Preparation
Before targeting Google Apps:
Enable api access in Google Apps.
Configure the Google API credentials
These steps are detailed in the sections that follow.
Enabling API access in Google Apps
The Google Admin SDK API lets you perform administrative operations on users, groups and organization units in your account. api access needs to be enabled before it can be used.
To enable API access in Google, log into the Google Cloud Console and enable the Admin SDK API. It can be searched by clicking on Library on the left side menu then in the APIs & Services section.
For more information on where to find this setting refer to the Help available in the Google Cloud Console.
Configuring the Google API credentials
The agtgapps connector uses a service account to call the Google api service, so that Bravura Security Fabric users are not directly involved. Those credentials need to be set up in the Google Cloud Console.
In order to connect through the API, an encryption file must be generated and saved on the instance server. This encryption file is unique for each Google Apps service account.
To configure the Google API credentials:
From the Google Cloud Console, create a new service account or choose an existing one.
Do not use one of the Google default service accounts.
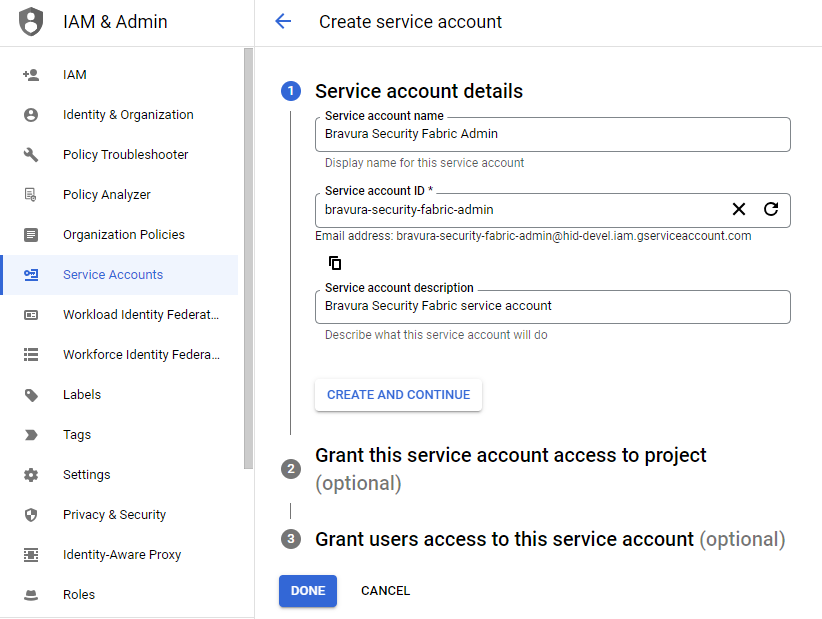
Assign the service account the "Editor" role.
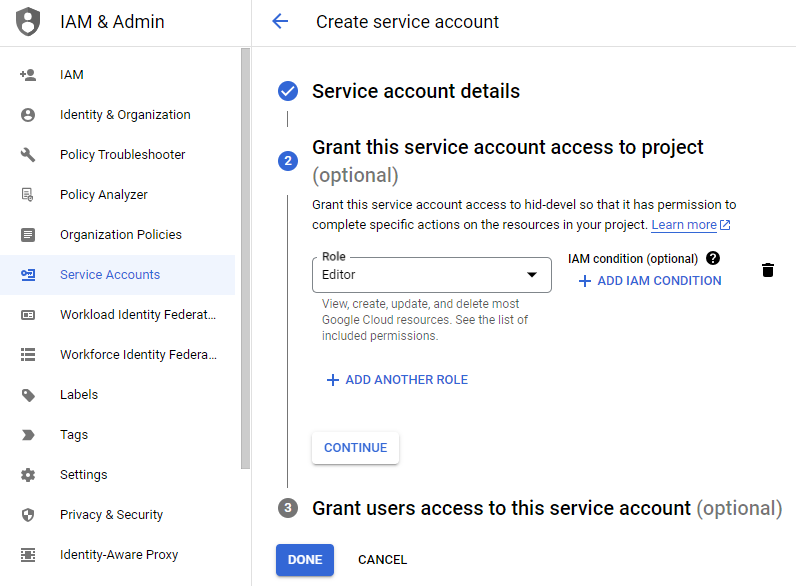
Take note of both the Email and Unique ID (Client ID) values for the service account that were generated. These will be used later.
Once the service account is created, from the KEYS tab, choose to create either a JSON formatted file (which is recommended) or a .P12 type of "private key" for the service account you are going to use.
Save the generated file on the instance server. This will be used later.
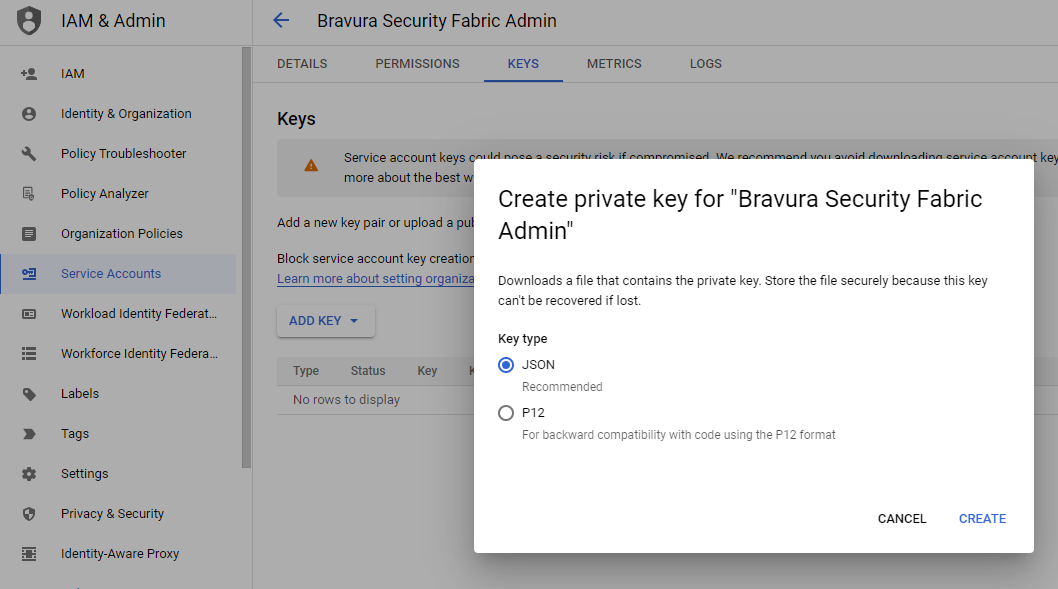
Note
Take note of the private key’s password if .P12 type of key is selected.
For information on how to create a Google service account, enabling Google Apps Domain-wide Delegation, assigning roles, or to generate a service account key, refer to the Help available in the Google Cloud Console and Google Admin Console.
Note
You can view the Email and the Unique ID (Client ID) for the service account client and the service account ID in the Google Cloud Console later if required.
Your Google administrator may be able to provide the service account key file, and the .P12 private key’s password.
Once you have the encryption file, set the permissions to allow the instance to use the API:
Log into the Google Admin console.
Browse to Security > Access and data control > API controls, then click Manage Domain-wide Delegation.
Add a new API client for the service account and enter:
In the Client ID field, enter the value of the Unique ID for the Service account generated earlier.
In the OAuth scope field, enter
https://www.googleapis.com/auth/admin.directory.user,https://www.googleapis.com/auth/admin.directory.group,https://www.googleapis.com/auth/admin.directory.rolemanagement, https://www.googleapis.com/auth/admin.directory.usersecurity
Click Authorize.
Google Apps is now ready to be added as a target system to the Bravura Security Fabric instance.