PIN sent via SMS or email
Authentication chains can be used in conjunction with the View and update profile (IDR) module to utilize mobile phones as part of the authentication process.
Best practice
PINs sent via SMS and usage of security questions are not recommended authentication methods as they are less secure methods.
Twilio-based SMS PIN delivery for authentication is also nearing end of life, see here for more information: https://www.twilio.com/en-us/changelog/notify-api-end-of-life-extension-notice .
It is instead recommended to use two-factor authentication such as with Bravura OneAuth authentication. See Add Bravura OneAuth authentication to Bravura Security Fabric for more information.
Usage of PINs sent via email is also an option as part of the authentication process as an alternative for SMS PINs.
Security considerations
SMS Security Limitations: SMS transmission may lack inherent security, as messages are transmitted in plain text from the SMS service provider to the recipient's device. However, most SMS service providers offer security over the Internet via TLS encryption from the sender's servers to theirs.
Integration with Secure Providers: Bravura Security Fabric provides access to published APIs of SMS service providers, allowing clients to integrate with reputable providers. This enables organizations to leverage the security features and authentication mechanisms offered by these providers to enhance the security of SMS notifications.
TLS Encryption: While SMS transmission may lack inherent security, the use of TLS encryption between servers can provide an additional layer of security, ensuring that messages are transmitted securely over the Internet.
Implementation
There are several Scenario components for sending one-time PINs, depending on the existing infrastructure the customer has, and the expected delivery method for the PIN.
If you have one or more email-to-SMS gateways, like the ones provided by various phone providers, use Scenario.hid_authchain_smspin_email
If you purchase a specific API-based SMS provider subscription, there are two other Scenario components provided with the base product install: hid_authchain_smspin_twilio and hid_authchain_smspin_celltrust
By default, a single SMS PIN method can be used in a specific integration, so the three Scenarios listed above are mutually exclusive, as noted in their manifest files.
There are two stages in the process: enrollment and authentication.
For enrollment, users provide their contact information by logging into the View and update profile (IDR) module and populating profile and request attributes for mobile phone provider and mobile phone number, and/or email address. Enrollment can be enforced by redirecting users to the View and update profile (IDR) module when they login.
For authentication, Bravura Security Fabric generates a random PIN and can either email it to the user via an email-to-SMS gateway or use an SMS Messaging Gateway such as the CellTrust SMS Gateway to send the SMS message. The user receives the SMS containing the PIN and types it into the Front-end to log in.
This case can be implemented in the following way:
The Email/SMS PIN module is configured as follows:
PIN delivery method: Email/SMS Gateway
Profile attribute specifying email/mobile phone number: A required, restricted-value profile and request attribute must be added for the users mobile phone number.
Profile attribute specifying mobile phone service provider: A required, restricted-value profile and request attribute must be added for the users mobile phone service provider.
The attributes must be configured with the Allow in authentication chains option enabled.
The Front-end is configured to enforce enrollment for the View and update profile (IDR) module.
User notification is configured to direct users to login and fill in their details.
When a user logs in:
The user is automatically directed to the View and update profile (IDR) module to fill in their details.
Other authentication options must be available.
The next time the user logs in, they can use the SMS/email PIN authentication module, which sends a PIN to their mobile phone or email address. They are required to enter the PIN before authentication can be granted.
Alternatively, users’ phone details could be populated from a data source such as an Active Directory account attribute.
For most implementations the email address is auto-populated from the source of profiles; users are not allowed to update the email value.
There is more than one way to implement this functionality. It can be deployed using the authchain_emailpin scenario component shipped with Bravura Security Fabric , as illustrated below.
Configure authentication via Email PIN
In this example, installing the hid_authchain_emailpin component modifies the Front-end login authentication chain to include a custom chain. This allows you to send a temporary PIN to a user’s email address as part of the authentication process. The user must enter the PIN within ten minutes of it being sent to authenticate.
The Front-end login authentication chain is configured with these settings:
Module | Control type |
|---|---|
Select chain ( | required |
Security questions ( | binding |
Click below to view a demonstration.
Log into Bravura Security Fabric as superuser .
Click Manage components > Scenario.
Select the checkbox for
Scenario.hid_authchain_emailpin.Click Install component(s) from the Actions panel on the right.
The component management program installs the component along with any dependencies. This may take some time depending on configuration requirements and dependencies. You should see ”Completed install for component” messages for each selected component in the TASK STATUS section of the Actions panel .
To test the addition of Email PIN authentication to the DEFAULT_LOGIN chain:
Log in to Bravura Security Fabric as an end user.
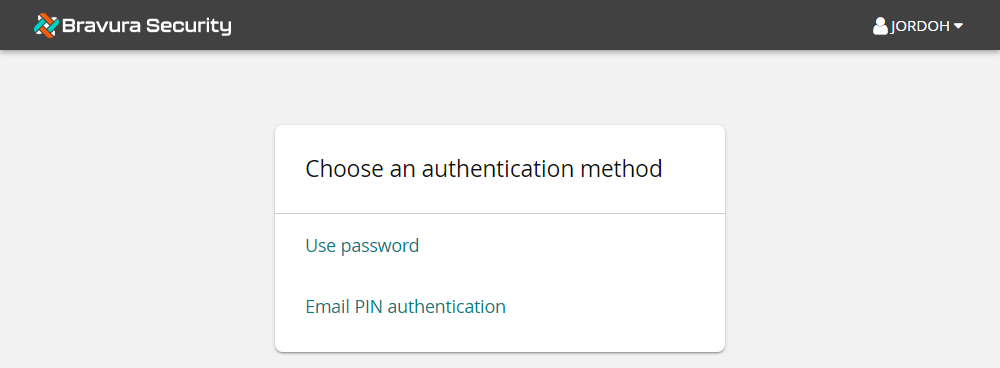
Click Email PIN authentication.
The page is displayed.
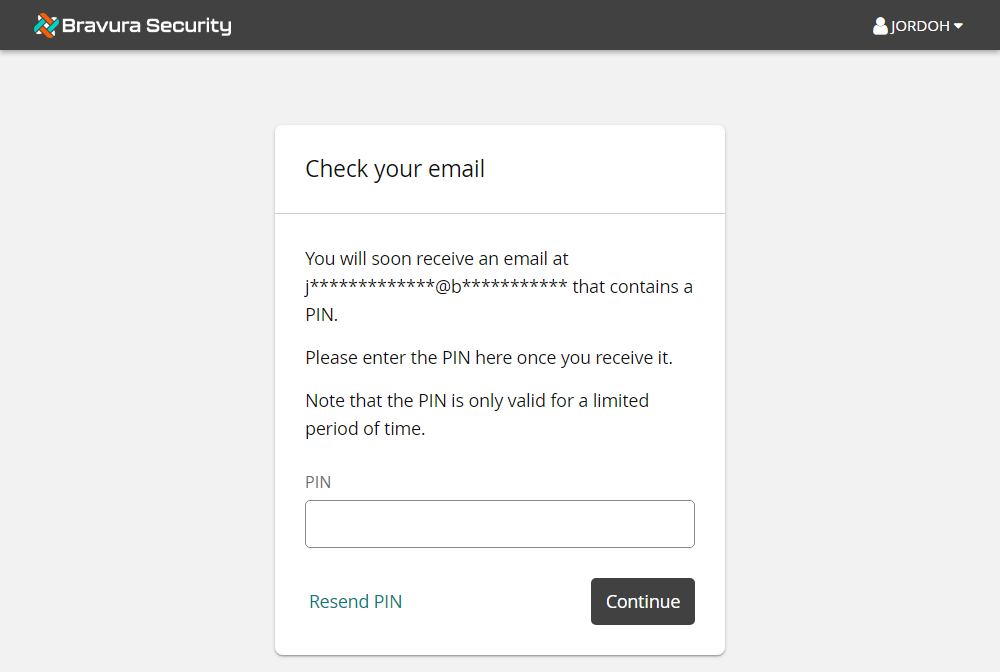
From the desktop, open Webmail.
Navigate to the Inbox and locate the "Your temporary PIN" message containing the user's email PIN.
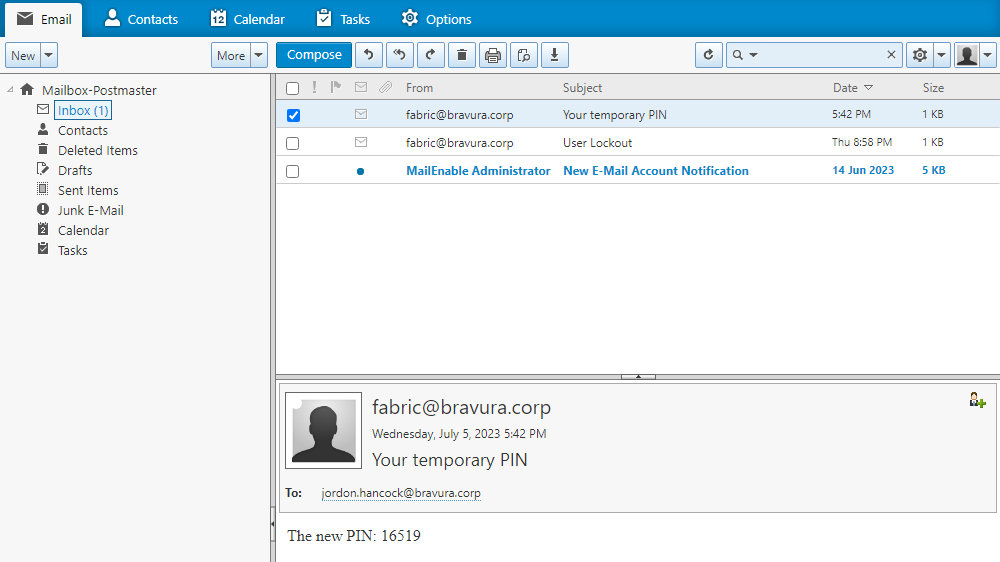
The body of the message contains the text ”The new PIN: <NNNNN>”.
In Bravura Security Fabric , enter the requested information and click Continue.
This module is a required control type. If you enter the incorrect response you will receive an error saying ”Invalid PIN”.
Once you have entered a correct PIN, you are then presented with two of the user’s security questions.
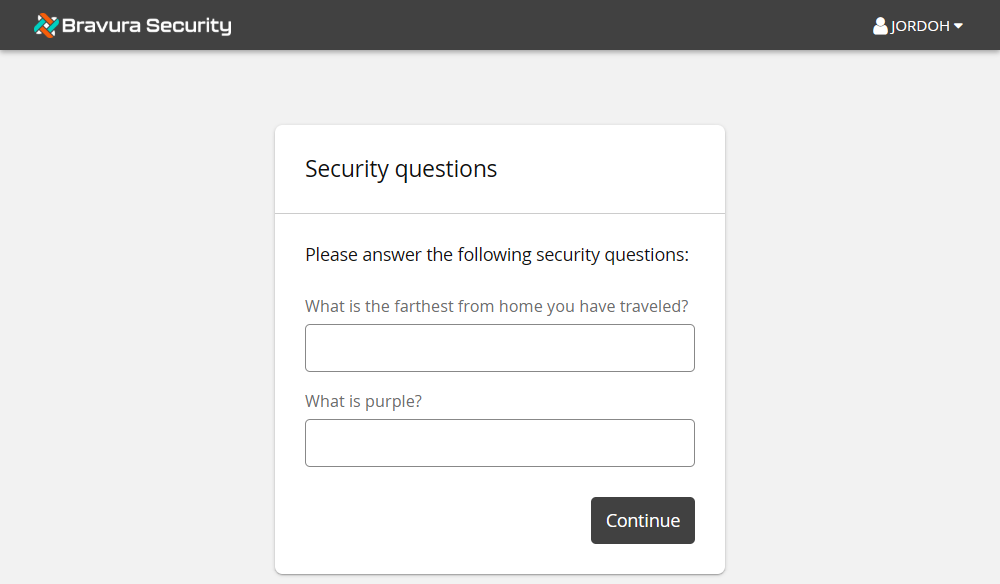
Answering the questions correctly will take you to the user’s home page.
If you are directed to the user's home page, you have completed the configuration correctly.
Configure authentication via SMS PIN
In this example, installing the hid_authchain_smspin_email component modifies the Front-end login authentication chain to include a custom chain . This allows you to send a temporary PIN via SMS text message as part of the authentication process. The component uses the mobile providers’ email-to-text gateways to send SMS texts to registered cell phones. Major US and Canadian providers are automatically onboarded; other providers must be added before users register the phone to be available.
This component is installed by default with Bravura Workforce Pattern. This example shows you how to modify external data settings to customize the component.
Log into Bravura Security Fabric as superuser.
Click Manage components > Refbuilds.
Select the checkbox for
RefBuild.im_corporate.Click Install component(s) from the Actions panel on the right.
The component management program installs the components along with any dependencies. This may take some time depending on configuration requirements and dependencies. You should see "Completed install for component" messages for each selected component in the Details section of the Actions panel.
When you install a component, the component management program creates the database tables, framework, and configurations that are necessary for the plugin points to function.
Review the settings by clicking Manage external data store > hid_global_configuration.
Verify the default settings for
Scenario.hid_authchain_smspin_emailare as below: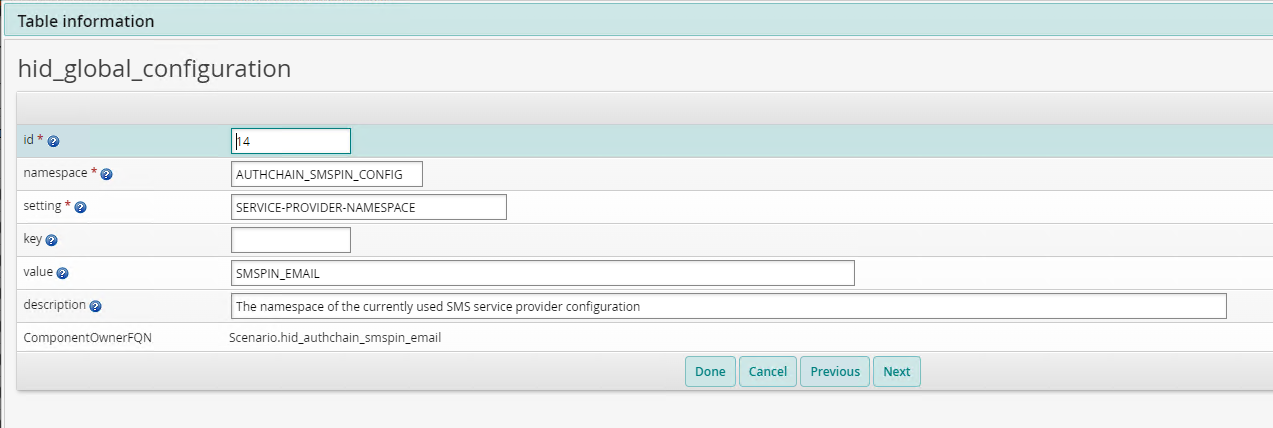
Populate or verify defaults in the external database namespaces for smspin and the SMS provider:
As superuser, navigate to the main menu and click Manage external data store.
Select
hid_global_configuration.Search in the table for something like "Value like '%SMSPIN_EMAIL%'".
Click the edit icon
 next to the empty row at the bottom of the table.
next to the empty row at the bottom of the table.Adjust the following values:
ID <id>
namespace <>
setting
key
value
description
Click Done to close the edit form.
Click Update.
The external data store (extdb) hid_global_configuration table contains the name of the profile attribute to be used to store users' phone numbers. Format the profile attribute to match the format expected by the SMS provider used.
Provide the data source for the cellphone attribute:
If a source target account attribute is available in an HR feed, Company Directory or some other target from where the cellphone number can be automatically imported, link that account attribute into the profile attribute defined in the external data store.
Consider granting the end-user access to edit that profile attribute, for example by adding it to the BASE_ATTRIBUTES profile attribute group .
Add a custom SMS/PIN scenario
There are many other such possible scenarios for sending a PIN via SMS or email that could be customized for an SMS/PIN provider that provides a REST API or some other form of WebApp integration.
If you have the necessary Python and web-service integration expertise, you can:
Copy the
hid_authchain_smspin_twilioScenario component from the component\Default\Scenario directory to component\Custom\Scenario.Copy the respective Functional component (
component\Default\Functional\hid_smspin_twilio) from Default to Custom.Rename the two components' directories to match the name of the new SMS ISP to integrate with; for example
Functional\hid_smspin_plivoandScenario\hid_authchain_smspin_plivo.Edit the two Custom components' files to match the requirements of the new integration.
For guidance from Bravura Security's Professional Services, contact your Account representative to request a service engagement.