the AdminSDHolder object
The following applies to Server 2003, Windows Server 2003 R2, Windows Server 2003 with SP1, and Windows Server 2003 with SP2.
The default owner for AdminSDHolder is the Domain Admins group. If your target system administrator is a member of this group, Bravura Security Fabric can reset domain administrator accounts. If you chose to delegate administration of users to a specific individual or group, the AdminSDHolder container will need to be modified.
In order to reset domain administrator accounts using a Delegated ID, configure permissions on the AdminSDHolder object to allow the management account group, created when you created the delegated ID, to reset passwords on AdminSDHolder.
Refer to the following link for detailed instructions:
https://technet.microsoft.com/en-us/library/cc772662%28v=ws.10%29.aspx
Creating a template account
Bravura Security Fabric uses template accounts as models or "blueprints" for creating new accounts in Active Directory. The following example illustrates how you can create a template account in Active Directory:
The following instructions are for Windows 2012 Active Directory. Details may vary depending on your version of the software.
Log into an Active Directory domain controller as a member of the Domain Admins group.
Launch Server Manager.
Select Tools > Active Directory Users and Computers.
Right-click on the Organizational Unit where you want the template account to exist. For example, the Users OU.
Select New >User.
Windows displays the New Object-User dialog box.
Enter the account names and User logon name.
When creating a template account, ensure that the User logon name and User logon name (pre-windows 2000) fields match, or new accounts created using this template may be created with an incorrect value.
If you wish to use different Active Directory and pre-Windows 2000 logon names, you must modify the configured action for the corresponding attributes in Bravura Security Fabric (see Account attributes in the Bravura Security Fabric configuration documentation).
Click Next .
Enter the new user’s password in the Password and Confirm Password fields, and set other options as you require.
You can disable the account if it is to be used only as a template account or enabled later.
Click Next to confirm the user’s account details.
Click Finish to close the dialog box.
Defining properties
By default, Bravura Security Fabric copies many properties (attributes) when creating a new user.
Note
It is recommended that you do not add template accounts to Bravura Security Fabric managed groups. Managed group memberships should be handled by including them in roles.
Without the use of roles, it may be necessary to create multiple template accounts depending on the needs of your organization, because group membership generally denotes resources (such as printers, file shares) to which a user has access.
To define additional properties for the template account:
Open the Users folder and locate the template user.
If you want to set the logon hours and account options:
Select the tab.
Set the following account parameters:
Logon Hours (Optional)
To restrict the hours during which the user can connect to a server. This setting does not affect a user’s ability to use a workstation.
Log On To (Optional)
To restrict the workstations from which a user will be permitted to log on to this domain account.
Account options
To manage the account expiration date and other options.
If you want to configure a logon script or home directory:
Select the tab.
Type the full path for the user’s profile in the Profile path field and the logon script to be used by the account in the Logon script field.
Type the location of the user’s Home folder in the Connect: To: fields.
When creating the template account’s home folder, ensure that the folder name matches the template account ID (required so that Bravura Security Fabric can replace the ID with the ID of the new user). No home directory is created for the recipient account if the template account has their Home folder defined on the DC (the Local Path), the home folder must be located on a network drive (Connect drive: to).
Configure other properties as you require.
Click OK to close the window.
Close the window.
Renaming template accounts
If a template account is renamed on the target system, account creation behaves differently depending on whether the target system is a source of profiles:
If the target is a source of profiles, then nothing changes. Bravura Security Fabric can continue to use the template account as is to create accounts.
If the target system is not a source of profiles, when you rename the template account (for example, cn or distinguishedName) ensure that userPrincipalName is also renamed or emptied out. If userPrincipalName is not renamed nor emptied, account creation will fail.