Technical requirements
To deploy Login Assistant in the scenario described above, the following high-level requirements are needed:
Set up VPN infrastructure to support the refreshing of locally cached network credentials on Windows workstations.
Allocate/provision appropriate domain controllers and a dedicated "site" within Active Directory.
Install the Bravura Pass Local Reset Extension either on remote user workstations/laptops, or set it up for remote execution from the Bravura Pass server.
Install the Login Assistant with Credential Provider software on remote user laptops and workstations, and configure it to use the locally installed VPN command-line client with specified credentials.
http://support.microsoft.com/kb/2514642
On newer Windows systems, the installer can assign the "SeBackupPrivilege" when it is run with elevated privileges.
Network architecture diagram
VPN requirements
A VPN connection is required during the credential refresh phase, where the Local Reset Extension updates the local Windows credential cache with the end user’s new AD password. If no VPN is available, then attempts to refresh the cached AD credentials will fail, and the user will still be locked out of their laptop.
When setting up the VPN infrastructure:
A command-line capable VPN client must be installed on each end-user workstation or laptop that will be used for remote connections.
To function with Credential Provider, it must be possible to start and stop this VPN connection using a command-line program. When the OTP method is implemented, the VPN command-line connect command must launch an interface where the OTP can be manually input by the end user. On the other hand, if using static credentials, the Credential Provider supports dynamically substituting two values — a “username” and a “password” — into the connect and disconnect command lines. Where used, these values are stored encrypted within the Windows registry.
An application-level VPN user account must be provisioned for exclusive use by the Bravura Pass client components. (This should normally be distinct from any VPN accounts assigned to individual end-users.)
One or more VPN endpoints should be setup:
These should be setup in perimeter networks ("DMZs").
If using a static password for the VPN credential, then VPN connections should terminate in a perimeter network ("DMZ") rather than the main, corporate network.
They must honor the above "application-level" VPN user credentials.
The VPN endpoints should be configured with network address/port access control list restrictions.
The VPN endpoints must also be configured to issue IP addresses to the connecting systems from a dedicated pool of IP addresses. This is needed as a part of a larger mechanism that will ensure that connecting VPN clients use the correct AD domain controllers.
Bravura Security only tests the Cisco AnyConnect VPN client with product feature integrations. It is the only officially supported VPN client integration with Bravura Security products. Other VPN clients may work, but Bravura Security does not test nor officially support them.
As the user’s personal VPN credentials may include the forgotten password, VPN authentication for SSA cannot include this password. There are two alternatives for SSA VPN authentication:
Authenticate the VPN using the end-user’s pre-existing OTP credential. For example, RSA SecurID or similar. There is less need to restrict VPN network access in this case.
Use a static password known to the credential provider software, but not to any human. Connections made using this password should be severely restricted. There may be one password per device, one shared password for all devices, or one password per group of devices.
For added security, follow these best practices when choosing to create a special VPN account with a static password that Login Assistant will use to connect to the network and update locally-cached passwords when users are off-site.
Presuming that the VPN service you use is capable of this, apply the following limits to this account on the VPN server side:
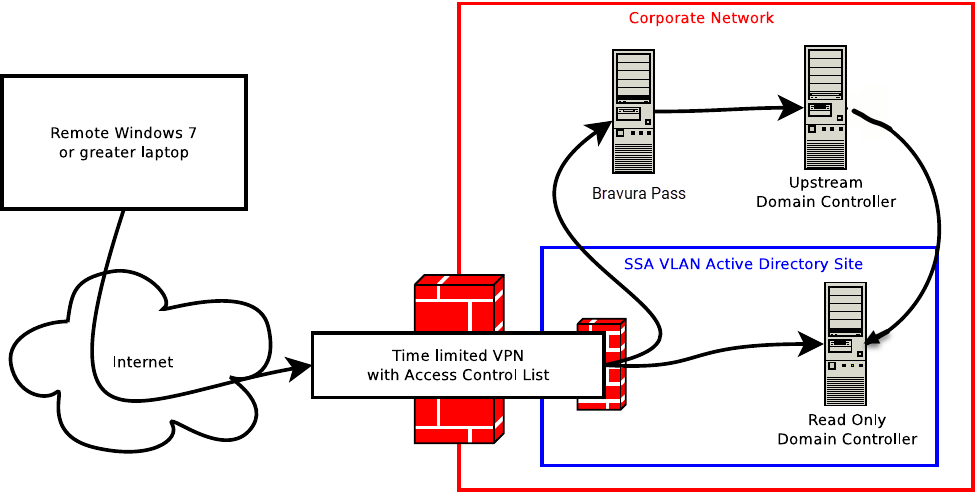
Create a new, dedicated read-only AD domain controller (DC), which will be used by Local Reset Extension.
Configure Bravura Pass to always push new AD password resets to the read/write DC along with any others.
Configure the VPN user to only be able to access:
The IP of this DC (all TCP ports).
The HTTPS URL of Bravura Pass – typically via a load balancer.
Set a connection timeout on the VPN user to 10 minutes.
Disable intruder lockouts on the VPN user, to minimize the potential for a denial-of-service attack on user access to self-service.
Active Directory requirements
Some Active Directory configuration is required for SSA to function properly. As a result, it is necessary to take steps to ensure that connecting SSA clients will use one of the specially-configured DCs for their login server.
A dedicated AD "site" must be provisioned.
One or more read-only domain controllers (RODCs) should be assigned to the AD site mentioned above.
These RODCs will also be deployed in the perimeter network(s) of the VPN endpoint(s).
This site will need to include an IP subnet to be defined below.
Ensure timely delivery of the new password to the RODC. (See Password propagation delays between DCs .)
The IP subnets from which the VPN clients will be assigned addresses must also be assigned to this site within AD.
One or more domain controllers must be provisioned, and assigned to the dedicated site.
All DCs in the dedicated site must be configured to use a fixed TCP port for NTDS and NetLogon RPC traffic.
The DCs must be deployed into the same network into which VPN clients connect, including if that ends up being a perimeter network ("DMZ").
For VPN connections that use a status password it is recommended to use read-only domain controllers.
Architectural considerations for deploying read-only domain controllers into a perimeter network is out of scope for this document. For information on perimeter network AD deployments, see http://technet.microsoft.com/en-us/library/dd728034(v=ws.10).aspx .
Microsoft provides some documentation for how to configure RPC dynamic port allocation and RPC to use certain ports and how to help secure those ports by using IPsec
Bravura Security does not believe port filtering is required between an RODC and its upstream, writable DC. Nonetheless organizations may port filter such traffic at their discretion and responsibility if they wish to do so.
Contact support@bravurasecurity.com for a more detailed document with a detailed breakdown of implementation tasks.
IP subnet requirements
When deploying Login Assistant, provision an IP subnet which:
Is used by the VPN endpoints as the IP address pool(s) offered to connecting VPN clients.
Can reach the RODCs mentioned above over the network.
Is assigned within the AD to the AD site mentioned above.
Can reach either the Bravura Pass server or a suitably configured reverse proxy by HTTPS.
The VPN endpoint, IP subnet and associated AD site should be provisioned within a perimeter network ("DMZ").