Teams
Team management in Bravura Privilege Pattern delegates onboarding of systems and accounts and definition of access control rules to business stakeholders.
Team management is constructed around a number of concepts:
A team may represent a group of people, an application or an organizational unit.
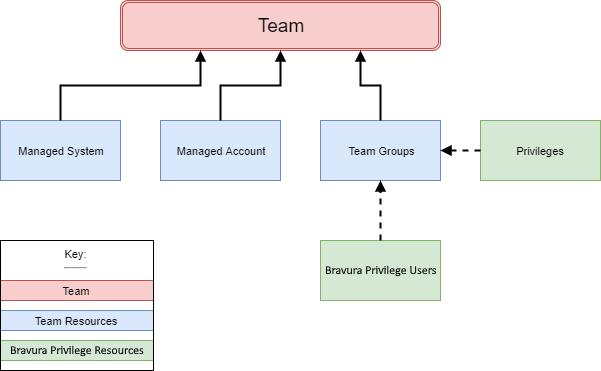
Teams contain:
Managed systems with which Bravura Privilege is integrated.
Managed accounts that appear on managed systems and whose passwords Bravura Privilege may set.
Team groups used to assign privileges to Bravura Privilege users.
Team groups contain:
Privileges such as trustee, approver, requester. See Privileges and appropriate users for more.
Individual Bravura Privilege users
Managed groups of accounts defined on a target system, such as AD or LDAP, whose membership is monitored and managed in Bravura Security Fabric . On some target systems, this can include groups inside groups.
Team vaults Used to store and retrieve credentials for target systems that do not communicate with Bravura Security Fabric or other secrets (e.g., a safe's combination). They are not intended to set or randomize credentials stored within them. Team vaults contain:
System vaults Representations of systems in the environment, but without a connector or technical integration.
Vault accounts Representations of accounts on system vaults, along with stored (but not actively managed) passwords.
Proxy zone A set of Bravura Security Fabric proxy servers responsible for running connectors that communicate with a set of systems, typically in the same location or on the same network segment. This is typically required when direct connection is blocked by a firewall. Bravura Privilege may also connect to managed systems discretely; that is, a connector runs locally on the Bravura Privilege application server and uses an appropriate API and network protocol to sign into the system in question.
Team administrators
Team administrators are users that are responsible for creating, deleting and managing group memberships of teams. When creating a team, a team administrator assigns trustees to the teams. Team administrators and team trustees can both manage team group memberships; but, once a trustee is assigned, a team administrator will require permission from the team trustee to make changes. It is best practice not to allow team administrators to also be team trustees.
The team administrator role is generally given to a user within the company that is aware of how the business is structured. The user may be a technical person that also functions as a product administrator for Bravura Privilege or they may be more involved in the business operations of the company.
Users must be a member of the PAM_TEAM_ADMINS user class to be team administrator and create and delete teams.
Team trustees
This topic is used in the privilege pattern book and is different to the training topic on purpose. This topic is just about Team trustees, whereas the training one has expanded and talks about other trustees. We discuss these other ones in the privileges and appropriate users instead. tp
Team trustees use Bravura Privilege to manage their assigned teams by controlling team group membership and privileges. They are also responsible for onboarding and offboarding systems and accounts to their teams.
Users who are assigned as team trustees are automatically added to the PAM_PRIV_TEAM user class to gain access to the appropriate PDRs.
Caution
Do not add groups to the PAM_PRIV_TEAM user class.
Privileges and appropriate users
Within the team structure, team groups are created to assign privileges to. Team group members can be assigned the following privileges:
Account trustee A user who can onboard, offboard, and update privileged accounts.
Approver A user who can allow or disallow access requests.
Approvers are also referred to as authorizers in the core Bravura Security Fabric configuration and documentation.
Approvers are often the owners of the managed account or an appropriate manager of the requester.
Auto_Approved A user who can check-out access to systems and accounts without making an access request. These users must also have permission to request access.
Users that check out an account on a regular basis should be given the auto-approval privilege to avoid holding up their work and to avoid approver fatigue.
Credential Manager A user who can override or randomize the stored password on a checked-out account. These users must also have the requesters privilege.
Credential manager privilege is often given to the owners of the managed account.
LC trustees a user who can create and update vaulted credentials.
OTP Trustees a user who can create and use OTP accounts.
Requester A user who can make access requests.
Requesters that require approvers are generally users that do not require access to the managed account on a regular basis, but should still have access to the account in the event of an emergency or a circumstance that arises on occasion.
Subscriber trustee a user who can make subscriber validation requests.
System trustee a user who can onboard, offboard, and update privileged systems.
Team trustee a user who can make team management requests.
Vault trustee a user who can create, archive, and update vault systems and accounts.