Product considerations
Carefully analyze configuration parameters and files to determine what will be affected. Consider the following:
Build number for patch
If you are applying a patch:
Make note of the patch build number. Request the build number from support@bravurasecurity.com if you do not know it.
If your organization has more than one ticket pending the application of a patch (including tickets from other administrators within your organization), always use the latest patch. Clarify with support@bravurasecurity.com if you are not sure which patch to use.
If your organization has open tickets where the Bravura Security developers are still preparing patches, it may be preferable to wait for all pending changes to be prepared. A patch containing all previous fixes and enhancements can be applied and tested simultaneously. This will reduce overhead and the required maintenance windows and change controls.
Alternatively, if you have multiple outstanding patches to apply and decide to patch each issue individually, verify the correct patching order with support@bravurasecurity.com in order to reduce any potential interference with other open tickets.
Databases
Each significant version of Bravura Security software is likely to have different requirements for its database tables, table schema or data encoding.
Below is a compatibility matrix that should be taken into consideration when upgrading Bravura Security Fabric and Connector Pack in regards to MSSQL database requirements:
Latest version requirements
Check available database space
If an upgrade or patch changes the instance’s database schema, verify there are at least two and half times the total database size free on each database server where the temp is.db files are stored.
Using MSSQL Management Studio check the size of the database files.
In Windows Explorer, look at the free space available where the temp.db files are located.
If the free space is less than two and a half times the size of the database, allocate more disk space.
Failure to do so may result in the installer failing to update the database schema.
Analytics
If you are installing the Analytics app feature as part of an upgrade you must install Microsoft’s SQL Reporting Services.
After installing Microsoft’s SQL Reporting Services gather the following information:
The server name where SQL Server Reporting Services (SSRS) resides
Report Server Web Service URL
Name and password of service account
If you are using an existing report server database you will need that database name
If you are using an existing report server user you will need that username and password
See Analytics for more information on this feature.
Replication configuration
Establish a window to perform the upgrade when all replication nodes can be offline. It is highly recommended that replication queues be flushed to avoid data loss. Generally, in a replicated environment, plan for the following:
Before performing an upgrade, services, except the logging service (and, in some cases, the database service), should be stopped on all replication nodes, and the replication queues should be allowed to empty.
Upgrade each node, starting with the primary node.
Ensure that services remain stopped until all nodes have been upgraded. This prevents data and files from becoming unsynchronized.
This process will vary based on the version you are upgrading from and to. This is detailed in the upgrade instructions and playbooks.
Scripts, plugins, and configuration files
When configuring Bravura Security software, various files may have been added or modified to implement various features or customizations.
Carefully analyze and test all scripts, plugins, and configuration files; for example:
Customized auto discovery scripts
Target integration configuration files
External interface program configuration files
Plugin scripts
Language and user interface modifications
Customized password strength dictionary file
Filters
Access controls, including user classes
Service configuration
Note the following for custom scripts, plugins, and configuration files:
The directory structure may have changed between versions; verify any hard-coded directory PATH details.
The names of Bravura Security Fabric programs may have changed; verify all references to those programs.
The command line usage of Bravura Security Fabric programs may have changed; verify all arguments being passed into those programs.
Scripts written in the PSLang language are being migrated to Python scripts. You may want to examine any scripts to determine if new build-in functions or versions written in Python are available to optimize your code.
The capability of connectors and external interface programs may have been enhanced (possibly by changes to the target address line or additional options in its configuration file); you may need to review your integrations to reflect those changes.
New built-in connectors may have been written for integrations you previously scripted using flexible connectors; you may want to re-implement those targets using the new connector.
Multiple connectors may have been consolidated into a single connector (for example, the Domino and Lotus Notes connectors were combined in connector pack 1.3); you will need to redo any integrations using either of those connectors.
If you have your own compiled binaries for custom interfaces, plugins or authentication chains, you must recompile them as 64-bit.
The SearchFilter plugin interface was completely overhauled in 12.3.0. Components using add_expression or manually altering query will need to be rewritten using the new builder interface.
This overhaul may cause problems with older implementations of this plugin during upgrades See the Knowledge Base article https://support.hitachi-id.net/hc/en-us/articles/4414643138583 for more information. You will need Bravura Security portal access to view this article.
Changes to wfreq plugins as of 12.0.0 mean almost any custom wfreq extensions likely need to be re-written or have logic changed to meet new restrictions on when the plugin runs.
Custom loaddb or
idtrackscripts written prior to 12.0.0 should be tested. Care has been taken to maintain backwards compatibility but some edge cases may not work or require refactoring; for example, differential listing works differently to older versions.Changes to the EMAILPIN component as of 12.0.0 means existing entries in the PSLSTORE table pertaining to the EMAILPIN are no longer valid in v12+. All PSLSTORE entries with the namespace EMAILPIN must be cleared prior to the upgrade to ensure the EMAILPIN component remains functional after the upgrade.
File Locations
When you install any Bravura Security product, the default path for program files is <Program files path>\Bravura Security\ as of 12.5.0.
Prior to 12.5.0, the path is <Program files path>\Hitachi ID\.
The directory name is not changed when upgrading.
Three main directories are created when you install Bravura Security Fabric instance, as detailed below.
It is recommended that you do not change these directory locations during the setup process. You cannot install any of the directories required for Bravura Security Fabric on a mapped drive.
<Program Files path>\Bravura Security\Bravura Security Fabric\<instance>\
Directories marked with  include files installed by Connector Pack .
include files installed by Connector Pack .
Directories marked with  include folders and files installed with the optional Analytics app.
include folders and files installed with the optional Analytics app.
Directories marked with 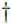 include optional files. They are only installed in a complete installation or if selected in a custom installation.
include optional files. They are only installed in a complete installation or if selected in a custom installation.
Directory | Contains |
|---|---|
| Files required for add-on software, such as Local Reset Extension and SKA. Some files, required to target Netegrity SiteMinder, are installed by Connector Pack . If you installed a global Connector Pack , these files are contained in the Connector Pack global directory. |
| Instance-specific user management connectors (agents). If you installed a global Connector Pack , user management connectors are contained in the Connector Pack global directory. |
| Analytics app specific folders |
| Contains * .rsd files which are Shared Dataset Definitions. These files are only used by SQL Server versions higher than Express. They contain datasets that are shared between reports. |
| Contains * .rdl files which are Report Definitions. These files are the drillthrough reports used by other reports. They are not visible to the end-user. |
| This folder contains other folders. Each folder in this folder is a category in the Analytics app. Within these folders are * .rdl files which are Report Definitions. The folders need to be added to the CUSTOM ANALYTICCATEGORIES system variable to be visible. These reports are then visible to the end-users in the Analytics app. |
cgi-bin | The user web interface modules (* .exe CGI programs). |
db | The Bravura Security Fabric database sqlscripts. |
db \ cache | Search engine temporary search results. These files are cleaned up nightly by |
db \ replication | Stored procedure replication queues, and temporary replicated batch data. |
| Files necessary to make modifications to the GUI. Some files are installed by Connector Pack . If you install a global Connector Pack , files related to connectors are located in the global design directory. |
dictionary | A flat file, Bravura Security Fabric uses this file to determine if new passwords fail dictionary-based password-policy rules. |
idapiservice | Files required to use the SOAP API. |
| Instance-specific ticket management connectors (exit trap programs). If you installed a global Connector Pack , ticket management connectors are contained in the Connector Pack global directory. |
lib | Contains the |
license | The license file for Bravura Security Fabric . |
plugin | Plugin programs executed by Bravura Security Fabric . |
psconfig | List files produced by auto discovery and the |
report | Files and programs for report generation. |
| Instance-specific sample scripts and configuration files. If you installed a global Connector Pack , connector-related sample files are contained in the Connector Pack global directory. |
script | Configuration files and scripts used by connectors, |
service | Service programs. |
sessdata | Session data. A scheduled program removed old data files nightly. |
skin | Compiled GUI files used at run-time (HTML and *.z). |
smon | Monitored session data. This location can be changed by Recorded session management (smon) module options. |
| Command-line programs and utilities. If you install a global Connector Pack , tools related to connector configuration are located in the global util directory. |
| The If you installed a global Connector Pack , this directory is created in the Connector Pack global directory. |
wwwdocs | Images and static HTML pages used by Bravura Security Fabric . |
<Program Files path>\Bravura Security\Bravura Security Fabric\Logs\<instance>\
Any operation that is run by Bravura Security Fabric is logged. Those logs are invaluable when debugging an issue. The log directory by default is <Program Files path>\Bravura Security\Bravura Security Fabric\Logs\<instance>\ . Each instance of Bravura Security Fabric that is installed will have at least one sub-directory within this directory.
The rotatelog scheduled job, which runs on a nightly basis, rotates the logs into a new folder, to reduce disk space usage.
<Program Files path>\Bravura Security\Bravura Security Fabric\Locks
Certain target systems can only be accessed serially, such as Lotus Notes. This is a limitation of the API used to access the target system. In these cases Bravura Security Fabric drops a lock file in the locks directory when an operation is being performed that should only be performed serially. For this reason the locks directory must be the same for all instances of Bravura Security Fabric that are installed on the same server.
When you install Connector Pack , files are placed in different locations depending on type of Connector Pack .
For an instance-specific connector pack, the installer, connector-pack-x64.msi, installs connectors and supporting files in:
<Program Files path>\Bravura Security\Bravura Security Fabric\<instance>\
For a global connector pack, the installer, connector-pack-x64.msi, installs connectors and supporting files in:
<Program Files path>\Bravura Security\Connector Packs\global\
The table below describes the function of directories that are created when a Connector Pack is installed:
Directory | Contains |
|---|---|
addon | Files required to target Netegrity SiteMinder systems |
agent | User management connectors (agents) |
design | Connector Pack -related files necessary to make modifications to the GUI; for example target system address help pages. See the “Customization Guide” for details. |
interface | Ticket management connectors (exit trap programs) |
samples | Sample scripts and configuration files |
unix | The |
util | Tools to support the configuration of various target systems |
Services
After an upgrade, service configuration is reset to the default. If you have set the startup type of a service (for example, if you have set a service to delayed start), this change must be made again after upgrading.
Reports
Saved reports will not be preserved when upgrading from earlier versions. After the upgrade, scheduled reports can be viewed on the Manage the system > Maintenance > Scheduled jobs page, but cannot be run or modified.
Reports in Bravura Security Fabric versions 9.0 or later are SQLite databases.
After upgrades or patches you can expect to see errors from loadreports on reports not covered in your product license.
Product customizations and fixes
In addition to configuration files, your Bravura Security Fabric instance may contain custom binaries and/or schema. These could include web modules, connectors, plugin programs, external interface programs, and so on.
Once custom binaries are identified, their purpose should be determined to decide whether they are still necessary. For example, if the custom binary was created to resolve a product deficit, the deficit was likely resolved in the base product. Similarly, if the purpose of the binary was to add custom functionality, it is also possible that the feature was added to the base product.
Read the Release notes to determine whether a custom binary is necessary. If it is still not obvious, contact support@bravurasecurity.com for assistance.
Only in very specific cases will an older binary be usable in a newer product. A previous service engagement or product fixes on an existing instance (including binary and/or schema) might require assistance from Support to either initiate a new service engagement, verify the fixes provided in a previous release, or indicate a new feature or functionality that supersedes fixes in older functionality.
Determine the level of product customization
Bravura Security Fabric is a comprehensive suite of products comprising many binaries and scripts, which are designed to work together as a unified identity, privilege, and password management platform.
When troubleshooting or preparing for an upgrade or migration, you must identify if and where the Bravura Security Fabric instance is using stock code versus something customized.
The default installer available from Bravura Security is the stock release build and does not contain any customer-specific customizations unless those features have been incorporated into the base product. If there are customized features or fixes in your current version that should be preserved in the new destination product version, let your Account Manager or Support know, so Bravura Security developers can look for differences and carry them forward if feasible, creating a custom build of the new version.
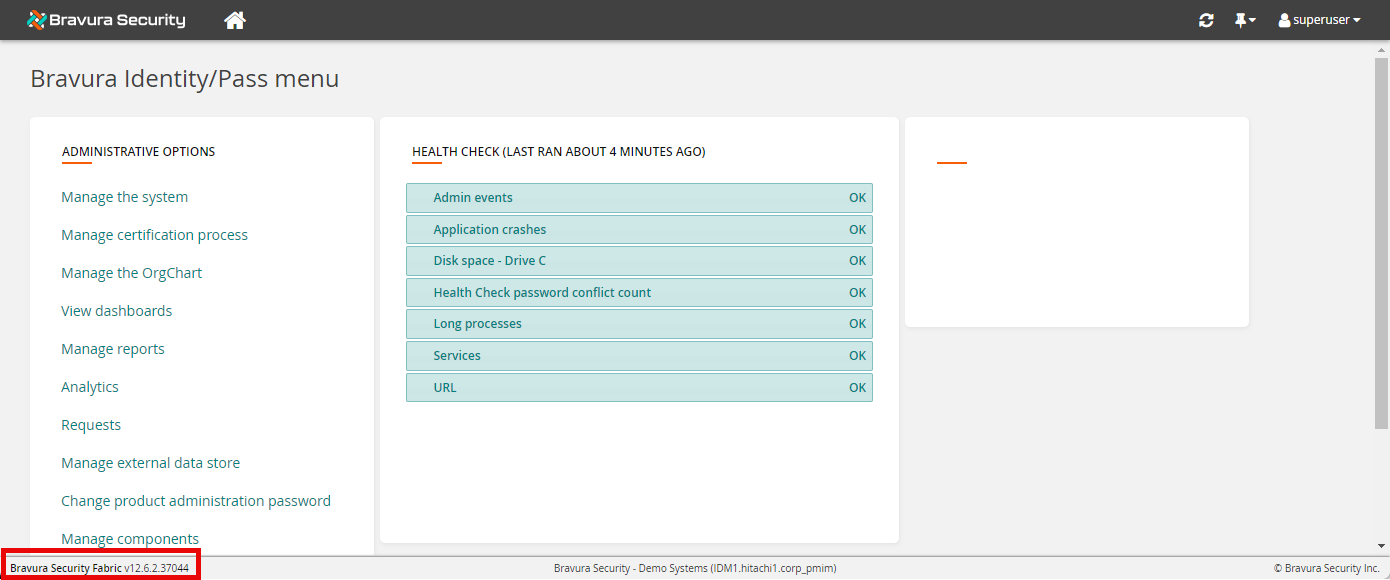
There are several ways to check for specific versioning changes in your current instance:
Look for the version displayed in the default product Web UI footer, as shown above. This is the version of the CGI binary that renders that specific page.
Check binary versions and their builds in Windows Explorer by right-clicking the file > Properties > Details. Alternatively, you can check version information using the getfileinfo program .
Write a complete list of versions for each binary in the product in a text file by running the following in a command prompt from the instance's util directory:
instdump.exe -binaryversion -outfile binversions.txt
See instdump for more usage information.
For even more details such as file description, including who each binary was built for, and information on other files like config and non-binaries, and the CommonFiles required by some of these binaries, use PowerShell from the instance directory. For example:
dir cgi-bin\, agent\, agent\cmn\, interface\, plugin\, service\, util\, design\, report\, wwwdocs\, C:\Program Files\Common Files\Bravura Security\ | Get-ItemProperty | Format-list -Property * -Force > binversions-verbose.txt
(For versions 12.4 or older replace "Bravura Security" with "Hitachi ID". )
If the agent directory is in the Global Connector Pack location, replace that location in the cmdlet above.
Add other locations, or use a subset of the command for a specific troubleshooting task.
Check if SQL stored procedures in the backend database are customized by comparing them with the default code listed in the instance's db\functions-mssql.sq l.
Similarly, the default backend SQL database schema is provided in db\dbdefault-mssql.sql
Look for custom product UI skins in design\custom .
When upgrading to a newer version these may not be used as-is, because the UI changes between versions. However, they are useful to determine what has to be changed.
Look for custom components in component\Custom (ignore the samples).
Configuration for installed components and other parts of the product are in db/extdb.db .
Identify custom plugin scripts by modification date in the instance's plugin directory
Look for other custom scripts, such as
pxnull-itsm.cfgwhich contains exit trap email notifications, in the instance's script\directory. The date/timestamp is also useful here for identifying modified scripts.See details of the license currently active on a product application node by running the following in a command prompt from the instance's util directory:
licviewer ..\license\idmsuite.lic
See licviewer for more usage information
The license file format was modified in Hitachi ID Suite 10.1.0, so a
licviewerprogram from either side of that version is not compatible with the file from the other side.
Client tools
A new version of Bravura Security Fabric may need a newer version of the target system client software installed on the primary node.
As of 9.0, Bravura Security Fabric is completely 64-bit, so it requires any target tools (for example, database clients, SDKs or any software our product loads directly to integrate with targets), to also be installed as 64-bit versions. This means that for fresh installs (including replication migrations), the 64-bit clients must be installed, and for cloned migration, the 32-bit clients must be uninstalled and the 64-bit client installed.
Refer to Connector Pack documentation for details on any targets that require target clients or tools.
Web interface modifications
All custom web interface modifications should be reviewed. Some existing modifications will require modification or deletion, while new modifications may need to be added.
The best method to address this issue is to go through every file in the custom directory in the source instance and confirm the same file exists in the destination instance src directory. If a file does not exist in the new instance, the custom version of the file can probably be deleted. If a file does exist, go through the entire file and search for each tag or KVGroup in the new instance. If the tag or KVGroup does not exist, it can probably be deleted from the file. If it does exist, compare the custom version to the default version in the new instance and figure out what if any modification will need to be made to the custom version.
Finally, test all the web pages and verify that the desired modifications have been migrated properly. Also look for new web interface constructs that may require new modifications.
See Customization for more information.
Language packs
Check the Bravura Security portal or contact support@bravurasecurity.com to find out what language packs are available for the new version. The lack of a language pack might cause delays in the migration project if it does not yet exist.
Supporting systems
As mentioned in Inventory of systems , there are a number of potentially related supporting systems to consider in addition to the Bravura Security Fabric servers themselves. These systems fall into two categories; systems with Bravura Security Fabric software components installed on them, and other technologies that support the Bravura Security Fabric server.
Caution
When upgrading, ensure that the server requirements for the new product version are met on the server. See the latest Server requirements. Attempts to upgrade or patch on under-provisioned servers are likely to fail.
Mainframe support
Bravura Security's Mainframe Connector does not directly integrate with the operating system, it integrates with one of the three operating system security modules described in Mainframe in the Connector Pack documentation.
As long that those modules' plugin infrastructure does not change, the integration is supported.
Bravura Security recommends testing the integration several months before the production upgrade, so there can be time for us to address any issues introduced by the new version.
The current Mainframe Connector can communicate with connector packs 2.3.0 or newer.
Python
Verify the minimum Python requirements for the upgrade.
Bravura Security Fabric versions 12.0.0 to 12.3x require Python 3.7.3+ 64-bit.
Bravura Security Fabric versions 12.4+ and 12.5+ require Python 3.10.5+ 64-bit.
Bravura Security Fabric versions 12.6 requires Python 3.11.2+ 64-bit.
Python must be installed for all users.
The upgrade in support may cause issues with some scripts.
See also
Bravura One applications
Bravura One app must be the same version as the instance so ensure this is included in your upgrade plan. For more information about the Bravura One app see Mobile Access in the Bravura Security Fabric documentation.
Upgrading from version 10.1.4 or below will require that the Bravura One app be registered again from the mobile devices if two-factor authentication has been enabled to scan a QR Code for mobile authentication for phone-assisted login.
Proxy Servers
Bravura Security Proxy servers can be upgraded in any order after the application nodes are upgraded, as long as it is done before file changes are propagated post upgrade .
Release notes
Review the latest Release notes to identify changes that might affect expected product behavior.
Pay particular attention to:
Script changes for plugins and exit traps.
Access controls.
Features that have been added or revoked.
Operating system updates
Verify there are no pending Windows updates to be installed, and verify that no server restarts are scheduled before starting the upgrade or patching process.
Product password
Ensure that you know the Bravura Security Fabric service user (psadmin) password. This will be required to upgrade existing systems.
Learn more about Changes to the service account (psadmin) with serviceacct.
Bravura Privilege
Review the following:
Managed system policies. Ensure that no single account belongs to more than one policy.
Warning
As of version 12.0.0, Bravura Privilege does not allow for a managed account to belong to more than one policy. If an account is a member of multiple policies at the time of the upgrade, it will be removed from all policies, except from the managed system’s primary policy.
Session monitoring privileges for both managed system policies and self-service rules.
Warning
Session monitoring privileges have changed as of 12.0.0. All managed system policy and self-service rules will be cleared upon upgrade. You will need to reconfigure them after the upgrade.
Bravura Privilege Pattern trustee privileges. Trustee privileges changed in 12.0.0. The upgrade script should maintain any existing rules so they work how they used to, but authmod rules should be reviewed in case different behavior is desired.