Deployment
To allow the secure browser or web app privileged sign-on method to be used, install the following components in addition to the Bravura Privilege Pattern configuration:
Scenario.pam_webapp_management
Scenario.pam_webapp_social (optional)
This optional component includes website disclosure configurations for GMail, Facebook, and Twitter.
Scenario.pam_webapp_cloud_service (optional)
This optional component includes website disclosure configurations for Microsoft Azure and AWS IAM/root accounts.
Scenario.pam_webapp_cloud_computing (optional)
This optional component includes a website disclosure configuration for ServiceNow accounts.
For information about converting existing browser driver (pswxdom) configuration to JSON format that can be used for website disclosure configurations see pswxdom2webapp .
You can manually create a configuration file (JSON) if the website you want to access is not available with Bravura Security Fabric
The configuration file for the web app privileged sign-on disclosure requires a JSON file with the following structure:
{
"info": {
"url": "https://webpage/"
},
"username": {
"order": 1,
"type": "CSS",
"value": "input[name='session[username_or_email]']",
"input_value": "%username%",
"keypress_event": true,
"click": false,
"settle_time_before": 5,
"settle_time_after": 0,
"stop_on_fail": false
},
"password": {
"order": 2,
"type": "CSS",
"value": "input[name='session[password]']",
"input_value": "%password%" ,
"keypress_event": true,
"click": false,
"settle_time_before": 0,
"settle_time_after": 0,
"stop_on_fail": false
},
"submit": {
"order": 3,
"type": "CSS",
"value": "[role='button'][type='submit']",
"input_value": "" ,
"keypress_event": false,
"click": true,
"settle_time_before": 0,
"settle_time_after": 0,
"stop_on_fail": false
}Where:
"Info"["url"]is the url the web app will open the webpage on."username","password ", and"submit"action keys with a structure which determines how the browser will interact with the webpage.You can have as many action keys as needed to interact with the webpage tab
"order"order number the browser extension will act on."type"the search method the browser extension will use to find an element that matches "value" on the webpage. The supported types are:"XPATH": find an element using XPATH that matches the "value"
"CSS": find an element using CSS that matches the "value"
"ID": find an element with "id" that matches the "value"
"NAME": find the first element with "name" that matches the "value"
"CLASS": find the first element with the class that matches the "value"
"value"browser extension will use to look the webpage by "type"."input_value"the value we will look for in the search to identify the input field."keypress_event"a flag that is required, but not yet used."click"a flag that determines if the browser extension will click on the "input_value" element."settle_time_before"the time in seconds the browser extension waits before accessing this element."settle_time_after"the time in seconds the browser extension waits after accessing this element."stop_on_fail"a flag that stops the continued execution if the browser extension fails to find the element set by "value".
Sample configuration file for web app privileged sign-on (twitter.json)
{
"info": {
"url": "https://twitter.com/i/flow/login"
},
"username": {
"order": 1,
"type": "XPATH",
"value": "//span[contains(text(),'email')]/ancestor::label//*/input",
"input_value": "%username%",
"keypress_event": true,
"click": false,
"settle_time_before": 5,
"settle_time_after": 0,
"stop_on_fail": false
},
"next": {
"order": 2,
"type": "XPATH",
"value": "//div[@role='button']//*/span[text()='Next']",
"input_value": "",
"keypress_event": false,
"click": true,
"settle_time_before": 5,
"settle_time_after": 0,
"stop_on_fail": false
},
"password": {
"order": 3,
"type": "XPATH",
"value": "//input[@name='password']",
"input_value": "%password%" ,
"keypress_event": true,
"click": false,
"settle_time_before": 5,
"settle_time_after": 0,
"stop_on_fail": false
},
"submit": {
"order": 4,
"type": "XPATH",
"value": "//div[@role='button']//*/span[text()='Log in']",
"input_value": "" ,
"keypress_event": false,
"click": true,
"settle_time_before": 2,
"settle_time_after": 0,
"stop_on_fail": false
}
}Sample website disclosure configuration (JSON) for AWS
{
"info": {
"url": "https://console.aws.amazon.com"
},
"root_user": {
"order": 1,
"type": "CSS",
"value": "input#root_user_radio_button",
"input_value": "",
"keypress_event": false,
"click": true,
"settle_time_before": 5,
"settle_time_after": 0,
"stop_on_fail": false
},{
"info": {
"url": "https://login.live.com/"
},
"username": {
"order": 1,
"type": "CSS",
"value": "input[type='email']",
"input_value": "%username%",
"keypress_event": false,
"click": false,
"settle_time_before": 5,
"settle_time_after": 5,
"stop_on_fail": false
},
"next": {
"order": 2,
"type": "CSS",
"value": "input[type='submit']",
"input_value": "",
"keypress_event": false,
"click": true,
"settle_time_before": 0,
"settle_time_after": 3,
"stop_on_fail": false
},
"password": {
"order": 3,
"type": "CSS",
"value": "input[name='passwd']",
"input_value": "%password%" ,
"keypress_event": true,
"click": false,
"settle_time_before": 0,
"settle_time_after": 0,
"stop_on_fail": false
},
"passwordNext": {
"order": 4,
"type": "CSS",
"value": "input[type='submit']",
"input_value": "" ,
"keypress_event": false,
"click": true,
"settle_time_before": 0,
"settle_time_after": 0,
"stop_on_fail": false
}Example: Install optional scenarios
Log in to the front-end as superuser.
From the main menu click Manage components.
Search and select the checkbox for the following optional scenarios:
Scenario.pam_webapp_social
Scenario.pam_webapp_cloud_computing
Scenario.pam_webapp_cloud_service
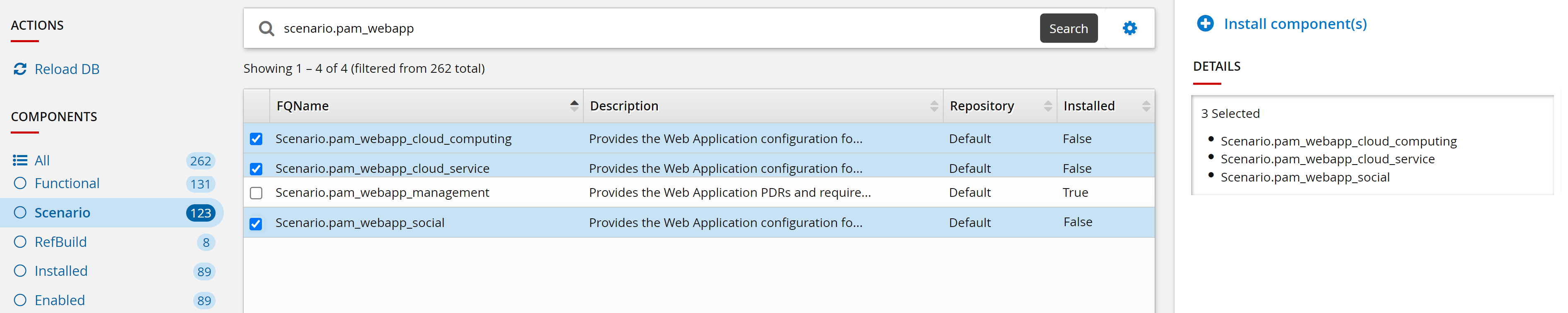
Click Install component(s).
The panel on the right will indicate when the installation is complete.
These optional scenarios include website disclosure configurations for the following:
GMail
Facebook
Twitter
Microsoft Azure
AWS IAM/root accounts
ServiceNow
Example: View the optional website disclosure configurations
This example assumes that:
Scenario.pam_webapp_management is installed
Scenario.pam_webapp_social is installed
Scenario.pam_webapp_cloud_computing is installed
Scenario.pam_webapp_cloud_service is installed
A web application administrator has been added to the PAM_TEAM_ADMINS user class, thus has the privilege to configure website disclosure configurations
To view the website disclosure configurations installed by these three scenarios:
Log in to Bravura Security Fabric as a web application administrator.
Click Manage Resources.
Click Website Disclosure Configuration: Update.
Click Select a website disclosure configuration.
The configurations installed by the three scenarios are available.
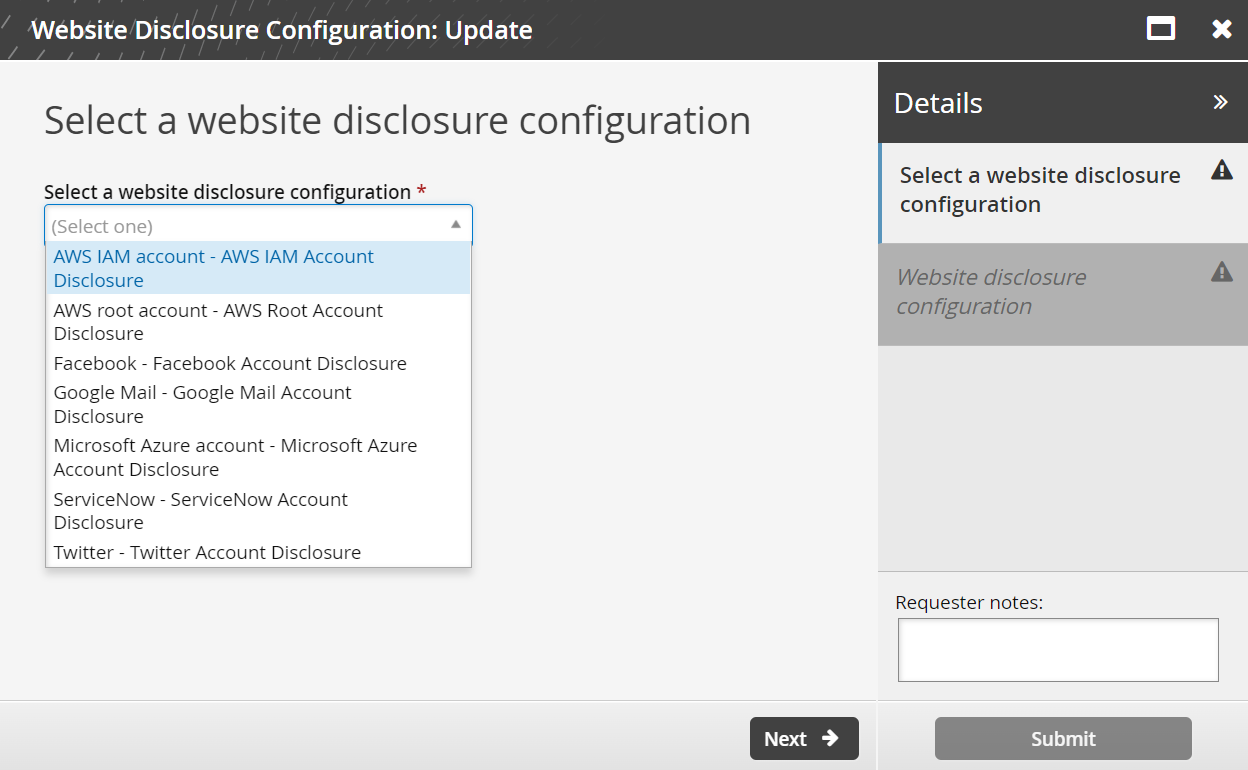
Close the Update wizard.
or
Edit the website disclosure configuration:
Select one of the website disclosure configurations and click Next .
Change the website disclosure configuration name, description, or configuration file as needed.
Click Submit.